> Ubuntu: Configuring Two-Factor Authentication for Secure Access
Ubuntu: Configuring Two-Factor Authentication for Secure Access
With Protectimus multi-factor authentication (MFA) solution, you can set up Ubuntu two-factor authentication (2FA) in a few steps and securely protect your Ubuntu users’ accounts from unauthorized access.
1. How Ubuntu Two-Factor Authentication (2FA) Works
After you enable Ubuntu two-factor authentication, your users will enter two different authentication passwords at the same time to get access to their Ubuntu accounts:
- The first is a standard password (the one the user keeps in memory);
- The second is a temporary password valid only for 30 or 60 seconds (this code is generated with the help of a 2FA token or a 2FA app on a user’s phone – a device that the user owns and has to carry with them).
This way, the Ubuntu account becomes protected with two different authentication factors. Even if the hacker steals the one-time password using phishing, brute force, social engineering, data spoofing, or any other way, they can’t get access to the Ubuntu account without the one-time password from a user’s 2FA token.
This guide shows how you can set up Ubuntu two-factor authentication (2FA) using Protectimus RADIUS 2FA component for the integration with Protectimus Cloud 2FA service or Protectimus On-Premise MFA Platform.
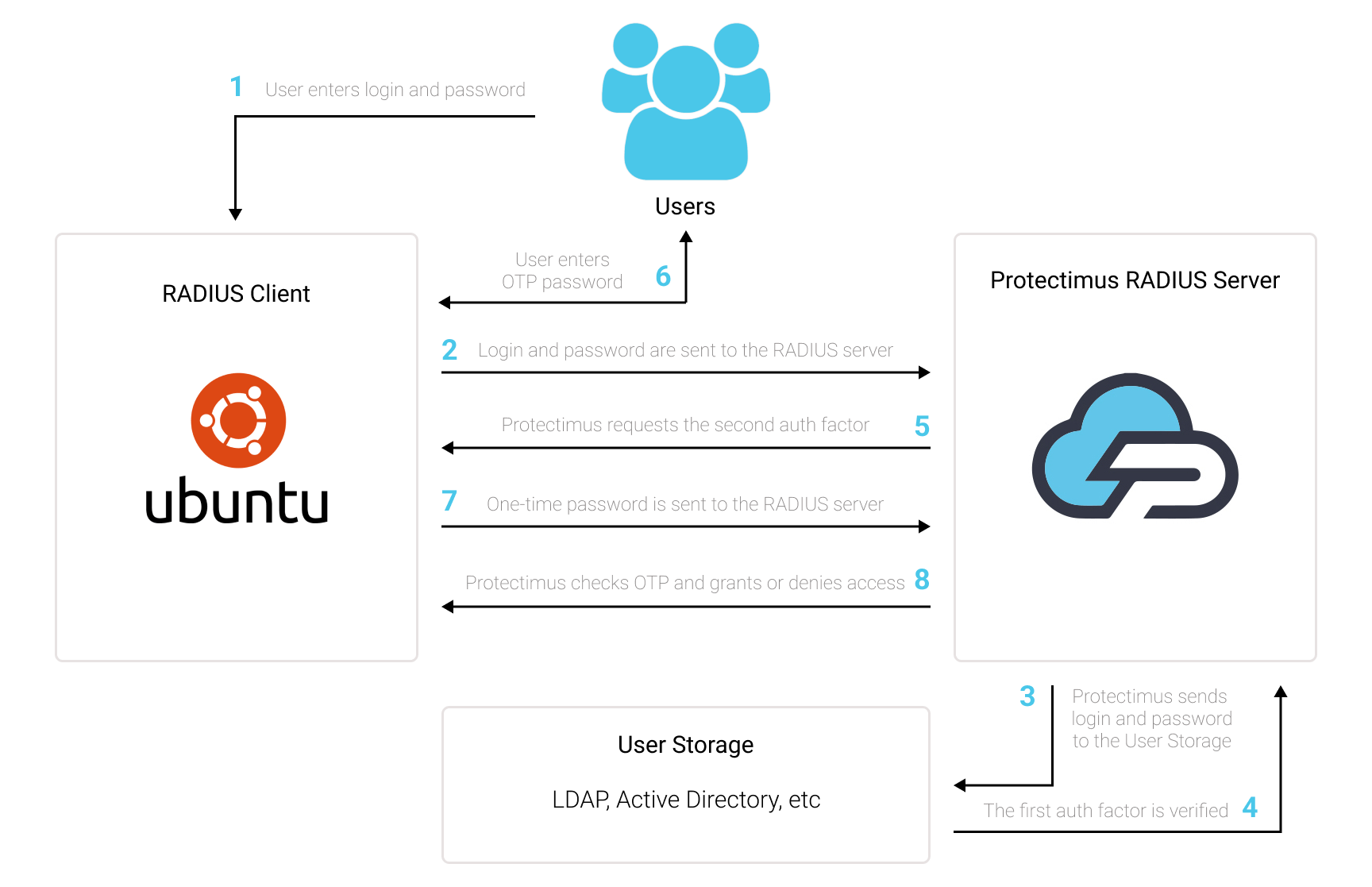
2. How to Enable Ubuntu Two-Factor Authentication (2FA)
You can set up Ubuntu two-factor authentication (2FA) with Protectimus using the RADIUS protocol:
- Get registered with Protectimus SAAS 2FA Service or On-Premise 2FA Platform and configure basic settings.
- Install and configure Protectimus RADIUS Server.
- Configure Ubuntu Settings.
2.1. Get Registered and Configure Basic Protectimus Settings
- Register with the Protectimus Cloud Service and activate API or install the Protectimus On-Premise Platform (if you install Protectimus Platform on Windows, check the RProxy box during the installation).
- Add Resource.
- Add Users.
- Add Tokens or activate Users’ Self Service Portal.
- Assign Tokens to Users.
- Assign Tokens with Users to the Resource.
2.2. Install and Configure Protectimus RADIUS Server
Detailed instructions for installing and configuring the Protestimus RADIUS Server are available here.2.3. Configure Ubuntu Authentication Settings
apt install libpam-radius-auth vim /etc/pam_radius_server.conf# server[:port] shared_secret timeout (s)
127.0.0.1 secret 1IMPORTANT! Use your platform IP instead of 127.0.0.1
SSH
vim /etc/sshd/sshd_configChallengeResponseAuthentication yesLocal authentication + OTP via Protectimus
vim /etc/pam.d/ssh# Standard Un*x authentication.
@include common-auth
auth required pam_radius_auth.soAuthentication + OTP via Protectimus
vim /etc/pam.d/ssh# Standard Un*x authentication.
#@include common-auth
auth required pam_radius_auth.so
GUI
/etc/pam.d/gdm-passwordauth required pam_radius_auth.so