> Office 365: Securing Your Microsoft Environment with Two-Factor Authentication
Office 365: Securing Your Microsoft Environment with Two-Factor Authentication
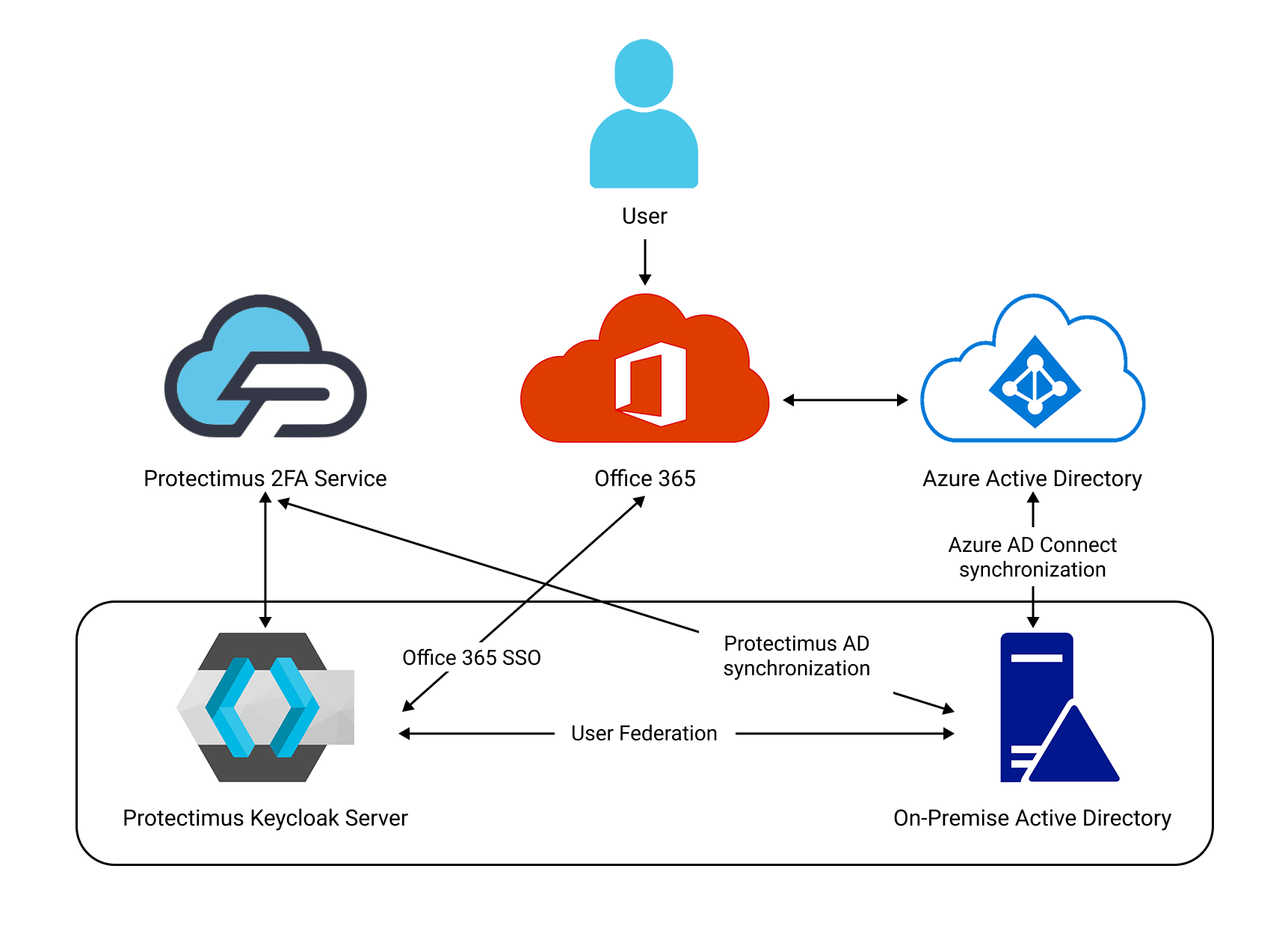
Protectimus two-factor authentication (2FA) system supports an SP (Service Provider) initiated Single Sign On (SSO).
This means that your end-users will have the ability to sign into their accounts directly from the protected resource login page. When the end-user tries to sign into a protected resource, an authorization request is sent to the Identify Provider (Protectimus). Once the Protectimus authenticates the user’s identity, the user is logged into their account in the protected resource.
A scheme of interaction of Protectimus On-Premise Two-Factor Authentication Platform with Microsoft Office 365 through Keycloak is presented below.
1. Get Registered and Configure Basic Settings
- Install the Protectimus On-Premise Platform and get registered with Protectimus.
- Add Resource.
- Add Users.
- Add Tokens or activate Users’ Self Service Portal.
- Assign Tokens to Users.
- Assign Tokens with Users to the Resource.
2. Synchronize your On-Premise AD with Azure AD
2.1. Open office.com
Admin -> Show all -> Azure Active Directory -> Custom domain names -> “Add custom domain”In DNS, you need to create a TXT record to confirm adding a domain to Azure AD.
2.2. Download and run the Azure AD Connect
https://www.microsoft.com/en-us/download/details.aspx?id=47594Continue -> Customize -> Install (No checked options) -> Password Hash Synchronization -> Next -> Connect to Azure AD:
username@[something].onmicrosoft.com pass:
Next -> Add Directory -> domain
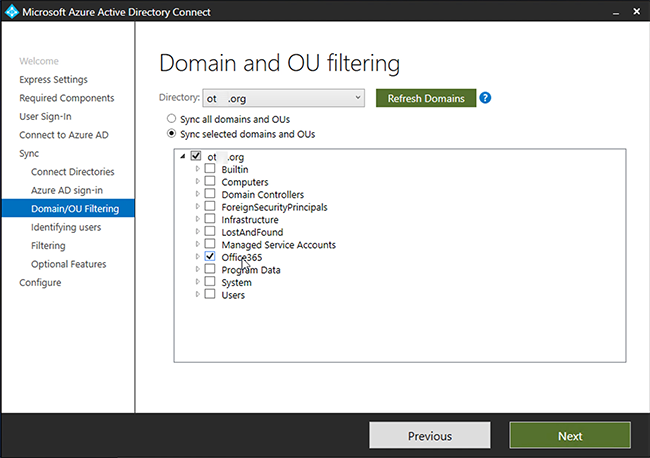
You can create a separate Organizational Unit (OU) for users whose accounts must be protected with two-factor authentication and set up synchronization only for this OU. Every User in this OU must have an email, it will be used as a UPN (User Principal Name).
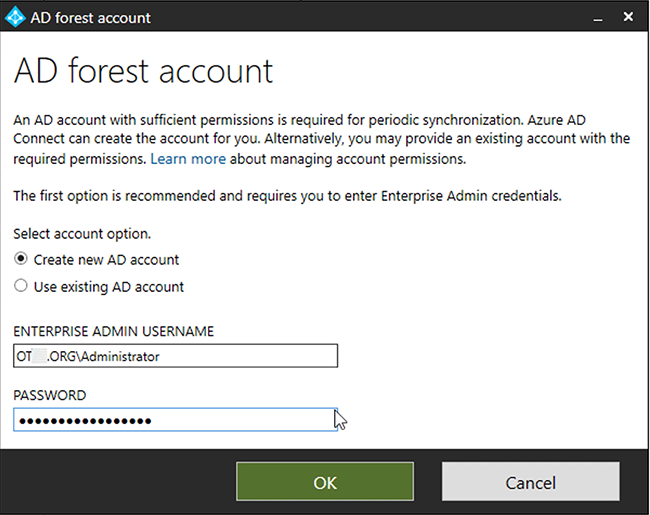
- Create new AD account
- Enterprise ADMIN username: domain\Administrator
- PASSWORD: Windows AD Administrator password
Next -> Next -> Sync Selected Domain
Next -> Next -> Next -> Exit.
3. Configure Keycloak
3.1. Create Realm
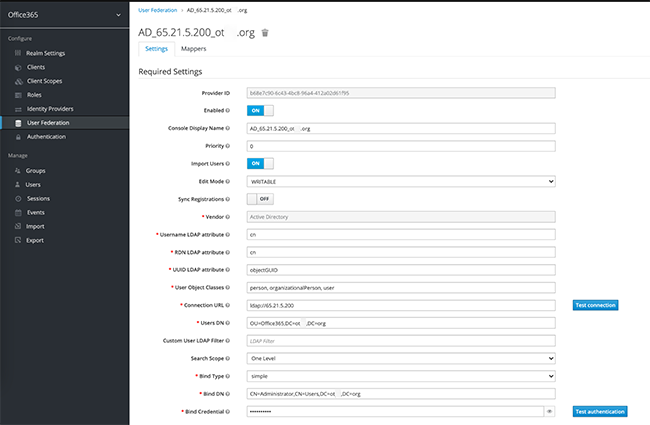
Add Realm, for example, name it Office3653.2. Create User Federation
Add Mapper:- Name: saml.persistent.name.id.for.urn:federation:MicrosoftOnline
- Mapper Type: user-attribute-ldap-mapper
- User Model Attribute: saml.persistent.name.id.for.urn:federation:MicrosoftOnline
- LDAP Attribute: objectGUID
- Read Only: ON
- Always Read Value from LDAP: ON
- Is Mandatory in LDAP: OFF
- Is Binary Attribute: OFF
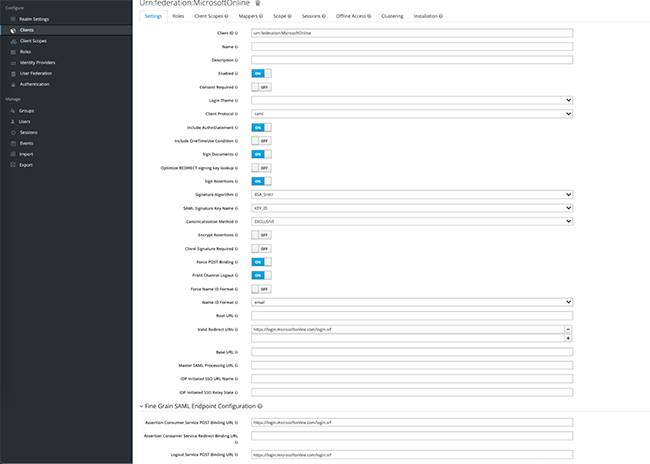
3.3. Create a client
- To do this, import this file when creating a client:
https://nexus.microsoftonline-p.com/federationmetadata/saml20/federationmetadata.xml
ATTENTION! It is important to name the file: “urn:federation:MicrosoftOnline”
-
Edit the client properties:
- Client Signature Required – Disable
- Signature Algorithm – “RSA_SHA1”
-
Create a Mapper for the client “Add builtin” -> X500 email
- Mapper: Name: IDPEmail
- Mapper Type: User Property
- Property: email
- SAML Attribute Name: IDPEmail
4. Connect Office 365 with Keycloak
4.1. Get SAML certificate
First of all, you need to get a SAML certificate and check it using this URL:https://kc.dev.protectimus.com/auth/realms/[realm name]/protocol/saml/descriptor
Or check the certificate using the corresponding feature in the interface – SAML keys.
4.2. Install the required software
- Install-Module -Name AzureAD
- Install-Module MSOnline
4.3. Connecting Office 365 with Keycloak
Execute the following script:# get the public key certificate from keycloak
# https://kc.dev.protectimus.com/auth/realms/2608/protocol/saml/descriptor
# see X509Certificate
$cert="MIICoTCCAYkCBgF3Y+nVLjANBgkqhkiG9w0BAQsFADAUMRIwEAYDVQQDDAlvZmZpY2UzNjUwHhcNMjEwMjAyMTgwMTQ0WhcNMzEwMjAyMTgwMzI0WjAUMRIwEAYDVQQDDAlvZmZpY2UzNjUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC3eE+GuP2ubqH0C2sceb1iBsPr5LNIK0dtW67CQPL2tLM0YlRAFXu2sWRMKwPl8ZULvMzufA855j0Chd5KX1izVi8c6fclqge+OB9iMB05Ew/zGb8zmCXETgVU9+lsQFchd8M/I/i0QKKOatIbP50t9SKJI5daX78wb/IVk2pexB76cqXaQrrddh9ksXo3OFyFpAk1xlCC9Nu77QLCPWK4fBnSEbnzxDP3ZMhPXMQsn3MbD1SHGmHmJ93wMeXFGGIU77aDI/uAYZj1tb7dj/aICqG8RpUVXEolf8BDH/nT2TonYSmMaSqd99wCNJaKJWpyPd2qid7118DtOyPzZza/AgMBAAEwDQYJKoZIhvcNAQELBQADggEBAFglY4CdTJkGTL7/YUY1uBhSTSGvtbv6GiQ+2Uox3JVNVECB1Za63mUU1tTC/r4Jp02jRnTtBfSR7Sra+HDIKgAOkwcVTh2P++i1bk7PiY1Rb2ePrBtXWnb0GC8qCLAOK7b2/y9E1K5Wjg2Qg1dxnNZFys8CLpHkkYwMwChJA6E8DMg/bWUYfighBo4mAUpORAwqkmEB2mC39VbWZAUyBysQ5Cb9xK8RWnOgj7XhZfhpihK815z+uwirQjOFmGhWs2Mxk9PHkPkCFeWdcGGoRPvBuVYaG5/MrWu5hqQFtiu4ZDsySEnBdUqfudD6Iorc6QHVYf6VCunSIdE9L9sIovs="
$uri="https://kc.dev.protectimus.com/auth/realms/Office365/protocol/saml"
$issuer_uri="https://kc.dev.protectimus.com/auth/realms/Office365"
$dom="yourdomain.com"
$cred = Get-Credential
Connect-MsolService -Credential $cred
Set-MsolDomainAuthentication -DomainName $dom -Authentication Federated -ActiveLogOnUri $uri -SigningCertificate $cert -PassiveLogOnUri $uri -IssuerUri $issuer_uri -LogOffUri $uri -PreferredAuthenticationProtocol SAMLPYou can check if the operation has been performed successfully:
Get-MsolDomainFederationSettings -DomainName domain.name4.4. Disconnecting Office 365 and Keycloak
Execute the following script:$dom="yourdomain.com"
Set-MsolDomainAuthentication -DomainName $dom -Authentication managedEverything is ready, open office365.com and try to log in with an account from AD.
Last updated on 2025-03-16