Recently the Internet has become an integral part of our lives. The network offers many incredible opportunities such as communication, shopping, paying bills, and various entertainments. But unfortunately not always and not everyone uses the Internet for the good of society. Due to the rapid development of numerous resources, many types of fraud have arisen that aim to obtain confidential data and use it further for personal profit. The main ones are phishing, vishing, smishing, pharming. However, to protect you personal data on the internet it’s enough to use elementary data protection rules and to know how to recognize the common threats and how to combat them. And this exactly what will be discussed in this article.
Phishing
 Phishing is one of the most commonly used methods of Internet fraud at this time. It is a kind of obtaining secret information by an attacker who uses the well-known methods of social engineering to make the users to open their personal data themselves. This can be the number and code of a bank card, phone number, login, password, and email address from certain services. Mainly phishing is used to get access to users’ online banking accounts or e-wallets, with the further possibility of funds withdrawal to the fraudster account.
Phishing is one of the most commonly used methods of Internet fraud at this time. It is a kind of obtaining secret information by an attacker who uses the well-known methods of social engineering to make the users to open their personal data themselves. This can be the number and code of a bank card, phone number, login, password, and email address from certain services. Mainly phishing is used to get access to users’ online banking accounts or e-wallets, with the further possibility of funds withdrawal to the fraudster account.
So how does phishing work?
A user gets a phishing-message to his mailbox that, first of all, affects his emotions. For example, this can be a notification about a big win or, on the contrary, the notification about hacking the account with the further suggestion to follow a phishing link and to enter the authorization data. A user goes to the provided resource and ‘gives away’ his login and password to the fraudster who, on his part, quickly operates with the information received.
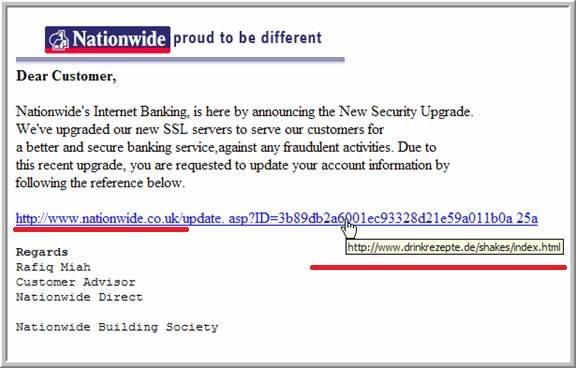
There are several specific examples of Internet phishing:
- Attackers send out millions of messages on behalf of a well-known company to various emails with the request to confirm their login and password. When you click the provided URL you can see the authorization page that is absolutely identical to the page on the original resource. The trick, most likely, is hidden in the link to the site. The domain should be very similar to the real one but differ in several symbols. A similar kind of phishing messages can be also found in different social networks.
- Phishers can use shortcomings in the SMTP protocol to send emails with the fake “Mail From:” line. Responding to such a letter the user sends the answer directly to the offender.
- It is also necessary to be cautious during participating in Online Auctions and sales since the goods offered for sale even though the legal resource can be paid through a third-party fraudulent website.
- Many users face fictitious Internet organizations that request donations.
- Online shops with extremely accessible prices for branded goods can also be counterfeited. As a result, there is a chance to pay for a product that will never be received since it never existed.
| Read also: Top 7 Tips How to Protect Yourself from Phishing Scams
Vishing
 Vishing (vishing – voice+phishing) is another variety of phishing that also uses methods of social engineering, but with the help of a phone call.
Vishing (vishing – voice+phishing) is another variety of phishing that also uses methods of social engineering, but with the help of a phone call.
This is how attackers, let’s call them “vishers”, usually act:
The user receives a phone call, for example, from the bank employee and the operator warns him that his banking card will be blocked if the full information about the card including its number, CVV-code, etc. is not provided by phone right now. A trustful client hearing such a ‘threat’ immediately panics and can give out all the personal data right up to the verification code.
During the vishing attack, the user can also be offered a purchase with a huge discount or informed about the win in any lottery. There is no point to enjoy such a bargain or such an advantageous prize, it is always worthwhile to double-check the information provided by referring to official resources.
So it is necessary to remember to check everything. It is well worth to politely say goodbye to the person on the other end and to check the provided information with a call to the hotline of the bank, they will provide you with more accurate information.
In any unclear situation, the main thing is not to panic. Remember – you can always check everything. Politely say goodbye to the person you are talking to and call the hotline of the organization whose representative the caller introduced himself. So you can easily understand if the call was real, or you almost became a victim of vishing.
| Read also: The Most Common Ways of Credit Card Fraud
Smishing
 Another type of cheating through communication services is smishing (smishing – sms+phishing). This criminal scheme aims to bring the user to follow a malicious link from the SMS message.
Another type of cheating through communication services is smishing (smishing – sms+phishing). This criminal scheme aims to bring the user to follow a malicious link from the SMS message.
A Smishing message can have a form of notification from a well-known bank, familiar company or it may be an information about sudden winning a lottery etc. In the case of SMS to detect a trick is more difficult than with phishing via email, because the messages are short and have not so much information except for the link itself.
Most likely it can be an offer to click the link and enter data or just call or send back the message that would bring extra expenses. It’s is necessary to remember that any such message should be cause for concern. Never reply to such kind of SMS messages and double-check the information with a call to the hotline of an actual service.
Pharming
 Fraudsters understand that classic phishing should become less effective in the near future. A lot of users are already aware of the danger they can face on the various resources and keep the security rules. In consequence of this an absolutely new type of fraud, called pharming, was invented. Its main principle is a secret redirection of users to third-party websites.
Fraudsters understand that classic phishing should become less effective in the near future. A lot of users are already aware of the danger they can face on the various resources and keep the security rules. In consequence of this an absolutely new type of fraud, called pharming, was invented. Its main principle is a secret redirection of users to third-party websites.
So how does pharming work?
The main peculiarity of pharming is the unobvious substitution of the original website for fraudulent, allowing an attacker to acquire the confidential user’s data. All this is done by using the DNS cache on the end user’s device or on the provider’s network equipment. After the exchange, the attacker should only wait until the client authorizes on a certain resource.
The virus turns on its activity only at the moment when the user opens the necessary page. Usually, pharming is applied to online banking or other payment systems through which money transactions are performed.
It is rather difficult to be secured from pharming as the site substitution process goes unnoticed. Pharming software can work both from the browser cache and directly as a virus on your PC. Thus, to protect yourself from pharming, you need not only to learn to recognize phishing emails, but also be careful when installing the software. It is necessary to be extremely cautious when reading emails, and when downloading any software from the Internet.
| Read also: 9 Data Protection Tips for Safe Online Shopping
How to protect yourself from Phishing, Vishing, Smishing, Pharming
How not to get caught on the hook of hunters for profit? First of all, you should always follow the following recommendations when using the Internet and any other communication resources:
- Every time pay attention to the sender and subject of the message. If they look suspicious, just delete these emails or SMS;
- Do not click the suggested links in emails and messages from an unknown sender;
- Never reply to messages requesting personal information;
- Watch for mistakes in the text, if you find them, most likely the letter is a hoax;
- Files attached to an unknown message that have .exe, .msi, .bat, .pif, .com, .vbs, .reg, and .zip extensions can install malicious software, there is no point to open them.
It would not be superfluous also to pay attention to the following possibilities of protection from phishing, smishing, vishing, and pharming:
- The most popular browsers such as Mozilla Firefox, Google Chrome, Microsoft Edge, Safari, have antiphishing systems with a list of malicious sites and this system warns the user about the visit to a malicious site. Similar antiphishing systems are used on many other resources such as social networks, etc.
- Antivirus software provides a quite reliable protection. It is only necessary to install updates on time. These updates allow preventing the virus infiltration on the device and alert the users when they follow malicious links.
- Various spam filters that are used by email services automatically sift messages received from phishers.
- Be sure to use two-factor authentication wherever it’s possible. If all your accounts are additionally protected with one-time passwords, this will complicate the lives of intruders. The lifetime of the one-time password is limited – no more than 60 seconds, so to gain access to the user account, the phisher needs to be more inventive and fast. It’s not so easy to get your login and password, and one-time password at the same time and still have time to enter your account or to make an illegal transaction in such a short time.
| Read also: 10 Most Popular Two-Factor Authentication Apps Compared
Conclusions
So, what is the difference between phishing, vishing, smishing, and pharming – these so similar, but still different types of Internet fraud? The main goal is the same for all of them – to fetch confidential information, mainly through redirecting users to fake websites. But this is done in different ways:
- In phishing – via e-mail.
- In vishing – by means of a phone call.
- In smishing – via SMS.
- In pharming – by using the DNS cache on the end user device or the network equipment of the provider.
How to protect yourself from phishing, vishing, smishing, pharming? Do not click on links in letters and SMS messages, do not use unlicensed software and do not download software on unfamiliar websites, use trustworthy browsers and antiviruses, activate two-factor authentication, do not trust every first caller and always recheck the information.
Read more:
- General Data Protection Regulation Summary
- How to Backup Google Authenticator or Transfer It to a New Phone
- The Pros and Cons of Different Two-Factor Authentication Types and Methods
- Ransomware – to Pay or Not to Pay
- Which messaging apps are trustworthy?
- Malvertising: Can It Be Stopped?
- How to Choose and Use Strong Passwords
- Email hacking protection
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!