What phishing is has been well-known for some time now. The first phishing attacks were noted shortly after the World Wide Web appeared. But despite the efforts of IT security specialists to create more effective ways of anti phishing protection, new phishing sites continue to appear every day.
According to the data from several studies, there were about 5000 new phishing sites created every day in 2016. In 2017, this figure will be even greater. The secret to the resilience of this type of fraud lies in how it is based not on “holes” in software, but on a vulnerability in human beings themselves, particularly those with access to important data. That’s why we’re going to remind you once more what phishing is, what the most common phishing attacks examples are, and what you can do to counter them.
“Phishing is a real threat, which is relatively easy to implement and difficult to identify and counteract.”
― Max Oliinyk, Chief Executive Officer, Protectimus Solutions LLP
Basic phishing examples 2017
Phishing is a kind of internet fraud that’s based on social engineering principles. The main purpose of phishing scams is to gain access to critically important data (passport data, for example), accounts, banking details, secret company information, and so on; so that it can be used to steal funds at a later date. Phishing works by redirecting users to fake network resources that function as complete imitations of a real site.
| Read also: Social Engineering Against 2FA: New Tricks
Deceptive phishing examples
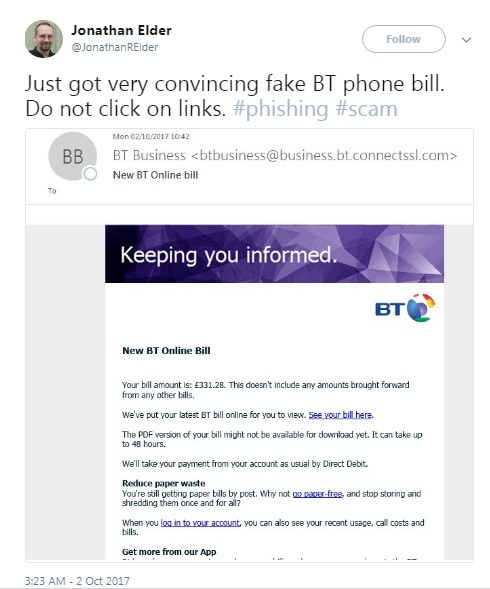
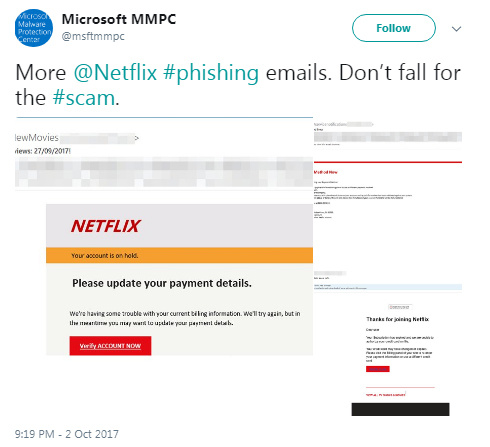
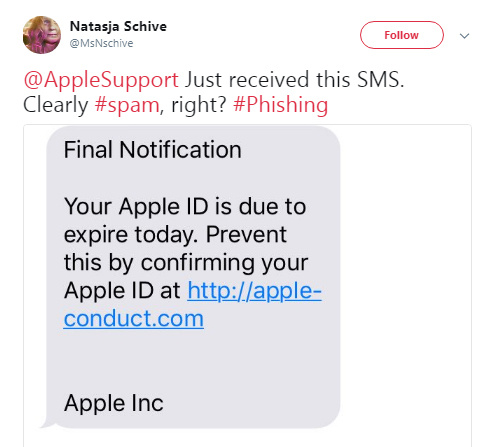
The majority of phishing attacks fall under this category. Attackers send out emails pretending to be from a real company, in order to receive users’ account data and thus gain control over their personal or official accounts. You could receive a phishing email claiming to be from a payment processor, a bank, a courier service, an online store, a social network, a revenue service, and so on.
Phishing emails are created very exactingly. They can be practically indistinguishable from the emails a user would normally receive from the company. The only difference may be in the request to follow a link in order to perform some kind of action. This transition, however, leads to the scammers’ site, which acts as a doppelgänger of the entity’s real website.
To get you to click on these links, the emails may dangle a proverbial carrot in front of you: “Take 70% off our services if you sign up within 24 hours!” They may also try to scare you: “Your account has been locked due to suspicious activity. To confirm that you are the account owner, click on the link.”
Here’s a list of some of the scammers’ favorite phishing examples:
“Your account has been/is going to be locked/disabled.”
Scare tactics can be quite effective. The threat of having your account locked if you don’t immediately log in can cause users to let their guard down, follow the link in the email, and enter their username and password.
“Suspicious/fraudulent activity has been detected on your account. You must update your security settings.”
These kinds of emails urgently ask you to log into your account and update your security settings. They work on the same principle as the previous attack. The user panics and lets their guard down.
“You have received an important message. To read it, please log into your personal portal.”
These phishing emails usually pretend to come from financial institutions. Users tend to believe that these emails are real, since financial institutions don’t send confidential information directly via email.
Tax-related phishing emails
There’s always a spike in the number of tax-related phishing emails that get sent out as Tax Day approaches. These emails can have a variety of subjects. They may claim to be debt notifications, requests for missing documents, notices of your right to a refund, and so on.
| Read also: Email hacking protection
Spear phishing scams
Phishing isn’t always done at random. Spear phishing email examples are often personalized and targeted. The purpose is the same—to get the user to navigate to a phishing site and input their account details.
Naturally, potential victims are more likely to trust an email that refers to them by name, mentions their place of work and position, or includes any other kind of personal details. Users often provide the information used in these phishing attacks themselves. Resources like the well-known LinkedIn are particularly helpful to criminals: when you create a résumé to send to potential employers, you try to include a lot of information about yourself.
To prevent spear phishing attacks, companies should frequently remind their employees about the undesirability of publicly disclosing personal and official information.
“A single spear-phishing email carrying a slightly altered malware can bypass multi-million dollar enterprise security solutions if an adversary deceives a cyber-hygienically apathetic employee into opening the attachment or clicking a malicious link and thereby compromising the entire network.”
― James Scott, Senior Fellow, Institute for Critical Infrastructure Technology
| Read also: Do we need multi-factor authentication in social networks?
CEO phishing scams
Management accounts are of particular interest to phishing scammers.
As a rule, security specialists in every company implement a system of permissions and responsibility levels based on the employees’ positions. The sales manager, for example, has access to the product database, while their access to the list of the company’s employees is restricted. The HR specialist, on the other hand, has access to information about who has which job, who has just been fired, who deserves a promotion—but they don’t know a thing about the sales figures or company bank accounts. The head of the company, however, typically has access to all the critical elements of the enterprise or organization’s life.
After gaining access to this person’s accounts, the phishing specialists can go on to use the information to communicate with other departments, e.g. to approve fraudulent bank transfers to an arbitrary financial institution.
Despite their high clearance levels, those in upper management don’t always take part in training programs that teach employees the basics of information security. This is why phishing attacks targeted against them can lead to particularly disastrous consequences for the company.
| Read also: A Wrong Lesson on Information Security
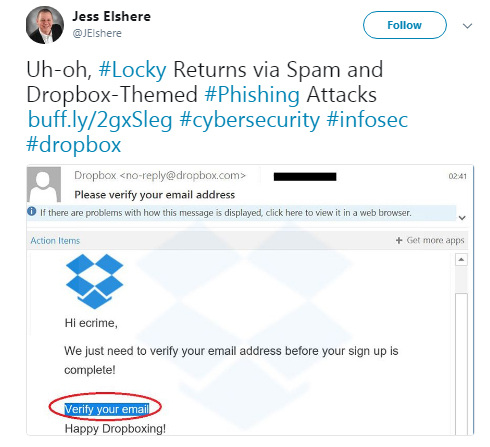
Google Docs and Dropbox phishing scams
More recently, phishing has taken a new direction: hunting for usernames and passwords to cloud storage accounts.
Users of the prominent cloud storage services Dropbox and Google Drive pack their accounts with sensitive information from both their own lives and their jobs. This includes presentations, spreadsheets, and documents from the office; data backups; personal photos; and passwords to other services.
Gaining access to these kinds of resources is, unsurprisingly, a tempting prospect for attackers. The same, standard approach is used for this purpose, too. A phishing site is created to mimic the login page of a given service. Potential victims are typically directed to the fake site by phishing links sent via email.
| Read also: Will Google’s Authentication without Passwords Be Safe?
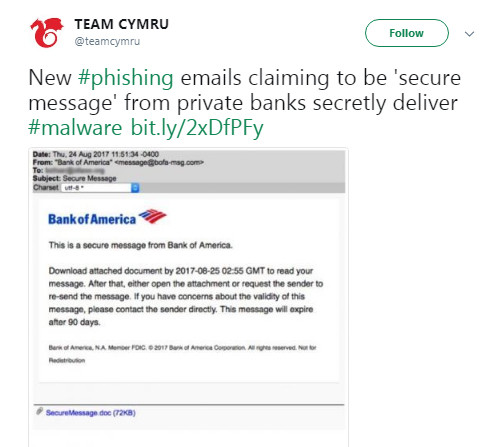
Attachment-based phishing scams
Links to suspicious sites that try to steal your data aren’t the worst that phishing has to offer. In those cases, criminals only gain access to specific confidential information: a username and password; i.e., an account with a particular service. What’s much worse is when a phishing attack leads to the victim’s entire computer becoming compromised by malware, like ransomware, spyware, and Trojan horses.
These kinds of malware can be attached to phishing emails. Supposing that the email came from a trusted source, users willingly download these files and infect their laptops, tablets, and desktop computers alike.
What is pharming?
“Classical” phishing that uses links to questionable sites is gradually becoming less effective. Experienced users of internet services are usually already aware of the danger inherent in clicking links to suspicious sites, so they’re cautious when they receive strange emails. Luring victims to these sites is becoming more and more difficult.
As a response to the declining effectiveness of these traditional attacks, attackers have devised pharming, which uses a hidden redirect to a fraudulent site.
With pharming, a Trojan horse is first introduced into the victim’s computer one way or another. These Trojans are often not detected by antivirus programs. They give no signs of their presence, instead waiting patiently in the wings. The malware is activated only when the user, without any external influence, decides to navigate to a site the attackers are interested in. These are usually sites for online banking, payment systems, and other entities involved in financial transactions. Around this time, a substitution occurs: instead of the requested site, the user of the infected computer is redirected to the phishing site. Not suspecting anything, the user provides the data the attackers are looking for. This is accomplished by changes to the DNS cache of the local computer or network equipment. This type of fraud is particularly dangerous due to how difficult it is to detect.
| Read more: Protectimus New OTP Tokens
How to Protect Yourself from Phishing Scams
- Be sure to check the URL you’re asked to visit when there are small errors in the writing of the message.
- Use only secure HTTPS connections. The lack of an S in the site address should be a red flag.
- Treat emails with attachments and links cautiously. Even if they appear to come from a known address, this doesn’t guarantee your security: the address could be compromised.
- After receiving an unexpected, suspicious message, contact the supposed sender by alternative means to clarify whether or not the sender really sent it.
- If you still need to navigate to the site, enter the address manually or use a saved bookmark instead (alas, this won’t protect you from pharming).
- Don’t use open Wi-Fi networks to access online banking and other financial services. These are often created and operated by attackers. Even if this isn’t the case, unencrypted connections pose no difficulty to hackers.
- Use two-factor authentication for all your accounts, when possible. This can save an account from being compromised if your password becomes known to an attacker.
Conclusion
It is unlikely that phishing will be completely eradicated in the near future: human laziness, gullibility, and greed are to blame for this.
New phishing scams appear every day and can take a variety of forms. The basic phishing scams are:
- Deceptive phishing. Phishing emails claiming to be from well-known legal companies that are practically indistinguishable from the emails the users would normally receive from these companies. The only difference may be in the request to follow a link in order to perform some kind of action.
- Spear phishing. Personalized and targeted phishing emails containing such information as the potential victim’s name, position, or includes any other kind of personal details.
- CEO phishing. Phishing emails targeted on gaining access to the accounts of the head of the company, CEO, CTO, etc. After gaining access to such accounts, the phishing specialists can go on to use the information to communicate with other departments, e.g. to approve fraudulent bank transfers to an arbitrary financial institution.
- Google Docs and Dropbox phishing. A relatively new direction of phishing scams hunting for usernames and passwords to cloud storage accounts.
- Attachment-based phishing. Phishing e-mails with attachments containing viruses.
- Pharming. A hidden redirect to a fraudulent site accomplished by changes to the DNS cache of the local computer or network equipment.
Only the availability of timely, complete information about hackers’ methods, and a healthy suspicion of unusual, unexpected messages, will significantly decrease the damage done by this type of internet fraud.
Thus, learn how to protect yourself from phishing scams. And first of all, don’t give your passwords to anybody. Make a habit of entering site addresses manually or using bookmarks saved in your browser. Be particularly careful with links in emails.
Read more:
- Credit Card Fraud – Most Common Ways
- Malvertising: Can It Be Stopped?
- Which messaging apps are trustworthy?
- What is Online Skimming and How to Avoid It
- Biometric Authentication Pros and Cons
- How to Choose and Use Strong Passwords
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


2022-01-22
Wow! Nice!
2022-02-07
🙂