> Comprehensive Guide to Managing Resources
Comprehensive Guide to Managing Resources
Resources serve as a means to group Users. For example, if you need to protect the users of various web projects or the employees of different departments, you may add several Resources.
The number of Resources (projects) that you may create depends on the Service Plan you select. If you need to create more Resources, please select the desired or required number of Resources by customizing your Service Plan.
1. How to Add a Resource
- Login to your account in Protectimus SAAS Service or On-Premise Platform and go to the Resources page.
- Click the Add Resource button.
- This will take you to the Resource adding page, where you’ll need to specify just a Resource Name and click Save, the remaining parameters are optional.
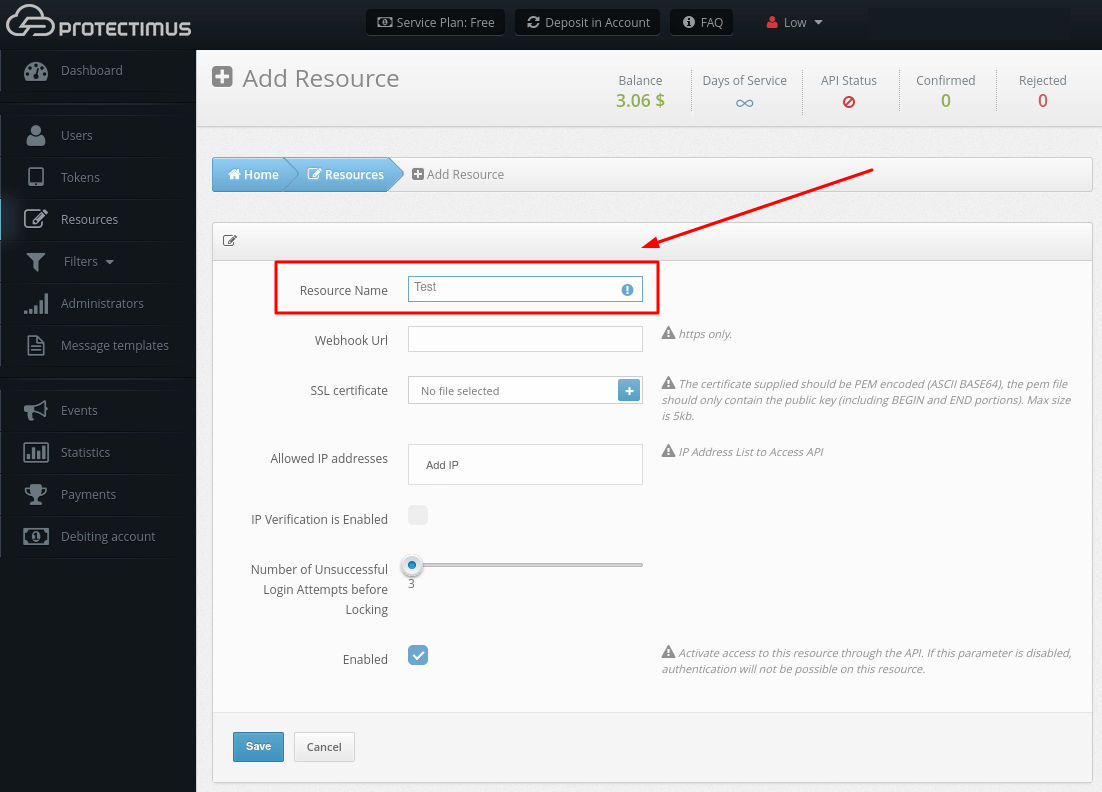
- Webhook URL. Whenever there is an update for the Resources, we will send a POST request containing a JSON update to the specified webhook URL. In case of an unsuccessful request, we will give up only after a reasonable amount of attempts. Currently, webhook is used to receive the result of INTERACTIVE authentications. INTERACTIVE authentications are supported by Protectimus Bot token.
- SSL certificate. The public key certificate certifies the belonging of the public key to the indicated webhook. The certificate supplied should be PEM encoded (ASCII BASE64), The pem file must contain only the public key beginning with “—–BEGIN CERTIFICATE—– ” and end with “—– END CERTIFICATE —–“
- Allowed IP Addresses. Allows you to restrict access to the system only from trusted IP addresses.
- IP Verification is Enabled. Enables the restriction of access to the system only from trusted IP addresses.
- Number of Unsuccessful Login Attempts before Locking. The value of this parameter should be specified between 3 and 10. If a User or Token is not authenticated successfully, the number of failed authentication attempts will be increased for this User. When the threshold number of failed attempts for the specified Resource is exceeded, this User will be locked. A User can be unlocked through the web interface or the API (the edit user method). If a User is authenticated successfully, the number of failed authentication attempts will be set at zero, if the threshold number of failed attempts for the specified resource is not exceeded, and if this User has not yet been locked.
- Enabled. Allows you to enable or disable the Resource.
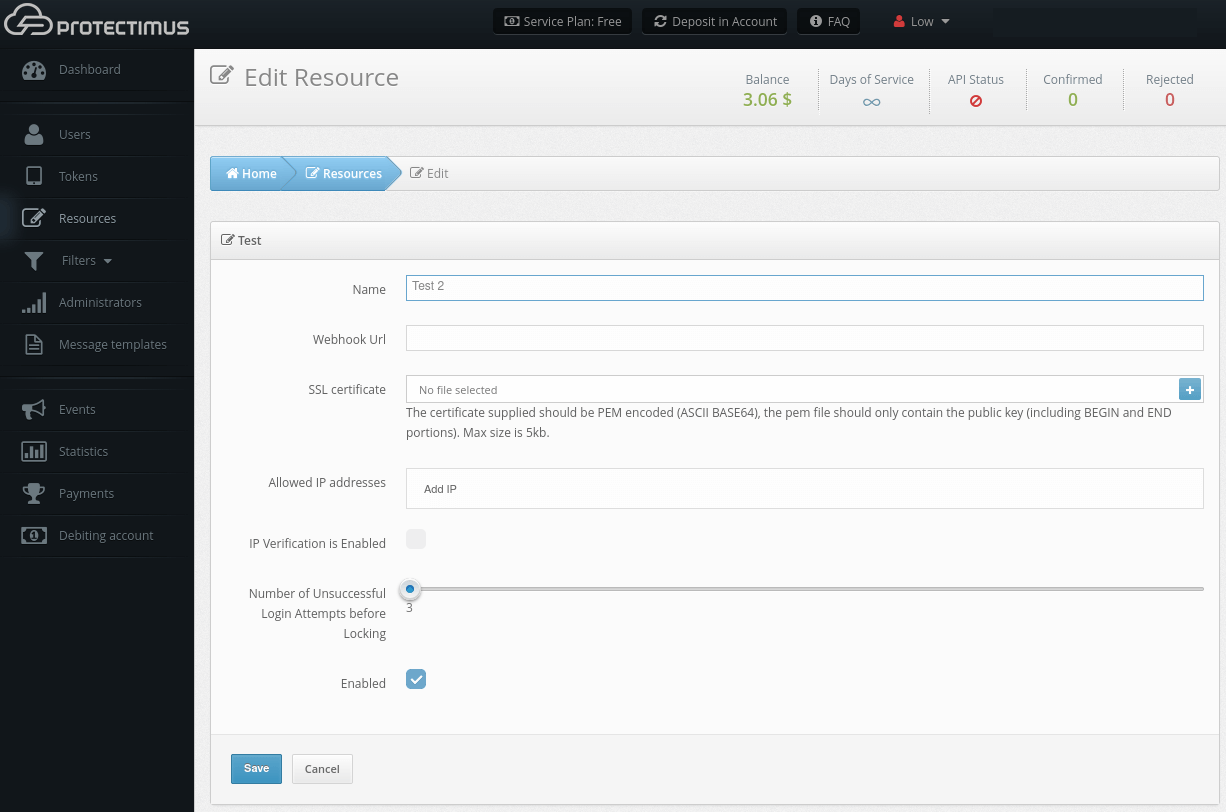
2. How to Edit a Resource
- Go to the Resources page.

- Select the desired Resource and click on the blue button on the right.
- You will be taken to the Resource settings page where you can make changes.
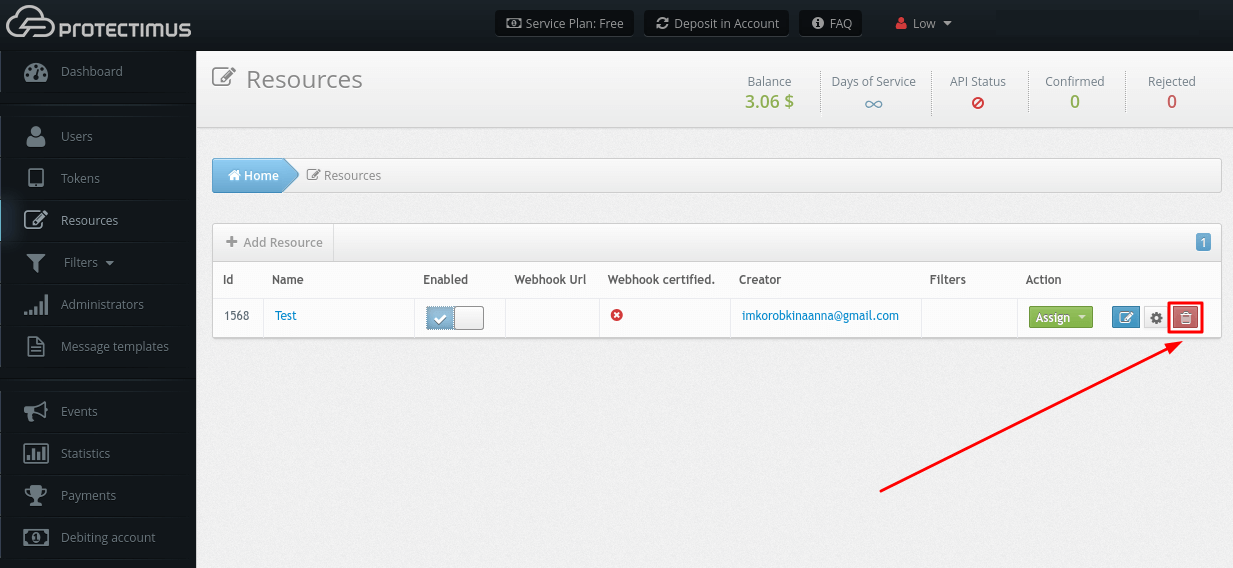
3. How to Delete a Resource
A Resource may be deleted only by the Administrator who created it or by the chief system administrator.
- Go to the Resources page.

- Find the Resource you are going to delete, click on the red button with the image of the bin.
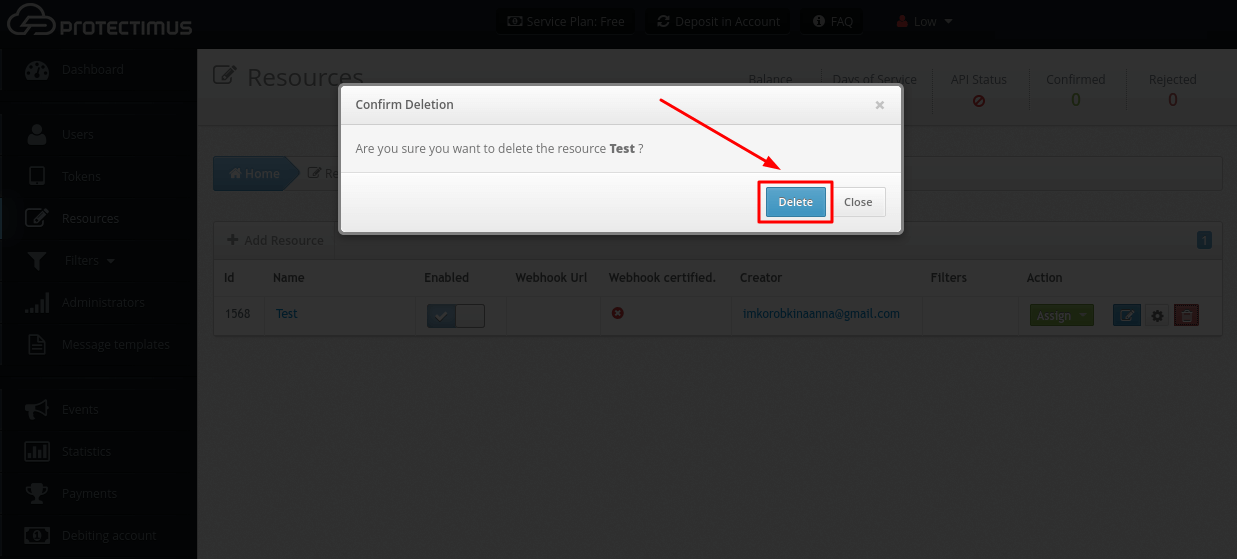
- Confirm the action.
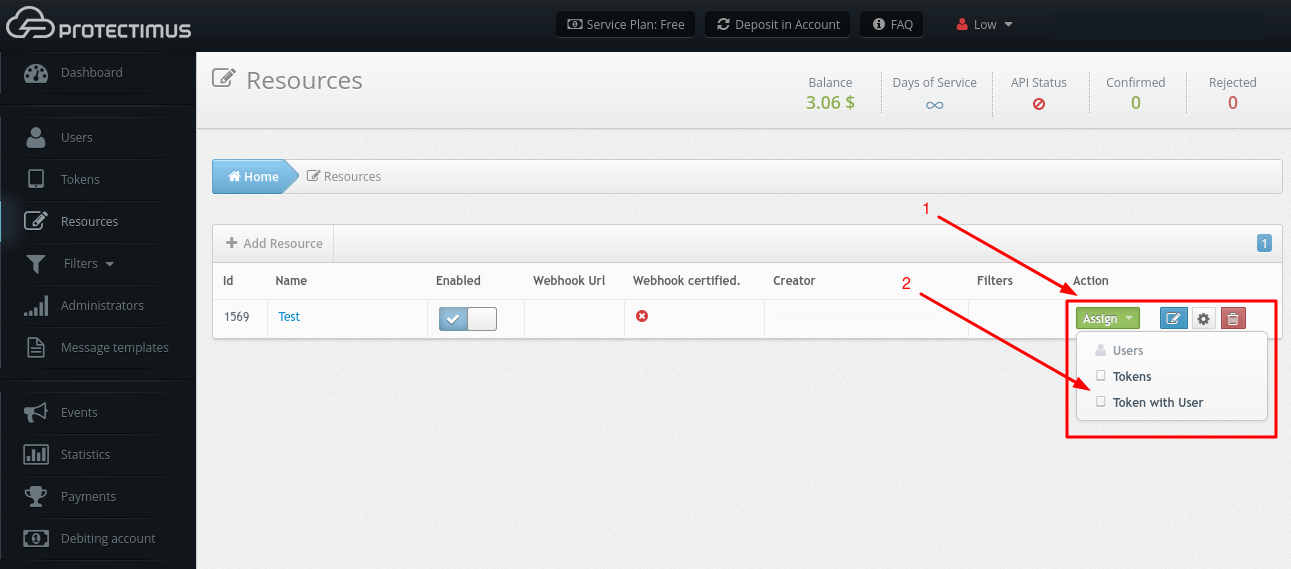
4. How to Assign Users and Tokens to Resource
Users and Tokens must be assigned to the Resource, otherwise Users will have no access to this Resource and Tokens won’t work. The method of assigning a User to a Resource depends on the authentication method selected. Protectimus supports several user authentication methods:
- User authentication with a static password. This method requires that a User should have a password, and that this User should be assigned to the Resource.
- User authentication with a one-time password. This method requires that a User should have a Token, and that this User should be assigned to a Resource WITH this token. This method will not work if a User and a Token are assigned to a Resource separately from each other.
- User authentication with a static password and a one-time password. It is a combination of the two methods described above. A User must be assigned to a resource WITH a token. This User must have a password. If a User’s Token is deactivated, OTP authentication will not be performed, in which case only this User’s static password and this User’s compliance with the filters’ requirements, if any, will be authenticated.
- Token authentication on a resource. This method allows you not to assign a Token to any specific User, but simply to verify the validity of a one-time password generated by the Token. This method requires that a Token should be assigned to a Resource.
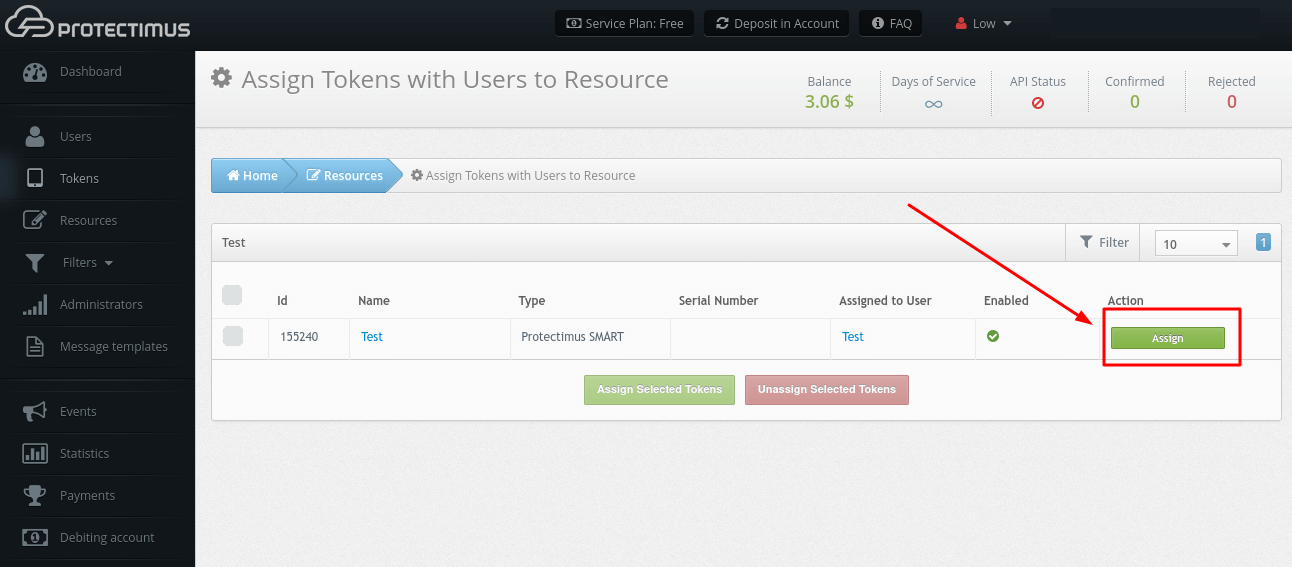
- Go to the Resources page.

- Find the Resource you need, click Assign, then Token with User (make sure that you’ve already assigned your Tokens to Users).
PLEASE NOTE! You may assign only Users or only Tokens if you choose User authentication with a static password or Token authentication on a resource.
- Select the Tokens that should be assigned to the Resource and click Assign.
Last updated on 2025-03-12
