> Securing Cisco Switches with Two-Factor Authentication
Securing Cisco Switches with Two-Factor Authentication
This Cisco Switches 2FA guide shows how to add two-factor authentication for Cisco Switches Login with the help of Protectimus 2FA Service or On-Premise 2FA Platform.
Protectimus two-factor authentication system communicates with Cisco network equipment using the RADIUS protocol. The Protectimus RADIUS Server component acts as a RADIUS server. It accepts incoming authentication requests via the RADIUS protocol, contacts the user storage (Active Directory, etc.) to verify the login and password, and then contacts the Protectimus 2FA server to verify the one-time password. If both authentication factors are correct, the Protectimus RADIUS Server allows the user to login.
The scheme of work of the Protectimus solution for Cisco switches two-factor authentication is shown below.
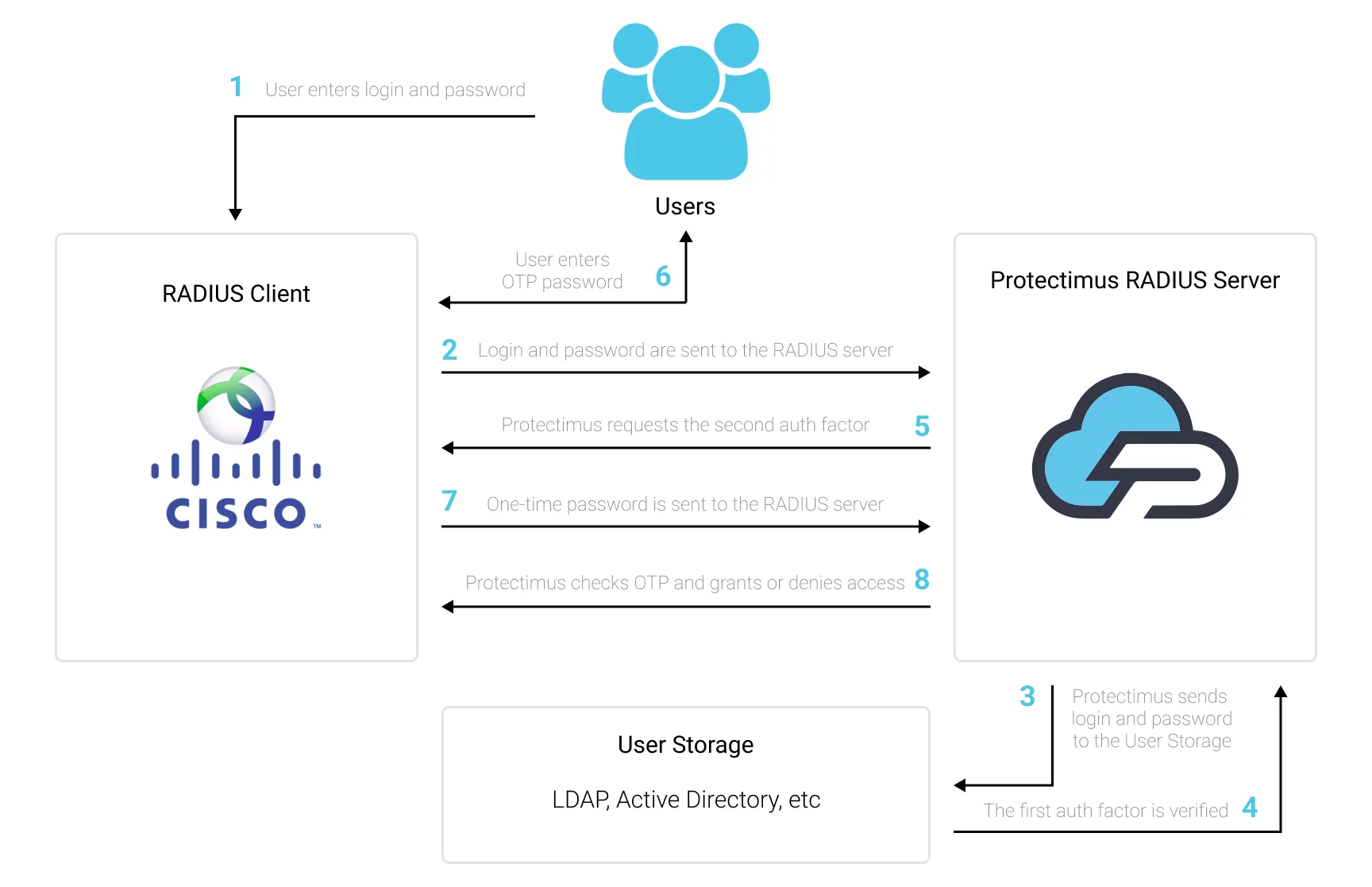
1. How Cisco Switches 2FA Two-Factor Authentication (2FA) Works
When you set up two-factor authentication for Cisco Switches, you make your users enter two different factors of authentication when they get access to the Cisco Switch.- The first authentication factor is a login and password (something the user knows);
- The second authentication factor is a one-time passcode generated with the help of a hardware 2FA token or a smartphone (something the user owns).
After you enable two-factor authentication (2FA) for Cisco Switches login, it becomes too hard to hack it. It’s almost impossible to get both authentication factors at the same time. Moreover, a one-time passcode validity time is only for 30 seconds, so the intruder will have too little time to hack the second factor.
Tho-factor authentication (2FA / MFA) is an effective protection measi=ure against such cybersecurity threats like phishing, social emgeneering, brute force, keylogging, MITM attacks, data spoofing, etc.
2. How to Enable Cisco Switches Login 2FA
You can set up Cisco Switches two-factor authentication (2FA) with Protectimus using the RADIUS protocol:
- Get registered with Protectimus SAAS Service or install the On-Premise 2FA Platform and configure basic settings.
- Install and configure Protectimus RADIUS Server.
- Configure Cisco Switches authentication policies.
2.1. Get Registered and Configure Basic Protectimus Settings
- Register with the Protectimus Cloud Service and activate API or install the Protectimus On-Premise Platform (if you install Protectimus Platform on Windows, check the RProxy box during the installation).
- Add Resource.
- Add Users.
- Add Tokens or activate Users’ Self Service Portal.
- Assign Tokens to Users.
- Assign Tokens with Users to the Resource.
2.2. Install and Configure Protectimus RADIUS Server
Detailed instructions for installing and configuring the Protectimus RADIUS Server for Cisco Switches 2-factor authentication using RADIUS are available here.2.3. Add Protectimus as RADIUS Server for your Cisco Switch
- Add Protectimus as a RADIUS Server.
Switch(config) #radius server [configuration-name]
Switch(config-radius-server) #address ipv4 hostname [auth-port integer] [acct-port integer]
Switch(config-radius-server) #key [shared-secret]- Associate your RADIUS server with a server group.
Switch(config) #aaa group server radius [group-name]
Switch(config-sg-radius) #server name [configuration-name]- Configure aaa authentication login to use RADIUS group with a fallback to local authentication.
Switch(config) #aaa authentication login [default | list-name] group [group-name] localIntegration of two-factor authentication (2FA/MFA) for your Check Point VPN is now complete. If you have other questions, contact Protectimus customer support service.
