In response to new challenges, Protectimus has developed a powerful means of protection against auto-filling, injecting, and other types of malicious software that manipulates and modifies data during transactions.
There are different ways in which such software can work; for example, the recipient is changed during a transfer as an unsuspecting user enters a one-time password sent via an SMS message. The problem is that this user actually performs and verifies a fraudulent transaction without even realizing that fraudulent activities are taking place.
A serious threat for banks and payment services lies in the fact that customers unwilling to admit their own mistakes place the blame on the payment systems themselves, which undermines companies’ business reputation.
The Protectimus R&D Department has come up with a solution to this problem. In accordance with RFC 6287, the challenge for the challenge-response algorithm is generated randomly. We have taken further steps and developed a special challenge generation algorithm based on the details of a transaction performed by a user. It allows entering the data correlating to the data being verified and a one-time password; consequently, if this user’s data is modified in any way, the one-time password entered cannot verify the data because it is generated based on a different set of data, which prevents the possibility of any fraudulent activities.
The new data signing function called CWYS (Confirm What You See) is available in the Ultra, Smart, SMS, and Mail tokens.
Diagram 1 shows the process of performing a transaction requiring verification.
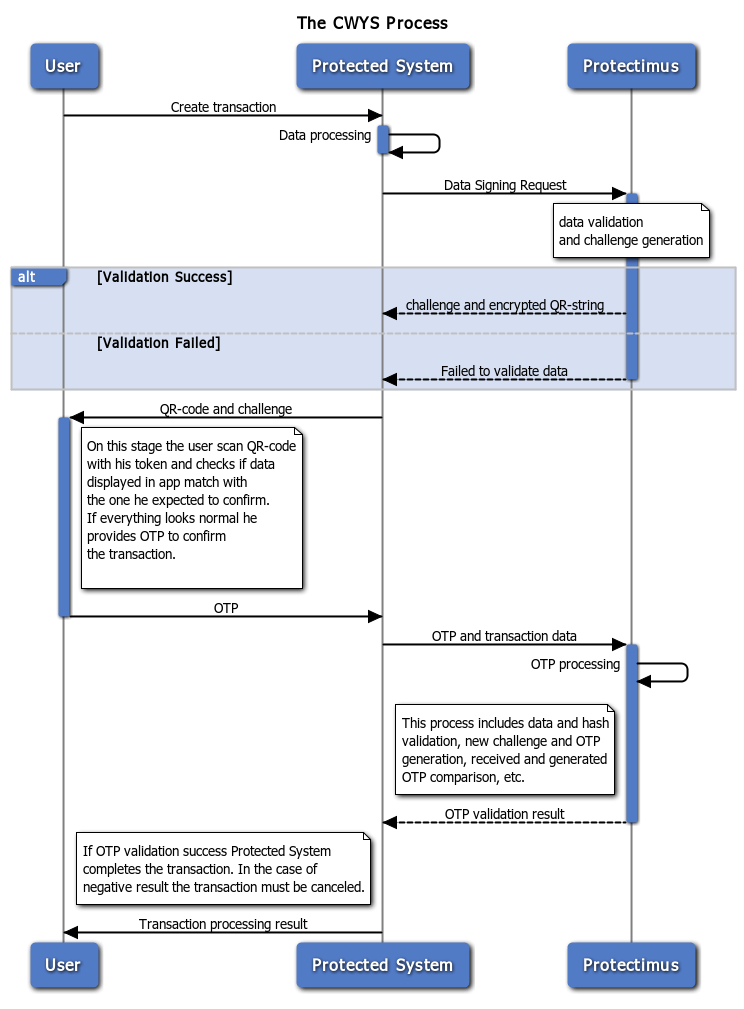
To send data to Protectimus and receive a challenge, a user must call the POST method at
https://api.protectimus.com/api/v1/token-service/tokens/sign-transaction
using these mandatory parameters:
- tokenId – user’s token identifier;
- transactionData – transaction details to be used in ОТР generation;
- hash – НМАС-SHA256 hash of the transactionData string to verify the integrity of the data received; the user’s API key is used as the key.
In the response, you will receive XML or JSON with the following elements:
- challenge – challenge for the ОТР generation algorithm;
- transactionData – encrypted transaction details;
- tokenType – token type;
- tokenName – token name;
- id – token identifier.
For a user with a Smart token, a QR code needs to be generated and displayed; for users with other types of tokens or for users unable to scan the QR code, there has to be a displayed, which they must enter in the token to generate an ОТР.
For example, if in the reply you received a challenge equal to 191,565, and the value of transactionData = 9 / vhmVzLIm / M + 8w9QXiJDA ==, then the row for QR code generation will look as follows:
transaction: // challenge = 191565 & transactionData = 9 / vhmVzLIm / M + 8w9QXiJDA ==
To complete the process and verify the transaction, the user must provide the OTP received to the system being protected. After receiving the ОТР, the system again sends a POST request to this address:
https://api.protectimus.com/api/v1/token-service/tokens/verify-signed-transaction
with the following parameters:
- tokenId – user’s token identifier;
- transactionData – details of the transaction being verified (it is important to send the details that will be sent to perform the transaction, not those received when performing the previous steps);
- hash – hash of the transactionData string generated in the same way as when calling the previous method;
- otp – one-time password provided by the user.
In response, the system being protected will receive information on the validity of the one-time password provided.
The CWYS function will be available in the new version of the Protectimus software. If you want to protect yourself and your data now, please contact the customer support service to get this new and advanced tool today.
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!