- 1. What is Multi-Factor Authentication (MFA)
- 2. Factors of Multi-Factor Authentication
- 3. How Multi-Factor Authentication Works
- 4. The Significance of Multi-Factor Authentication
- 5. What Threats Does MFA Protects From
- 6. Examples of Multi-Factor Authentication
- 7. Methods of Multi-Factor Authentication
- 8. Implementing MFA in Organizations
- 9. What Industries Use MFA
- 10. Frequently Asked Questions About 2FA
- 11. How-To’s for Protectimus Users
1. What is Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA, 3FA) adds an extra layer of security to your account, ensuring it’s really you when you log in. Instead of just entering your password, the system might ask for additional proof, such as a one-time code sent to your phone via MFA app, chatbot, push notification, SMS, or email. Or, you may need to answer a secret question, scan your fingerprint, or use the face ID feature.
This robust defense helps protect users’ accounts against cyber attacks and tricky situations where passwords might be at risk. Multi-factor authentication guards against phishing, man-in-the-middle attacks, brute force, and other password-related threats.
Multi-Factor Authentication is also referred to as two-factor authentication, 2-factor authentication, or 2FA. This is because, typically, a combination of two authentication factors is used during login to enhance user-friendliness.
2. Factors of Multi-Factor Authentication
Multi-factor authentication enhances security by requiring a combination of different authentication factors.
Currently, three main types of authentication factors are recognized:
- 1. Something you know: This includes passwords, usernames, or responses to secret questions like the name of your cat or your favorite author.
- 2. Something you have: A one-time code generated on your smartphone through an MFA app or received via SMS, chatbot in a messaging app, or email. Or, it can be a special device for one-time password generation called hardware OTP token. It resembles a key fob, USB drive, card, or calculator with a small 6 or 8-digit screen.
- 3. Something you are: Biometric data, such as fingerprint or retina scans, as well as face ID.
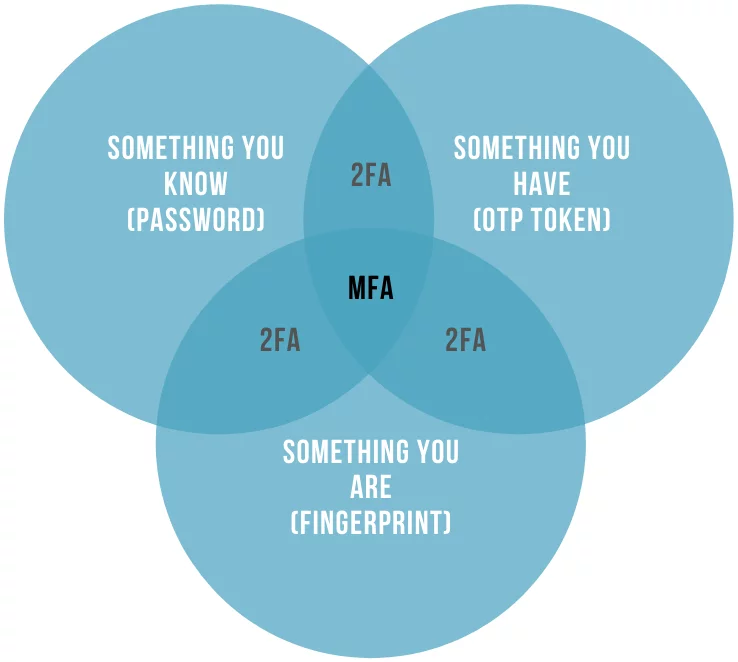
Some security specialists mention a potential fourth factor – the user’s environment. Yet, there is ongoing debate about whether it’s appropriate to classify the user’s environment as a distinct factor. Nevertheless, within the realm of multi-factor authentication, we can delineate two additional factors:
- 4. Location Verification: Location-based authentication validates a user’s identity by considering their geographical location. For example, if an account registered in one country encounters login attempts from another location, the system, employing geographic and IP filters, will restrict access to the account.
- 5. Time-Based Authentication: This factor verifies a user’s identity by evaluating the timing of access attempts. It operates on the assumption that specific activities, such as logging into a work computer, typically occur within predictable time ranges. If an access attempt deviates from the expected timeframe, the system will deny access to the account.
3. How Multi-Factor Authentication Works
Signing into your account with just a username and password may seem simple, but it opens the door for anyone with this information to access your account from anywhere globally. This is where Multi-Factor Authentication (MFA) steps in to add an extra layer of security.
The success of multi-factor authentication lies in the strategic combination of various authentication factors, each compensating for the weaknesses of the other. This makes it tough for attackers since compromising all factors at once within a limited time is challenging. Even if one factor is compromised, the account stays secure, providing robust protection.
When MFA is enabled, the authentication process becomes more intriguing.
- 1. The first step is the usual username and password routine (something you know).
- 2. Then, you encounter the second factor—a unique identity verification step, which may be:
- • Something you have: a one-time code generated on your smartphone through an MFA app or received via SMS, etc.
- • Something you are: a fingerprint or face ID.
Let’s say you choose the Protectimus Smart authenticator app as your second factor. Opening the MFA app on your smartphone reveals a dynamically generated 6-digit number. Inputting this number into the site grants you access.
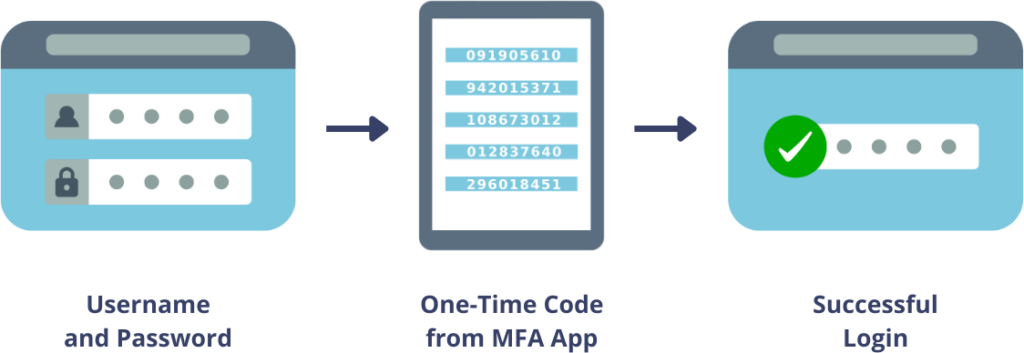
Now, if someone attempts to log in as you, they hit a roadblock. Even if they know your username and password, they’re stuck at the second factor. Without your smartphone, they can’t obtain the changing 6-digit code. This code, refreshed every 30 seconds, ensures security, even if they somehow knew yesterday’s code.
Breakdown of the MFA process:
- 1. Registration: Users create an account with a username and password, linking additional items such as a cell phone, physical hardware fob, or virtual items like an email address or mobile number. Biometric information, like fingerprints, can also be added for enhanced security.
- 2. Authentication: MFA-enabled users logging into a website input their username and password (the first factor) and are prompted to enter one-time codes or perform other actions from their MFA device (the second factor).
- 3. Reaction: Users complete the authentication by entering a one-time code, pressing a button on a hardware device, scanning their fingerprint, or clicking on the push notification.
4. The Significance of Multi-Factor Authentication
As organizations transition into the digital age and take on greater responsibility for safeguarding customer data, the need for robust security measures, including the adoption of multi-factor authentication (MFA), becomes apparent.
Relying on usernames and passwords, prove unreliable and susceptible to exploitation. Users often struggle to manage credentials, leaving them vulnerable to hacking.

MFA is a vital solution, adding an extra layer of verification to online accounts and reducing the risk of unauthorized access due to compromised passwords. Multi-factor authentication protects accounts from phishing, man-in-the-middle attacks, brute force attempts, credential stuffing, keyloggers, and other password-related attacks.
Certifications and compliance mandates emphasize the importance of MFA. It plays a crucial role in meeting stringent requirements like PCI-DSS, PSD2, GDPR, NIST, FFIEC, NYDFS, NAIC, and other security standards. For businesses and organizations dealing with confidential data, financial transactions, or personal user information, implementing MFA is particularly crucial.
In essence, MFA strengthens digital security, aligns with industry standards, and provides a resilient defense against evolving cyber threats. It stands as an indispensable component in the ongoing battle against digital risks.
5. What Threats Does Multi-Factor Authentication Protects From
Multi-Factor Authentication (MFA) stands as a robust security shield, safeguarding user accounts against a variety of cyber threats. It provides protection against brute force attacks, account takeovers, phishing, man-in-the-middle attacks, credential stuffing, session hijacking, social engineering, dictionary attacks, keyloggers, and other password-related threats.
Phishing Attacks
MFA plays a crucial role in defending against phishing attacks where hackers trick users into disclosing login credentials through deceptive emails or fake websites. Requiring a second form of authentication adds an extra layer of security, diminishing the effectiveness of phishing schemes.
Brute Force Attacks
MFA addresses the risk of brute-force attacks, where hackers systematically attempt to crack passwords by trying numerous combinations. The additional authentication factor makes it significantly more challenging for attackers to gain unauthorized access, even if they manage to decipher a password.
Keylogging Exploits
MFA protects against keylogging attacks, where malicious software records keystrokes to capture sensitive information like passwords. Introducing an additional layer of authentication, such as a one-time code or biometrics, renders keyloggers ineffective in gaining complete access to user accounts.
Credential Stuffing
MFA disrupts credential stuffing attacks, where hackers use leaked username and password pairs to gain unauthorized entry. The secondary authentication requirement renders stolen credentials insufficient, fortifying digital systems against automated login attempts.
Session Hijacking
MFA guards against session hijacking, a type of attack where hackers steal an active user session for unauthorized access. Even if an attacker captures session data, the secondary authentication factor adds an extra layer of security, preventing successful compromise.
Social Engineering Attacks
MFA acts as a safeguard against social engineering attacks, where attackers manipulate individuals into divulging confidential information. Even if an attacker convinces a user to share login credentials, the secondary authentication factor adds an additional barrier to unauthorized access.
Man-in-the-Middle (MitM) Attacks
MFA helps prevent MitM attacks, where attackers intercept and manipulate communication to gain access to sensitive information. Additional verification steps, especially when utilizing CWYS feature for data signing, make it challenging for attackers to manipulate or intercept the authentication process.
Compromised Passwords
Passwords pose a risk when acquired by unauthorized individuals. For example, if a user records their password on a physical notepad, it becomes susceptible to theft, enabling unauthorized access. In contrast, 2FA enhances security by requiring validation from a secondary device after entering a password.
6. Examples of Multi-Factor Authentication
Discover how businesses are using Multi-Factor Authentication (MFA) in real-life scenarios. We’ll explore practical examples that showcase how organizations across different industries have successfully implemented MFA:
Tailored Security Rules for Different User Groups at Volet
Volet uses MFA to customize security for different user groups. Employees are limited to hardware 2FA tokens with geographic and IP filters. Meanwhile, Volet end users enjoy flexibility, letting them choose from hardware OTP tokens, 2FA apps, or 2FA chatbots on messaging platforms. Additionally, end-users’ transactions are further protected with the CWYS (Confirm What You See) data signing feature.
Protection for Corporate Infrastructure at Xchanging Italy
Xchanging Italy, part of DXC Technology, trusts Protectimus for widespread security. They use Protectimus’ 2FA solution to secure access to almost all enterprise software. The decision was driven by the need for efficient protection across all services, avoiding the complexities of integrating 2FA with each corporate software individually. The Protectimus Dynamic Strong Password Authentication (DSPA) solution integrates seamlessly with Active Directory. This transforms user passwords into dynamic two-factor passwords, combining a standard password with a temporary time-based one-time password (TOTP). The result is comprehensive security for connected services without the need for separate software installations on workers’ computers.
Enhancing Security for VPN and Email Access at SICIM
SICIM relies on two-factor authentication to boost security for corporate VPN access. Additionally, this 2FA protocol adds an extra layer of protection to employees’ corporate email boxes, ensuring heightened security for sensitive information.
7. Methods of Multi-Factor Authentication
Multi-Factor Authentication (MFA) significantly enhances digital security by requiring users to verify their identity through various methods. There are several approaches, each contributing uniquely to strengthen authentication processes. Below, we categorize these methods into different groups, shedding light on their distinctive features and applications.
Knowledge-based Authentication
Passwords: Despite their simplicity, passwords are commonly used in MFA solutions as the initial step of multi-factor authentication.
Security Questions: Traditional security questions are losing favor due to repetitive data entry. Dynamic security questions, relying on real-time data, offer a more secure and user-friendly alternative.
Hardware OTP Tokens
Classic Hardware OTP Tokens: Physical OTP tokens, resembling key fobs or cards with a small display and button, generate 6 or 8-digit temporary codes. Classic OTP tokens have hard-coded secret keys that cannot be replaced by the end user.
Programmable Hardware OTP Tokens: Physical devices, similar to key fobs or cards, generate temporary two-factor authentication codes. What sets programmable OTP tokens apart is their unique capability to be flashed with a new secret key. This flexibility is advantageous for businesses, offering the convenience of altering the secret key as required and ensuring enhanced security by avoiding key transfers.

U2F Standard: Combining USB or NFC tokens with an open-standard application, the U2F standard provides a straightforward way to add authentication factors to supporting platforms.
SMS Authentication
Text messages sent to trusted numbers, requiring interaction or a one-time code for identity verification. While SMS authentication is widely used, it is considered less secure than other MFA methods and may be susceptible to interception.
Two-Factor Authentication Apps
Mobile 2FA authentication apps like Protectimus SMART or Google Authenticator generate secure OTPs, providing a robust alternative to SMS.
Authentication via Chatbots in Messaging Apps
An innovative 2-factor authentication method introduces the use of MFA chatbots on widely-used messaging platforms such as Facebook Messenger, Telegram, and Viber for delivering one-time passwords (OTPs). This approach offers a solution to several critical issues: it provides heightened security compared to SMS authentication, is entirely cost-free, and offers user-friendly simplicity for both clients and their users.
Push-based 2FA
Enhancing security and ease of use, push-based 2FA combats phishing by replacing access codes with push notifications. Scalable for organizations, it requires data access on mobile devices.

Email Token Authentication
Email authentication is similar to SMS tokens, codes are sent via email, providing a backup method for users without immediate access to their phones. This approach ensures accessibility while maintaining security.
Inherent Authentication (Biometric Authentication)
Utilizing unique characteristics such as fingerprints or facial features, biometrics offer a secure and convenient MFA method. However, not all devices support this technology.
Location-based and Time-based Authentication
Location-based and time-based authentication methods, typically used in combination with two other authentication methods, add an extra layer of security:
- Geographic filters restrict access to accounts, permitting entry only from selected countries.
- IP filtering ensures access to accounts solely from specified IP addresses.
- Time filters grant access to accounts exclusively during designated business hours.
These MFA methods provide a layered defense against unauthorized access, addressing different user needs and security concerns. Organizations can choose the combination of methods that best aligns with their security requirements and user experience preferences.
8. Implementing Multi-Factor Authentication in Organizations
Implementing Multi-Factor Authentication (MFA) in organizations involves key best practices for optimal security:
- 1. Prioritize High-Value Accounts: Focus on securing critical accounts first, like those of top executives and network administrators, aligning with legal requirements and operational efficiency.
- 2. Select Practical MFA Solution: Choose a versatile 2-factor authentication service that supports various two-factor authentication methods. Consider cost-effectiveness, practicality, and criteria such as adaptability, user-friendliness, and ease of integration.
- 3. Choose a Reliable MFA Provider: Critical to success, select an MFA provider that is compatible with your needs, easy to implement, stable, and ready to help with the integration. Possibility of integration into existing IT frameworks is essential.
- 4. Educate End Users: Effectively communicate the importance of MFA to end users. Tailor explanations for employees, emphasizing the impact on products and profits. With clients, make MFA unobtrusive and consider incentives for voluntary adoption.
Remember, MFA is a valuable asset safeguarding business and personal data. Recognizing its benefits empowers organizations to make informed decisions and implement effective solutions promptly.
Explore further details on this topic in the article 5 Steps to Prepare Your Business for Multifactor Authentication.
9. What Industries Use MFA
From the financial realm to healthcare, education, online gaming, technology, government, and the expansive energy sector, MFA emerges as a crucial defense mechanism against unauthorized access and potential security threats. Let’s unravel the tailored implementations and benefits of MFA across these varied landscapes.

Financial Services
In the financial services sector, Multi-Factor Authentication (MFA) serves as a crucial shield against unauthorized access. Implementing 2FA, particularly with data signing features like Confirm What You See (CWYS), acts as a robust defense mechanism. This safeguards users’ accounts and shields financial transactions from phishing attacks, Man-in-the-Middle (MITM) threats, and data replacement attempts.

Education
Within educational institutions, two-factor authentication solutions and OTP tokens are widely adopted. These tools play a pivotal role in safeguarding the vast amount of sensitive data related to students and employees. The use of 2FA in universities, colleges, and schools acts as a barrier against unauthorized access, ensuring the protection of valuable educational information.

Healthcare
In the healthcare sector, where the protection of patient data is paramount, the application of 2FA services is instrumental. This goes beyond meeting compliance requirements such as HIPAA, PCI DSS, HITRUST, Joint Commission standards, and NIST standards. Secure access to patient and staff data in hospitals, along with the utilization of Protectimus hardware tokens for Electronic Visit Verification (EVV), ensures a robust defense against potential security breaches.

Online Gaming and Gambling
For platforms in online gaming, gambling, and sports betting, two-factor authentication is a key defense against fraud and credential stuffing. Most states’ regulations governing online gambling mandate iGaming platforms to implement multi-factor authentication for their users. By protecting user accounts with 2FA, these platforms enhance security and provide a safer environment for users, preventing unauthorized access and fraudulent activities.
Technology and Energy
Across various technological landscapes, industries rely on Multi-Factor Authentication to fortify their cybersecurity posture. The widespread use of 2FA technology ensures the protection of sensitive projects, financial systems, logistical operations, and human resource data. It acts as a safeguard for user endpoint devices, securing access and preventing security breaches in an ever-evolving technological landscape.

Government
In the realm of government agencies, implementing IT modernization initiatives necessitates a security solution that can keep pace. Multi-Factor Authentication (MFA) technology emerges as a vital component, striking a balance between robust security and usability. As federal agencies embrace zero trust policies, 2FA technology contributes to securing access for millions of end users, ensuring a resilient defense against potential threats.
10. Frequently Asked Questions About 2FA
1. Where Can I Enable Two-Factor Authentication (2FA)?
- • Email Accounts: Add an extra layer of protection to your email accounts through 2FA. This is crucial as a compromised email can be a gateway for hackers to recover and compromise your other accounts.
- • Financial Services: Boost the security of your online banking, payment systems, cryptocurrency exchanges, and other financial service accounts by activating 2FA.
- • Accounts Involving Payments: Strengthen the security of accounts storing your payment details, such as eBay and Amazon, by enabling 2FA. This adds an extra layer of defense for your financial information.
- • Social Media: Safeguard your presence on social media platforms like Facebook and Instagram by implementing 2FA. Mitigate the risk of unauthorized access and potential misuse of your personal information.
- • Accounts with Personal Data: Activate 2FA on accounts containing personal information, such as myGov, to prevent unauthorized access and ensure the protection of sensitive data.
- • Gaming Platforms: Given that online gaming platforms collect personal and financial data for remote identity verification and game purchases, it’s wise to protect access to accounts on platforms like Steam, Epic Games, and PlayStation with two-factor authentication.
To initiate 2FA, the process may vary based on the specific software or service. However, the general steps remain consistent across most applications. Ensure the security of your online accounts by enabling 2FA on these important platforms.
2. Who Should Use Two-Factor Authentication?
Two-factor authentication (2FA) is a vital security measure for everyone, regardless of their online activity level. It’s a must for those who prioritize robust protection for personal and business data.
Consider the following groups who should adopt two-factor authentication:
- 1. Everyone with Online Accounts. Individuals with accounts across various online platforms, spanning email, social media, banking, and shopping websites, should activate 2FA. This applies to both personal and professional accounts.
- 2. Businesses and Employees. Businesses should enforce 2FA for their employees to bolster the security of company accounts and sensitive information. This is particularly crucial for accessing corporate email, project management tools, admin accounts, and other business-related platforms.
- 3. Remote Workers. In the era of remote work, businesses with employees working from home or other locations should mandate 2FA, especially when utilizing VPN, RDP, or VDI services.
- 4. Financial Accounts. Given that banking and financial accounts are attractive targets for hackers, enabling 2FA is essential. Both individuals and financial institutions providing such services should note that users and employees must be protected with Multi-Factor Authentication (MFA).
- 5. Social Media Users. Social media accounts, storing personal information, are often targeted by cybercriminals. Activating 2FA on platforms like Facebook, Twitter, and Instagram is crucial to prevent unauthorized access.
- 6. Email Accounts. Since email serves as the gateway to many other online accounts (password reset requests, account recovery, etc.), securing your email with 2FA is paramount. It adds an additional barrier against unauthorized access to your entire online presence.
- 7. Students and Educational Institutions. Students and individuals using educational platforms or learning management systems should adopt 2FA to safeguard academic and personal information. Educational institutions should facilitate this by implementing two-factor authentication.
- 8. Healthcare and Sensitive Information. Individuals with accounts containing sensitive healthcare or personal information should give priority to 2FA for privacy and identity theft prevention. Hospitals and healthcare centers must ensure the implementation of 2FA to protect patient data.
- 9. Cryptocurrency Users. Users of cryptocurrency exchanges and wallets should activate 2FA to safeguard their digital assets. Cryptocurrency exchanges should take note and provide an additional level of defense for their users due to the heightened risk of attacks.
- 10. Individuals with Valuable or Sensitive Data. Anyone storing valuable or sensitive data online, such as intellectual property, proprietary information, or confidential documents, should employ 2FA to mitigate the risk of unauthorized access.
In conclusion, two-factor authentication is a versatile and indispensable tool for enhancing online security across a broad spectrum of users and industries.
3. Is Two-Factor Authentication Easy to Set Up?
Yes, Two-Factor Authentication (2FA) is generally easy to set up, and the process varies depending on the service or platform you are using. In most cases, the setup involves the following steps:
- 1. Log in to your account.
- 2. Go to security/account settings.
- 3. Choose a 2FA method (MFA app, SMS, email, 2FA bot).
- 4. Follow on-screen instructions (scan QR code or enter setup key).
- 5. Verify setup with a code.
- 6. Note any backup/recovery options provided.
Always follow the specific instructions of the platform or service. 2FA adds an extra layer of security to your accounts.
4. How Effective Is Two-Factor Authentication in Enhancing Security?
Two-Factor Authentication (2FA) is highly effective in enhancing security. It adds an extra layer of protection beyond just a password, making it significantly more difficult for unauthorized individuals to gain access to your accounts. Here are key reasons why 2FA is effective:
- • Reduces Impact of Stolen Credentials and Weak Passwords: Even if your password is weak, or in case of a breach or phishing attack, stolen passwords alone are insufficient without the second authentication factor.
- • Protects Against Unauthorized Access: 2FA prevents unauthorized entry, even if someone physically possesses your password or attempts login from a different location.
- • Time-Sensitive Codes: Authenticator apps generate time-based codes, intensifying security by limiting code validity.
- • Diverse Authentication Methods: Supporting SMS, authenticator apps, email, chatbots, or hardware OTP tokens, 2FA lets users choose based on preferences and security needs.
- • Compliance and Best Practices: Recommended by security standards, 2FA is a staple for safeguarding sensitive information.
However, 2FA isn’t foolproof. Users should practice good password hygiene, stay vigilant against phishing, and opt for a secure second factor like an authenticator app with cloud backup or a hardware 2FA token for added assurance. Overall, 2FA remains a critical and effective tool in ongoing efforts to enhance online security.
Deepen your understanding of multi-factor authentication by delving into the article 6 MFA Myths You Still Believe.
5. Can I Use Two-Factor Authentication Without a Smartphone?
Yes, you can use Two-Factor Authentication (2FA) without a smartphone. While many 2FA methods involve mobile apps, alternative options exist that do not require a smartphone:
- • Hardware OTP Tokens: Certain services provide hardware tokens or key fobs that generate time-based codes. These devices serve as a second factor for authentication. Even if the service doesn’t offer hardware OTP tokens, you can use programmable hardware tokens like Protectimus Flex or Protectimus Slim on such websites. Note that you’ll need an Android smartphone for one-time programming. After programming, the smartphone is not required.
- • Text Messages (SMS): A common method involves receiving a verification code via SMS. The code is sent to your registered mobile phone number, and you enter it during the login process.
- • Phone Call Verification: Some services offer 2FA through phone call verification. You receive an automated call that provides a spoken verification code, which you then enter.
- • Email Verification: Another option is to receive a verification code via email. This code is sent to your registered email address, and you use it to complete the authentication process.
- • Backup Codes: Certain platforms offer backup codes that you can generate and securely store. These codes serve as a backup if you’re unable to receive codes through your primary 2FA method.
Broaden your understanding of one-time password delivery and generation methods through our comprehensive article The Pros and Cons of Different Two-Factor Authentication Types and Methods.
6. What Happens if I Lose Access to My Two-Factor Authentication Device?
If you lose access to your Two-Factor Authentication (2FA) device, follow these steps:
- 1. Utilize Cloud Backup (If Applicable): If you use a 2FA app like Protectimus Smart with activated cloud backup, you can easily restore your tokens and regain account access.
- 2. Use Backup Codes: Check for backup codes provided during setup and use them to log in.
- 3. Try Alternative 2FA Methods: Check if the service offers alternative methods (e.g., text message, email, or phone call) and use those.
- 4. Explore Account Recovery Options: Many services have an account recovery process. Verify your identity through various means or follow the service’s specified recovery procedure.
- 5. Contact Support: If unable to recover, reach out to customer support for assistance.
To prevent future issues:
- • Use a Secure 2FA App: Utilize a two-factor authentication app with encrypted cloud backup for easy restoration on a new device.
- • Save Backup Codes: Securely store any backup codes provided during 2FA setup.
- • Use Multiple 2FA Methods: Set up various 2FA methods for added flexibility.
- • Update Contact Information: Keep recovery options, such as email and phone number, up to date.
7. Can Two-Factor Authentication Be Hacked?
While Two-Factor Authentication (2FA) significantly enhances security, it is not completely immune to hacking. Various methods have been used to compromise 2FA, but they often require a higher level of sophistication compared to simple password attacks. Here are some potential ways 2FA can be compromised:
- 1. Real-time Phishing Attacks: Cybercriminals may use phishing techniques to trick users into providing both their password and the second factor. This can occur through fake websites or malicious emails.
- 2. Man-in-the-Middle Attacks: In these attacks, an attacker intercepts and alters the communication between two parties. This could allow them to capture both the password and the 2FA code.
- 3. SIM Swapping: If an attacker can convince your mobile carrier to transfer your phone number to a new SIM card, they could potentially receive 2FA codes sent via SMS.
- 4. Keylogging: Malware or a keylogger on a device can capture both your password and 2FA code when you enter them.
- Credential Stuffing: If an attacker obtains a list of compromised passwords from one source, they may attempt to use these passwords along with captured 2FA codes on other services.
- 5. Social Engineering: Attackers may try to manipulate individuals or support staff into providing access or resetting 2FA settings.
While acknowledging these risks, the implementation of Two-Factor Authentication (2FA) significantly raises the bar for attackers and fortifies security. To maximize the effectiveness of 2FA, it’s essential to employ multiple and diverse authentication methods. Additionally, users should refrain from sharing codes, exercise caution when confronted with suspicious links, maintain updated software and systems, and remain vigilant against phishing attempts.
For an added layer of protection, users can adopt proactive measures such as implementing data signing and CWYS (Confirm What You See) to combat phishing. Advanced methods like hardware tokens provide heightened security compared to relying solely on SMS. Strengthening overall security involves applying 2FA to each account, using robust passwords, and avoiding third-party logins.
While recognizing that no security measure is entirely foolproof, it is clear that utilizing 2FA remains a best practice for enhancing online security.
Delve deeper into the intricacies of this subject by reading the article 2FA Security Flaws You Should Know About.
8. What’s the Difference Between MFA and Two-Factor Authentication (2FA)?
2FA and MFA may seem interchangeable, but there’s a nuanced distinction between them. Two-Factor Authentication (2FA) specifically involves the use of two factors to authenticate a user — typically a password and a second factor like an OTP or a push notification. On the other hand, Multi-Factor Authentication (MFA) is a broader concept encompassing the use of two or more factors for user authentication. MFA extends beyond 2FA, incorporating various methods such as biometrics, location and time filters, or smart cards in addition to conventional factors like passwords and OTPs. In essence, 2FA serves as a subset of MFA, highlighting that MFA provides a more expansive array of authentication options, offering heightened flexibility and security measures beyond the constraints of just two factors.
11. How-To’s for Protectimus Users
1. Step-By-Step Guide on Setting Up Protectimus MFA
Setting up Protectimus Multi-Factor Authentication (MFA) and integrating it into your infrastructure involves a series of straightforward steps. It’s essential to note that the specific process may slightly differ based on the service you’re securing and whether you opt for the Cloud-Based Protectimus MFA Service or the On-Premise MFA Platform.
We recommend initiating testing of the Protectimus two-factor authentication system by configuring the cloud service. Transitioning between cloud and on-premise authentication servers is straightforward and involves simple adjustments to the configuration file.
To commence with Protectimus Cloud MFA Service:
- 1. Create a Protectimus Account:
- • Visit https://service.protectimus.com/en/ and sign up for an account.
- 2. Access the Dashboard:
- • Log in to your Protectimus account and access the dashboard.
- 3. Add Resource:
- • Navigate to Resources and click ‘Add Resource.’
- • Enter a Resource Name of your choice; other parameters are optional.
- 4. Integrate Protectimus Cloud Service with Your System:
- • The integration process may vary based on the system you’re safeguarding. Access integration instructions for various systems on the Docs page at https://www.protectimus.com/guides/saas-service/.

2. What Types of Authentication Methods Does Protectimus Support?
Protectimus offers a versatile range of OATH-compliant authentication methods designed to meet diverse security requirements. Each method is tailored to specific purposes, ensuring a comprehensive and adaptable approach to multi-factor authentication for both personal and corporate applications.
HARDWARE TOTP TOKENS
- • Programmable security tokens providing a hardware alternative to 2FA apps.
- • Available in standard bank card and mini form-factors.
- • Supports TOTP (RFC 6238) algorithms with optional SHA-1, SHA-256.
- • Ideal for corporate use with Google Authenticator, Microsoft Azure MFA, and personal use across platforms.

- • High-strength, water-resistant hardware OTP tokens.
- • Utilizes TOTP algorithms with optional SHA-1, SHA-256.
- • Ideal for corporate use with Protectimus MFA service and systems supporting added secret keys.

- • Programmable hardware TOTP token in a key fob format.
- • Supports TOTP (RFC 6238) algorithms with SHA-1.
- • Suitable for both corporate and personal use across various authentication services.

- • Classic hardware TOTP token with SHA-256 algorithm support.
- • Features an LED display with six digits and a time indicator.
- • Suitable for corporate use with Protectimus MFA service and systems supporting added secret keys.
2FA AUTHENTICATOR APP PROTECTIMUS SMART
2FA Authenticator App Protectimus SMART
- • Free 2FA app for iOS and Android.
- • Encrypted cloud backup, PIN, and biometric protection.
- • Supports various algorithms, encrypted cloud backup, and customizable OTP length.
- • Ideal for personal use across any 2FA-supporting website and corporate use with Protectimus or other authentication services.
FREE OTP DELIVERY SERVICES
- • Free OTP delivery with chatbots in messaging apps, offering a reliable alternative to SMS.
- • Supports HOTP and OCRA algorithms, along with data signing functionality.
- • Suitable for corporate use with Protectimus MFA service.
- • Offers free OTP delivery via email with HOTP algorithms and data signing.
- • Suitable for corporate use with Protectimus MFA service.
SMS AUTHENTICATION
- • Delivers one-time passwords via SMS messages.
- • Supports HOTP algorithms and data signing.
- • Ideal for corporate use with Protectimus MFA service.
3. Can Protectimus Be Used for Both Personal and Business Accounts?
Absolutely! Protectimus caters to both personal and business needs by offering a variety of user-friendly 2FA software and authentication methods, including hardware tokens, mobile apps, and OTP delivery services. This diverse range provides versatility for different scenarios. While many Protectimus products are designed with businesses in mind, there are also excellent options tailored for individuals.
For personal use, the standout is the free 2FA app, Protectimus SMART OTP, which includes encrypted cloud backup. It’s an excellent choice for securing personal accounts on websites that support two-factor authentication (2FA). Notably, the programmable hardware tokens Protectimus Slim and Protectimus Flex are also ideal for both personal and business use. They can be seamlessly connected to almost any service, such as Google, Dropbox, GitHub, Microsoft, Facebook, and many cryptocurrency exchanges, serving as an alternative to a 2FA app.
Additionally, Protectimus offers a straightforward 2FA solution for Windows and RDP. It’s easy to install and accommodates up to 10 users for free. This solution is beneficial for both businesses and individuals looking to enhance the security of their personal Windows accounts.
In the business realm, Protectimus delivers a robust multi-factor authentication (MFA) platform with diverse hardware and software choices. This ensures a comprehensive strategy for safeguarding corporate systems and applications.
4. Is Protectimus Compliant With Industry Security Standards and Regulations?

Protectimus upholds industry security standards and regulations through certifications that attest to the effectiveness of its multi-factor authentication solutions. One such recognition is the OATH certification from The Initiative for Open Authentication. OATH, a leading industry organization dedicated to promoting robust authentication, runs the OATH Certification program. This program rigorously verifies and certifies vendor products, ensuring they meet the specified criteria outlined in the OATH certification profiles.
Moreover, Protectimus proudly holds the Citrix Ready Partner certification, affirming the compatibility of its 2FA solution with Citrix products. This recognition comes from evaluations by Citrix experts, granting Protectimus the Citrix Ready status. As a Citrix Ready Partner, Protectimus’s two-factor authentication solution is officially recommended for seamless integration with Citrix, highlighting its reliability and compatibility.
5. How Can I Set Up Protectimus for Different Applications and Accounts?
Setting up Protectimus for various applications and accounts is easy:
Simple Integration into Any Infrastructure: Protectimus streamlines the integration process with a variety of MFA plugins, ensuring quick connections to all systems within your infrastructure. Additionally, Protectimus offers a user-friendly API, even with its free plan, making integration straightforward. Developers can also leverage Software Development Kits (SDKs) available in popular languages like Java, PHP, and Python. If a specific plugin is unavailable, the dedicated development team is ready to assist in connecting and integrating with any service. This approach ensures comprehensive two-factor authentication coverage across your infrastructure.
Efficient User Grouping and Management: Protectimus simplifies user grouping and management through resources. Within a single account, you can create multiple resources, each with its own set of administrators. For example, the protection needs for your end users and the admin panel may differ. One resource is tailored to end users, offering various token options for their convenience, including hardware tokens, 2FA apps, or connecting to the Protectimus chatbot on messaging services. Simultaneously, another resource within the same Protectimus account is dedicated to administrators, developers, and support staff. This resource imposes stricter authentication rules, allowing only hardware tokens and implementing filters based on time and location. This resource-based approach enables the effective management of diverse user groups, each with specific security requirements based on their access levels to sensitive data.
6. What Support Options Are Available if I Encounter Issues With Protectimus?
We understand that timely assistance is crucial, and our support services are designed to meet your needs.
8/5 Support
Our team is here for you during working hours on business days, providing support for all paid tariff plans (Starter, Business, Custom, Platform, Cluster) without any additional payment. You can reach out via email at [email protected], by phone, or conveniently use the contact form on our website. Additionally, our Support Ticket System in the Protectimus Platform dashboard ensures a quick and organized response.
Extended Support Options (Extra Charge)
For those who require additional coverage, we offer extended support options:
- • 24/5 Support: This provides assistance 24 hours a day, five days a week.
- • 24/7 Support: Enjoy round-the-clock support, seven days a week.
With our extended support, you also receive access to an emergency number for immediate assistance during critical situations. This ensures that you receive the level of support that aligns with your specific requirements.
7. Is Protectimus Compatible With Popular Platforms and Services?
Certainly! The Protectimus multi-factor authentication (MFA) solution is compatible with a variety of popular platforms and services, offering ready-to-go integration plugins and the possibility of seamless 2FA integration via API. By effortlessly integrating with a diverse range of systems and applications, Protectimus products provide robust data protection on platforms such as MacOS, Windows (both locally and through remote access via RDP), Ubuntu, OWA, ADFS, Active Directory, LDAP, Roundcube, and systems supporting the RADIUS protocol. Should you have any questions or encounter difficulties, our dedicated development team is always ready to assist.
8. What Is the Lifespan of Protectimus Tokens, and How Do I Replace Them?
Protectimus hardware OTP tokens typically have a lifespan covered by a warranty of 12 months and 2 weeks from the date of shipment. The warranty is valid under normal operating conditions and without mechanical damages. Generally, these tokens serve for 3 to 5 years, depending on the battery life and the number of OTP generations. Please note, if the tokens are working well, returns or exchanges are not possible. Hardware tokens are designed for information security, containing confidential built-in secret keys that cannot be shared with another customer.
9. How Can I Recover My Account if I Lose My Protectimus Device or Token?
If you misplace your Protectimus device or token, please reach out to your administrator for assistance.
If you are an administrator and find yourself without access to your Protectimus account, kindly contact our support team for further assistance.



