Hackers are not lazy, they evolve fast, so relying on old security measures is a terrible idea. Today we will look into how secure two-factor authentication is in general, what methods are used to hack 2FA and up-to-date ways to protect yourself against those account hacks. Finally, you will get answers to the most recurrent questions on 2FA security.
How secure is two-factor authentication?
Is two-factor authentication safe? All accounts (emails, apps, online stores, etc.) are protected with a user password, it’s been done that way for ages. Unfortunately, passwords like “123456”, “qwerty” and “password” have been the most used ones for ages too. They still are, however mind-boggling that is. 2FA authentication adds a second layer to the common user password protection. The second security factor can be either something you have (your cellphone or hardware OTP token) or something you are (your fingerprint). In addition to something you know (the password), it creates another way for the server to confirm you are who you say you are. So an account protected with dual authentication is much harder to hack into, even if the user password is easy to compromise. The strengths of one factor surpass the vulnarability of the other.
But is two-factor authentication hackable? It is if you let it. Let’s take a look at how.
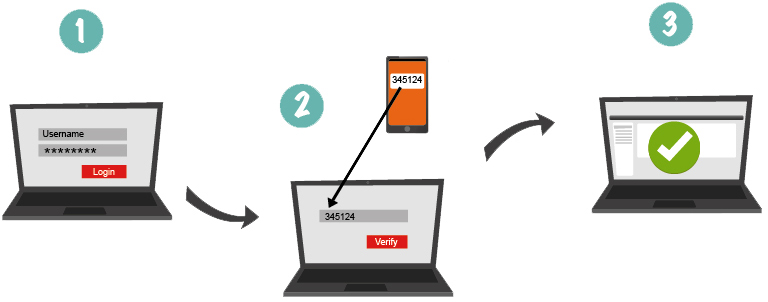
How would hackers bypass two-factor authentication system?
1. Real-time phishing
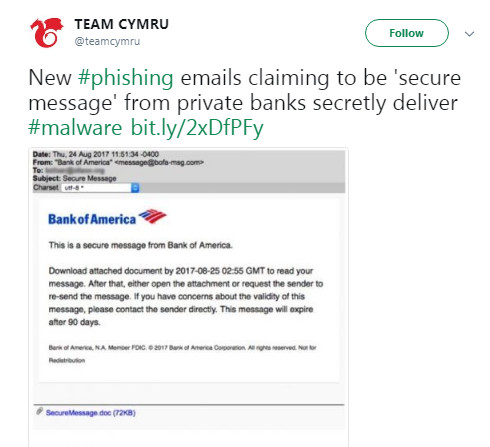
2FA was created to fight against phishing as a login weakness. Lo and behold … the hackers come up with a new two-factor authentication hack — real-time phishing.
A fake website that looks exactly like its legitimate counterpart is set up. Then the hacker sends the target an email prompting them to login for whatever reason (account expiration, some action needed to be taken etc). The user goes to the login page, which looks and works exactly like the one the user expects to see, they log in using their user password. Then the fake website asks for the second factor, just like the legitimate one would, the user complies and enters the OTP (one-time password) and the phishing website captures both passwords. In the background, the hacker has a few seconds to use the combination to get into the real account.
2. Social Engineering
This is a popular social engineering scheme — a criminal impersonates the target’s bank or a service provider, there have been accidents when a crook impersonated even a law enforcement agent and tricks the user to disclose the OTP. However, many warnings are issued, however often the account providers tell their customers to never trust such calls, social engineering attacks are still very successful.
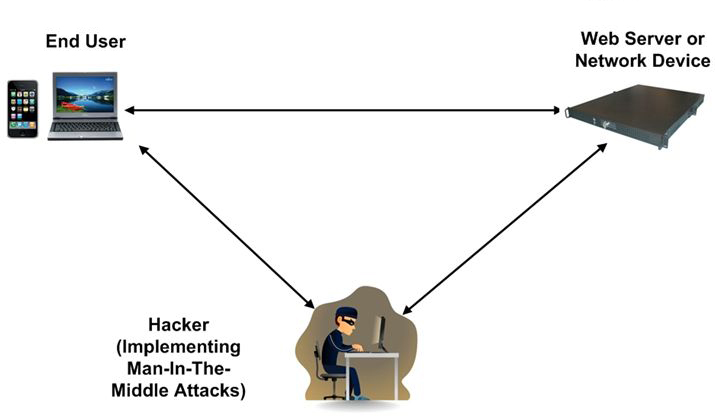
3. Man in the middle and man in the browser attacks
Man in the middle attack implies that the hacker inserts himself in the middle of the two systems’ communication. This can be done either with a fraudulent cryptographic certificate, inserting fake root certificates in the target’s browser database of trusted certificates, or by compromising a root certificate authority listed in the database.
As a result, two connections are created — client-attacker and attacker-server, instead of a single client-server one. Once the connection is intercepted the hacker can read and modify the transactions done via the connection.
Man in the browser uses a Trojan horse to intercept and manipulate the transactions on-the-go as they are made in the browser. With this attack the browser’s display is falsified, the user sees their intended transaction. In both attacks, the user won’t notice anything amiss.
4. SMS authentication issues
The main SMS 2FA weakness is the dependency on the service provider. The practice of reusing mobile phone numbers is a distinctive risk. If your OTP is delivered via SMS, all the hackers need to do is get the ownership of your phone number. A criminal impersonates their target and convinces the provider the user’s phone is lost so the number needs to be transferred. Doing this is not as hard as you might think.
One of the other SMS two-factor authentication issues is the smartphone’s Internet connection. It is easy to infect a smartphone with malware and intercept the OTP SMS.
5. Account recovery
The overall security level depends on the procedure of account recovery in case when one of the authentication factors gets lost or the attacker pretends that they are lost. For example, this might be considered a two-factor authentication weakness, if it’s enough to enter your mother’s maiden name or the name of your favorite author to recover access to the account. It’s not so hard for the hacker to find out this info using social engineering.
Another issue that turns out as a 2FA weakness — oftentimes websites ask for the user’s phone number to recover access via SMS. In this case, even if the user gets OTP via a hardware token, 2FA security is pulled down to the same level as SMS 2FA. Which is very low. This is one of the major two-factor authentication flaws.
6. Third-party login
Oftentimes websites and apps offer third-party (Facebook, Gmail, etc.) login option, which bypasses 2FA. Getting your Facebook credentials is not too hard for a seasoned hacker.
| Read also: Top 7 Tips How to Protect Yourself from Phishing Scams
How to prevent 2FA security hack
Use data signing
To protect yourself from various phishing and malware attacks opt for data signing or CWYS (Confirm What You See). With CWYS OTPs are generated drawing from the current transaction data and can be used only to verify that particular transaction performed by that particular user. If intercepted, such OTP will be useless.
Train yourself and your staff to identify phishing and social engineering
The main 2-factor authentication weakness is the user. But you can always eliminate this weakness by training yourself to recognize the attacks.
- Never click on suspicious links.
- Never reply to suspicious emails.
- Always check the spelling of the URLs.
- You can also try some anti-phishing training to become a pro in recognizing when someone tries to scam you.
- Use advanced 2FA methods (hardware tokens, OCRA tokens).
- Stop using outdated methods like SMS and HOTP tokens and eliminate the 2FA security flaws caused by them. Choose hardware tokens and opt for the most recent algorithms (TOTP and OCRA), and you’ll never see any disadvantages of two-factor authentication in action.

Use 2FA security on each account
If a hacker gains access to one of your accounts what are the chances they will gain access to all of them? Just think about it for a second, the answer is pretty clear. If you use Facebook to create accounts on multiple websites and a hacker breaks into your Facebook, if they gain access to your email and thus can reset credentials for all of your accounts … is two-step verification secure in these scenarios? The answer is no. But if you apply 2FA security on each account separately. And use a hardware token for good measure. Then yes, your accounts are as safe as can be.
Use strong passwords
As we’ve already mentioned — with 2FA the strengths of one factor surpass the vulnerabilities of the other. So it’s reasonable to strengthen both factors as much as you can, rather than relying on only one of them. Strong passwords for all of your accounts will protect them if your 2FA security token is stolen or otherwise compromised. A strong password is at least 8 characters long, contains both letters and numbers, upper and lower case and uses special characters.
| Read also: 4 Reasons Two-Factor Authentication Isn’t a Panacea
Frequently Asked Questions
Though not too easy, it is definitely possible. Man in the middle and man in the browser attacks are most likely to go unnoticed by the user. But they require quite a bit of resources, so it has to be worth it. Other ways include stealing the hardware token, and social engineering, which are not as likely to go unnoticed.
Strong passwords combined with hardware OTP tokens. Data signing feature (Confirm What You See) is also a great tool, especially for corporate accounts.
Theoretically yes. A secret key can be brute-forced and used to create a copy of your OTP token. But a secret key is usually at least 16 characters long. There are on average 62 variants for each of the 16 characters, which turns into 47672401706823533450263330816 tries. Even if a hacker can do a billion tries per second, they will need about 1511681941489 years to brute-force the secret key.
Well… MFA (Multi-factor authentication) using all 3 factors will be more secure than 2FA. But quantity does not always mean quality. The number of factors you use won’t matter if your TOTP storage is easy to compromise and your accounts are easy to recover using social engineering.
The short answer is yes to both. If you use SMS or even an app to deliver/generate OTPs for your Bitcoin exchange or Gmail 2FA you are vulnerable. A programmable hardware token is a much safer option.
Read more:
- Duo Security vs Protectimus
- 10 Most Popular Two-Factor Authentication Apps Compared
- How to Backup Google Authenticator or Transfer It to a New Phone
- The Pros and Cons of Different Two-Factor Authentication Types and Methods
- Two-factor authentication for Windows 7, 8, 10
- Time Drift in TOTP Hardware Tokens Explained and Solved
- 10 Steps to Eliminate Digital Security Risks in Fintech Project
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!