> Enabling Two-Factor Authentication on Pulse Connect Secure SSL VPN
Enabling Two-Factor Authentication on Pulse Connect Secure SSL VPN
This guide shows how to enable multi-factor authentication (2FA / MFA) for users logging in to Pulse Connect Secure SSL VPN with the help of the Protectimus two-factor authentication solution for Pulse Connect Secure SSL VPN.
Protectimus’s two-factor authentication system integrates with Pulse Connect Secure SSL VPN via RADIUS authentication protocol.
In this scenario, the Protectimus Cloud 2FA Service or On-Premise 2FA Platform performs as a RADIUS server, and the Pulse Connect Secure SSL VPN takes the role of a RADIUS client.
You will find the scheme of work of the Protectimus solution for Pulse Connect Secure SSL VPN two-factor authentication below.
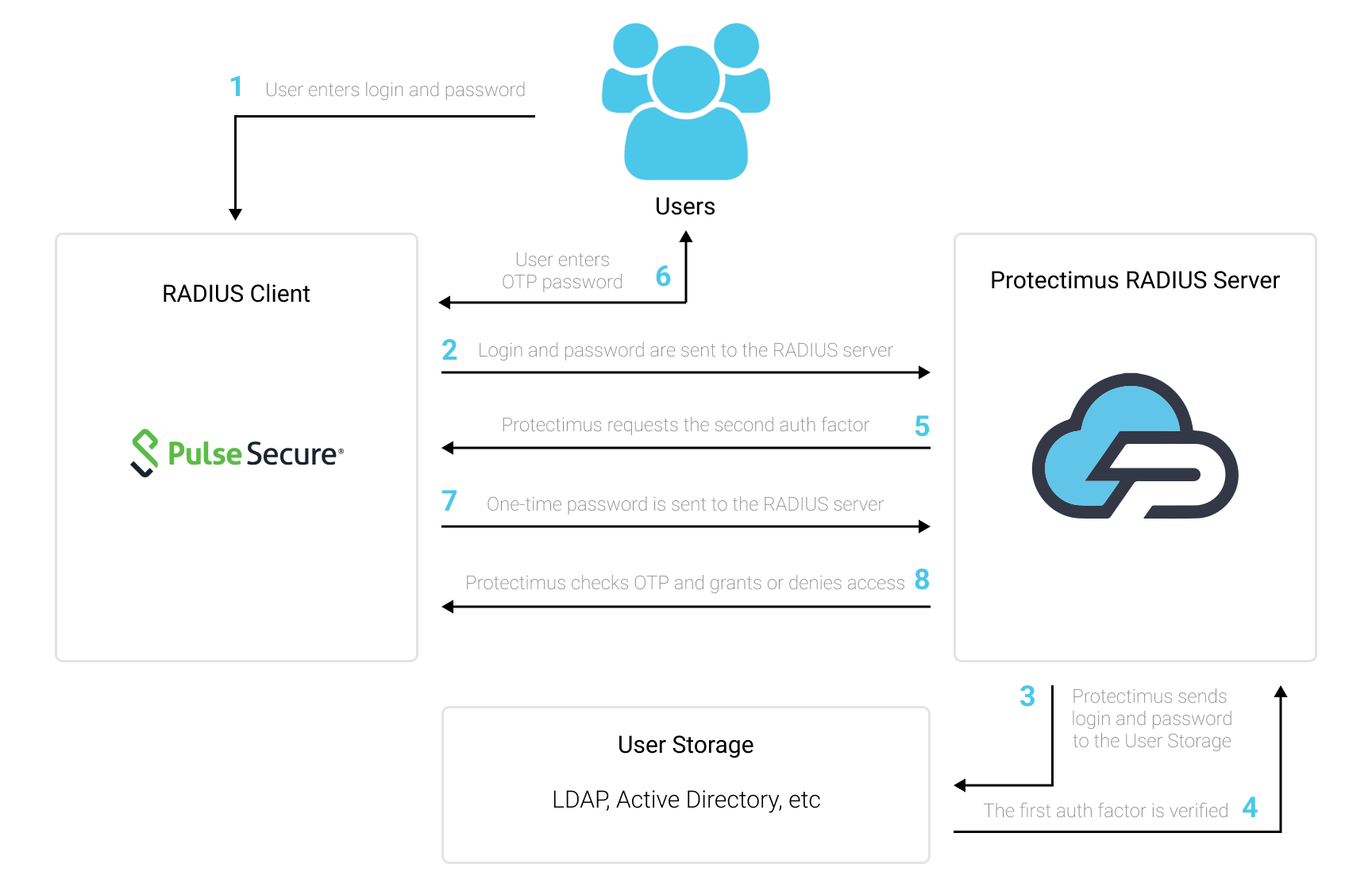
1. How 2FA for Pulse Connect Secure SSL VPN Works
Two-factor authentication (2FA / MFA) protects the Pulse Connect Secure SSL VPN user accounts from phishing, brute force, keyloggers, man-in-the-middle attacks, data spoofing, social engineering, and other similar hacking tricks.When you enable 2FA/MFA for Pulse Connect Secure SSL VPN, Pulse Secure VPN users will use two different authentication factors to get access to their accounts.
- The first factor is username and password (something they know);
- The second factor is a one-time password generated with the help of a hardware OTP token or a 2FA app (something they own).
To hack a Pulse Connect Secure SSL VPN user account protected with two-factor authentication, a hacker needs both passwords at once. Moreover, a hacker has only 30 seconds to crack and use a time-based one-time password. It is almost impossible to fulfill these conditions, which makes two-factor authentication so effective.
2. How to Enable 2FA for Pulse Connect Secure SSL VPN
You can set up two-factor authentication (2FA) for Pulse Connect Secure SSL VPN with Protectimus using the RADIUS protocol:
- Get registered with Protectimus SAAS Service or install the On-Premise 2FA Platform and configure basic settings.
- Install and configure Protectimus RADIUS Server.
- Configure Pulse Connect Secure SSL VPN authentication policies.
2.1. Get Registered and Configure Basic Protectimus Settings
- Register with the Protectimus Cloud Service and activate API or install the Protectimus On-Premise Platform (if you install Protectimus Platform on Windows, check the RProxy box during the installation).
- Add Resource.
- Add Users.
- Add Tokens or activate Users’ Self Service Portal.
- Assign Tokens to Users.
- Assign Tokens with Users to the Resource.
2.2. Install and Configure Protectimus RADIUS Server
Detailed instructions for installing and configuring the Protectimus RADIUS Server for Pulse Connect Secure SSL VPN 2-factor authentication using RADIUS are available here.2.3. Add Protectimus as RADIUS Server for Pulse Connect Secure SSL VPN
- Log into the Pulse Secure administration panel.
- Navigate to Authentication –> Auth. Servers.
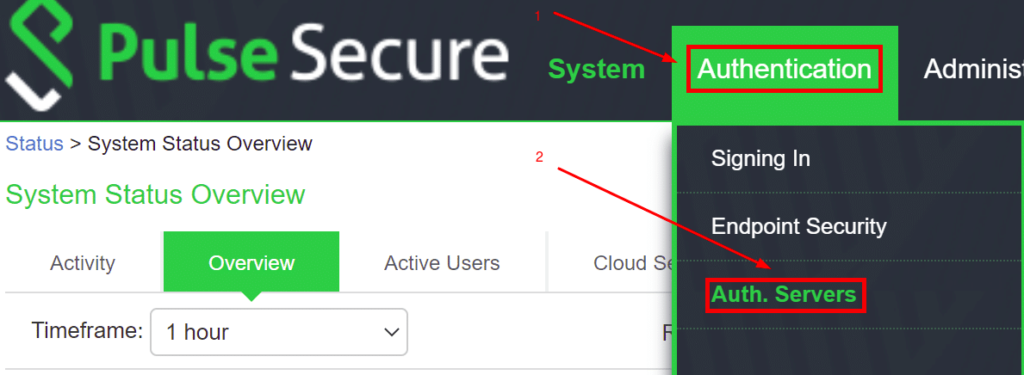
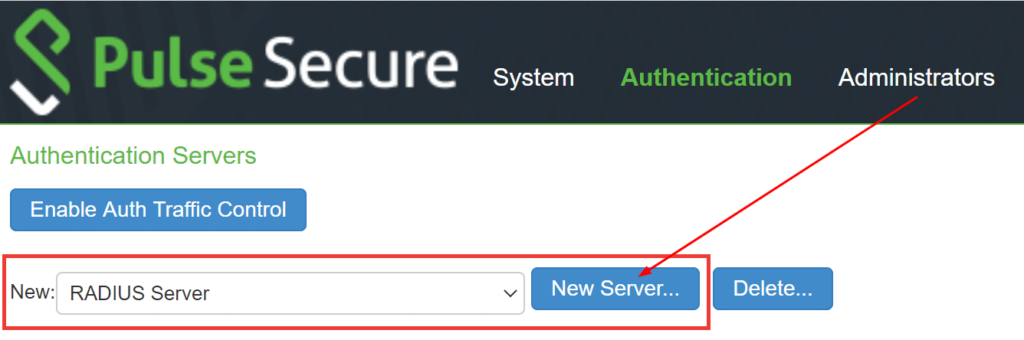
- Select RADIUS Server in the dropdown, and click New Server….
- Fill in the required fields in the Settings tab. Please refer to the following table and image.
| Name | Come up with a name for your RADIUS server, e.g. Protectimus Server. |
| RADIUS Server | Enter the IP of server where the Protectimus RADIUS Server component is installed. |
| Authentication Port | Indicate 1812 (or whichever port you configured in the Protectimus radius.yml file when configuring Protectimus RADIUS Server). |
| Shared Secret | Indicate the shared secret you created in the Protectimus radius.yml file (radius.secret property) when configuring Protectimus RADIUS Server |
| Timeout | Set to 180 seconds. |
| Retries | Set to 3. |
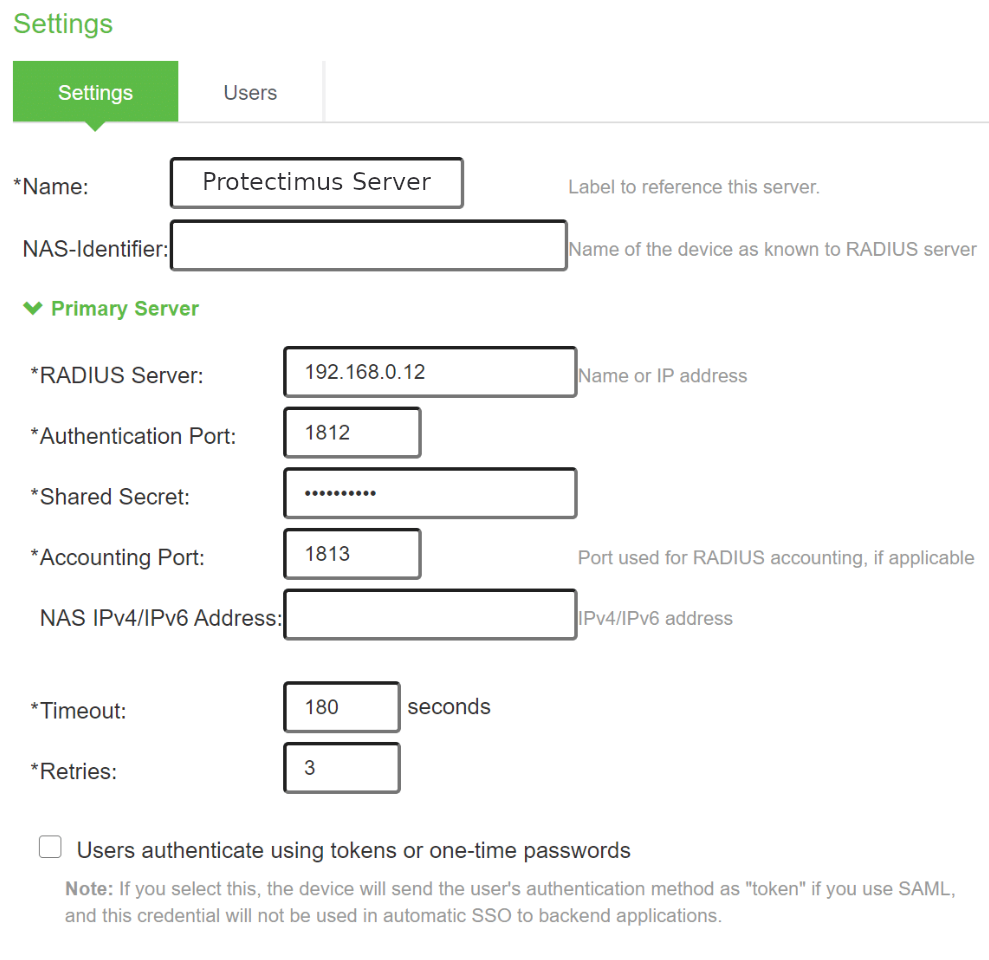
- Keep default values of all other fields and click Save Changes.
- Navigate to Users –> User Realms –> New User Realm….
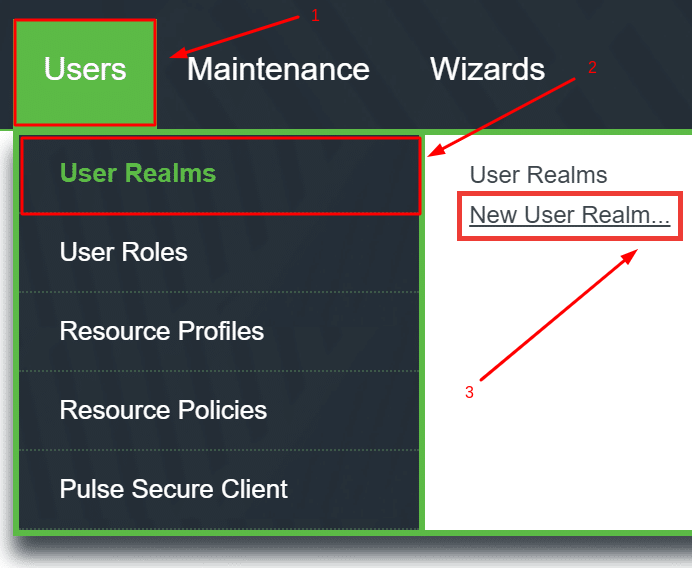
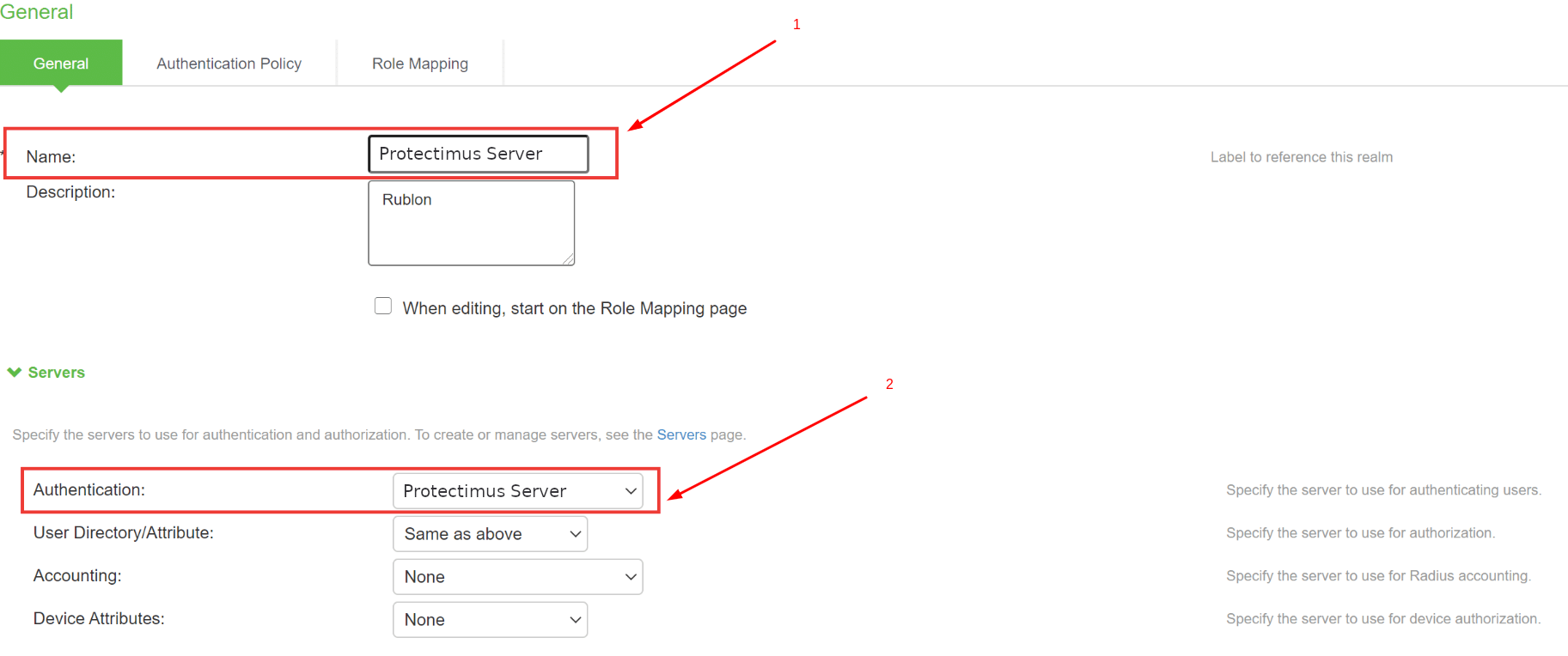
- Come up with a Name for your new realm, e.g. Protectimus Server.
- Select the previously created authentication server (Protectimus Server) in the Authentication dropdown.
- Click Save Changes.
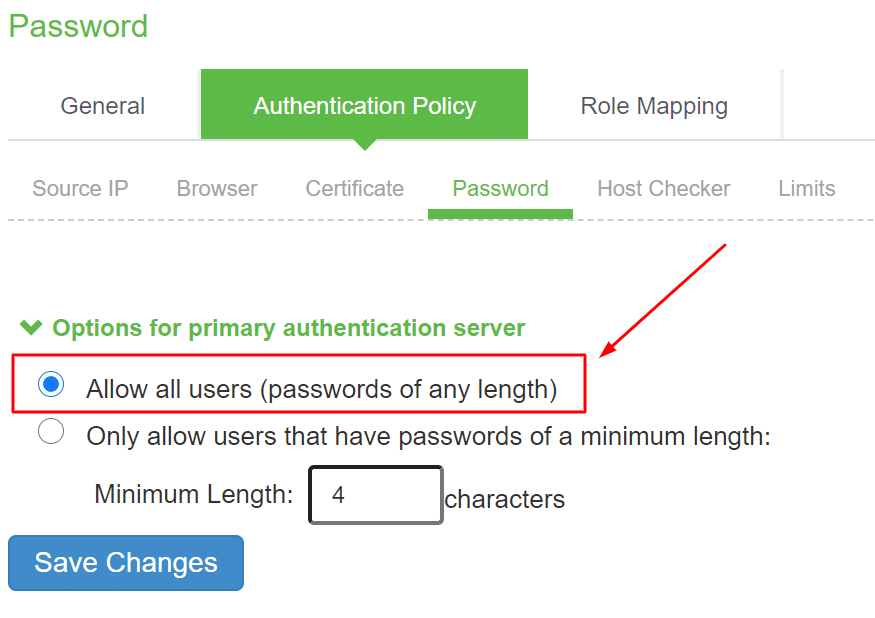
- Navigate to Authentication Policy –> Password.
- Select Allow all users (passwords of any length) and click Save Changes.
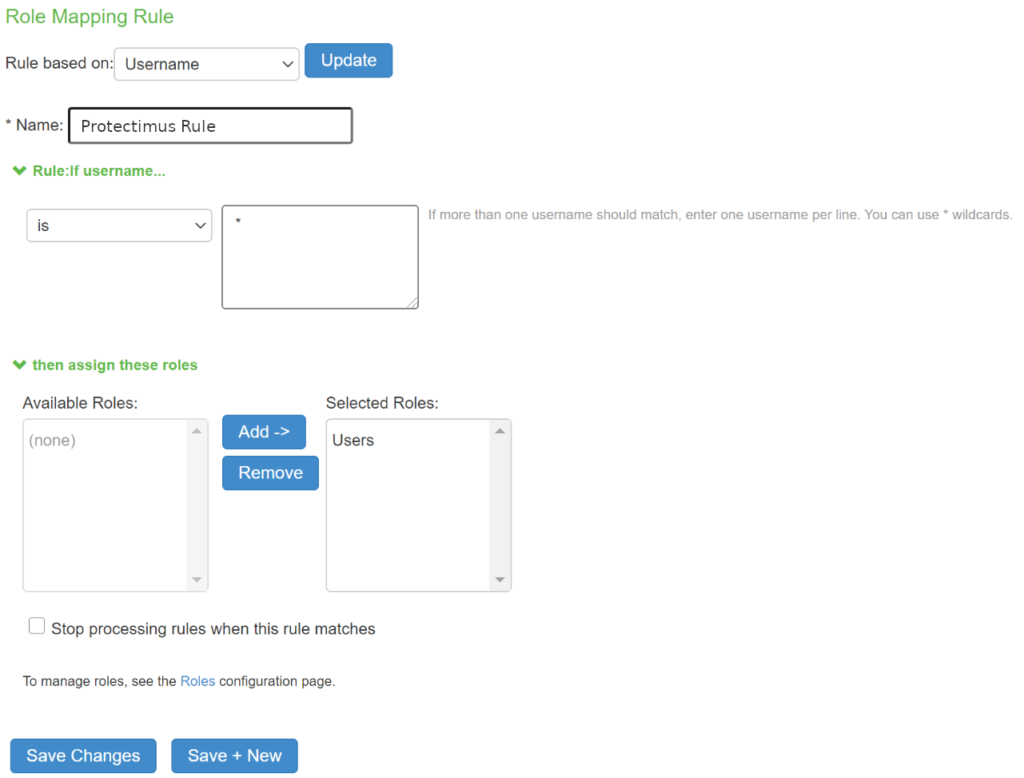
- Go to the Role Mapping tab and click New Rule….
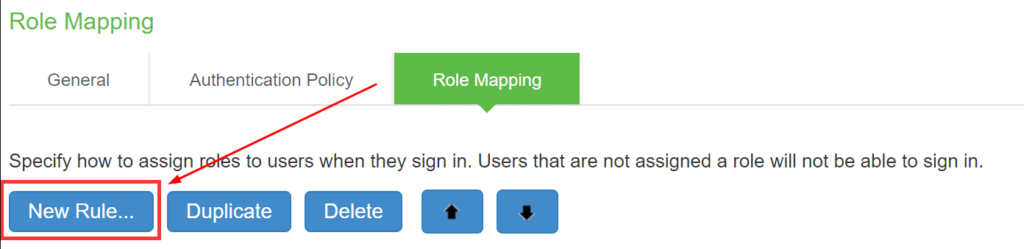
- Come up with the name for a new rule, e.g. Protectimus Rule.
- Set Rule:If username… to is *.
- Assign a Users role. Select Users on the Available Roles list and click Add –>.
- Click Save Changes.
- Navigate to Authentication –> Signing In –> Sign-in Policies.
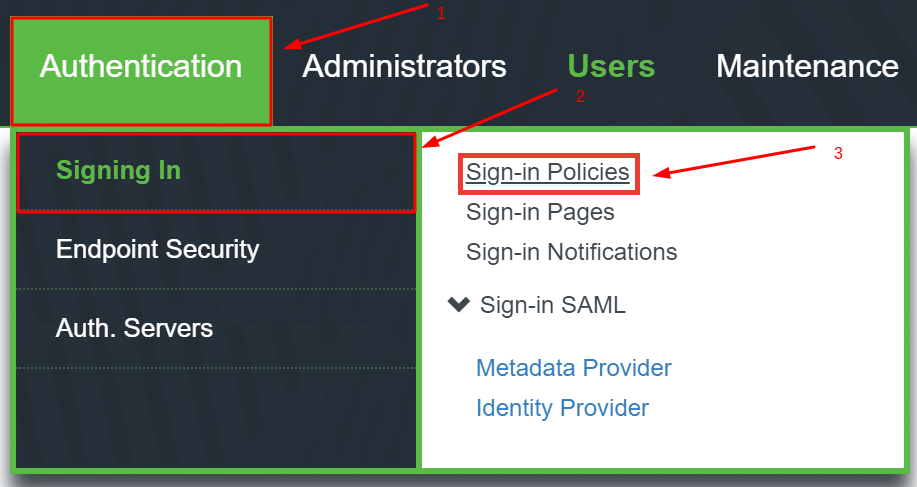
- Click the */ URL in the User URLs table.
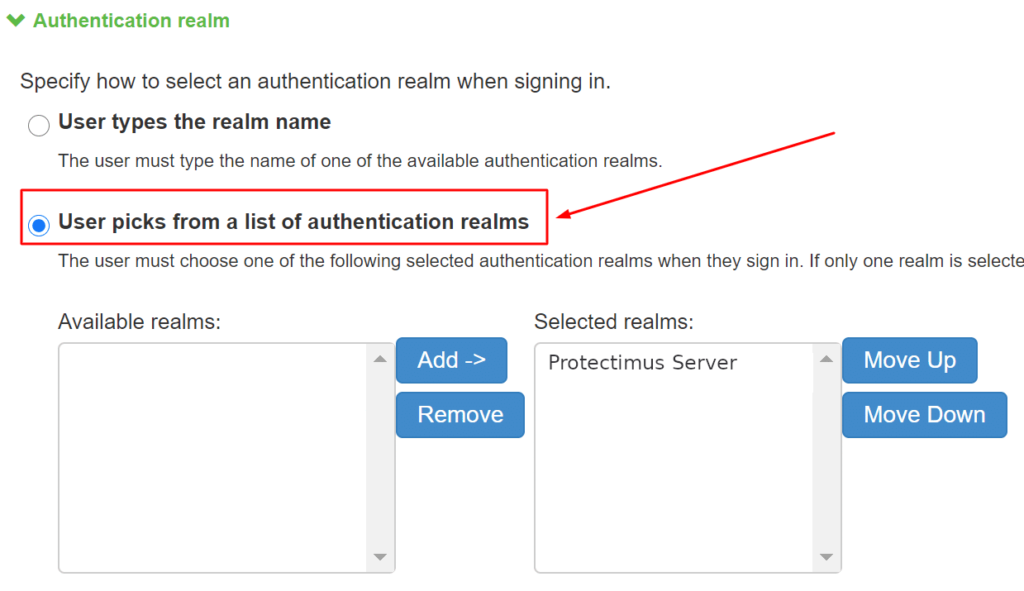
- Select User picks from a list of authentication realms and select the Protectimus Server realm you have created before. To do this, just select Protectimus Server on the Available realms list and click Add –>.
- Click Save Changes.
Integration of multi-factor authentication for Pulse Connect Secure SSL VPN is now complete. If you have other questions, contact Protectimus customer support service.
