Any more or less experienced Internet user came across 2FA at least once. But not everyone understands how it works. To use this powerful data protection tool more effectively let’s learn more about it.
The first factor of 2-factor authentication – what we know
Two-factor authentication starts with the usual standard password used for signing in on any website. Usually, the users themselves choose the password to create an account. And itself, the reusable password is not reliable enough and can provide only an elementary basic level of account protection in 2-factor authentication. This password is the first ‘key’ to unlock the account.
Yet, the reusable password, especially if chosen wisely, is an important component of two-factor authentication as it is a knowledge factor. The category of knowledge factors may also include PIN-codes.
What follows the procedure of password entering? There are few different variants.

There are three factors of user authentication: what we know; what we have; and what we are.
The second factor of 2-factor authentication – possible variants
Two types of authentication can be used as the second factor of 2FA:
- What we have.
Hardware tokens in the form of a smart cards, certificates with the digital signature, tokens generating time-based OTP passwords. These authentication means need a physical connection and usually the knowledge of the PIN-code. The user also needs to install special software on the computer he or she uses to interact with OTP token when logging in. To some users, this method seems not comfortable as they have to carry hardware tokens with them all the time and keep an eye on their safety. If a smart card or hardware token is lost or stolen, the client’s authentication will be impossible.
- What we are.
This group of authenticators includes the integral biometric characteristics of the person. These can be a fingerprint, retina pattern, face shape, voice, etc. The identifiers of this type use cryptographic methods and means. Most commonly biometric authentication is applied to control access to the premises or equipment – such as at the walk-through enterprises and organizations.
Biometric authentication is not the most reliable to be used for the access control on distance (as on the Internet). The one-time passwords are good as they are relevant during only one session. Even in the case, when hackers intercept the OTP password, this password will be useless when they will try to re-use it.
Methods of one-time passwords generation
To understand what principles 2-factor authentication uses in its work, it is important to imagine how one-time passwords are generated and how they become known to the legitimate user entering the system.
There are several ways to deliver the password:
- to send by e-mail;
- to send by SMS;
- to give a list of one-time passwords in advance;
- to generate the OTP password with the help of software or hardware token.
OTP passwords stability is primarily achieved by using complex constantly improving algorithms.
Protectimus offers the solutions that use three major algorithms.
- HOTP – HMAC-Based One-Time Password Algorithm.
The basis for the OTP generation according to this algorithm is the number of procedures the user underwent and the secret key known beforehand by both parties. The same values are taken into account during the authentication validation on the server.
- TOTP – Time-based One-time Password Algorithm.
This authentication algorithm generates the OTP password considering the time parameter. Typically, not a specific time is used, but rather a current interval with predetermined boundaries.
- OCRA – OATH Challenge-Response Algorithm.
This algorithm generates one-time passwords using a random value sent by the server as the input data. It can also be complemented with the data signature (Confirm What You See or CWYS) function, which helps to strengthen the security of the authentication procedure. CWYS function allows adding specific parameters (time, addressee, currency, the amount of transfer etc.) to the secret key and a random value when creating and verifying the OTP password. Due to its high reliability, the OCRA algorithm is perfect to be used in the most critical areas of the data transmission and storage system.
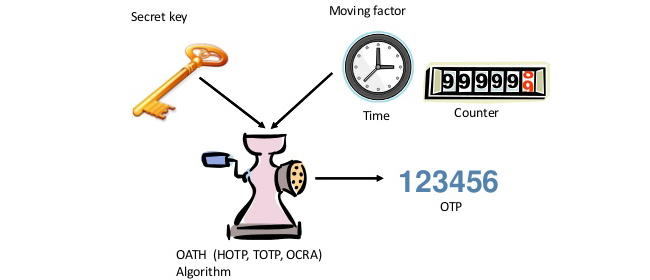
One-time password generation algorithms
HOTP and TOTP algorithms serve for a one-sided authentication – the server authenticates the client. But OCRA algorithm can provide a double-sided mutual authentication of the user and the website he or she enters. This point is especially important to eliminate the threat of the Automated Transfer System, replacement, and banking Trojans, which are particularly dangerous for banking operations.
What are the benefits of 2-factor authentication?
The main advantage of 2-factor authentication is a mutual support of one factor by another. If a hacker obtains a login and a standard password, the inability to enter the one-time password can prevent unauthorized access to the account. And vice versa, if the fraudster gets the OTP token, the authentication will not happen without entering the standard password or the PIN-code. This type of authentication is so strong because the benefits of one factor may overlap the deficiencies of another. And that’s what makes two-way authentication efficient and reliable.
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!