Remote work is a blessing for some people and a real curse for others. In this article, we have collected all the tips to help you organize remote work in your company. We are talking about task trackers, modern communication tools, and the organization of remote access to corporate servers at the same time. We used all our experience to make this difficult task easier for you.
What’s important, when organizing a home office for your employees, you should think about cybersecurity. We are ready to help you with risk management to avoid potential hacker attacks and protect all remote network connections from third-party interference. In this article, you’ll find all the answers to feel safe during the COVID-19 remote work (if you’re wearing your mask appropriately, of course).
2020 changed the usual routine for many companies. IT giant Microsoft has sent over 80% of its employees to work from home. Amazon, Facebook, Google, Uber, Twitter, Apple, are no exception. The part of our team is working remotely as well.
Some business owners perceive this trend as a real challenge, forcing them to make difficult decisions. We propose to consider this as an opportunity. What if you’re already optimizing your resources and learning about new remote workstation software? It’s time to use absolutely all resources so that the inevitable economic crisis does not become a blow to your company.
Table of contents
- Tools you need for remote work
- IT security threats you should be aware of to work remotely
- Cybersecurity: Where do you start?
Tools you need for remote work
Organizing the work at home, you should provide your employees with all the necessary tools:
- the software they will use to access their workplaces remotely, such as RDP and VPN clients, etc.;
- tools they will use to work with the documents remotely, such as cloud services;
- and services they will use for communication, such as messaging apps, video conferencing software, task managers, and CRM.
Let’s delve deeper into this topic and understand what exactly do you need.
Software for remote access
The first thing you should think about is what will your employees use while working from home? If your team uses corporate laptops, they can simply pick them up from the office for the quarantine period. But what if they are used to working with desktops? Don’t panic, it’s 2020. Remote access is not rocket science these days.
Before you get your feet wet, remember that each OS has its characteristics, and you should consider them:
 | Windows. All you need is the Microsoft Remote Desktop which is used to open access to the computer remotely over RDP (Remote Desktop Protocol). It should be already available in your operating system. If not, install Remote Assistance from Microsoft. We explain how to set up an RDP connection securely here. |
 | macOS. Apple users can use a regular Screen Sharing app, Chrome’s remote desktop connection, or third-party programs. |
 | Linux. TeamViewer, AnyDesk, and similar software are perfect for working under this operating system. |
Note that large companies can go even further. Citrix, VMWare, and Cisco offer cool infrastructure solutions to help you manage your remote work successfully. Of course, it doesn’t go about free software, they are much more expensive. But they surely pay off with your safety.
Cloud services for remote work
Most likely your employees deal with numerous files and folders every day. If they still save their docs to the desktop, it’s time for a change. Storing documents on the computer is not convenient and creates an extra security risk. Imagine that your employee’s computer can fall into the wrong hands. A thief will easily get to files that are stored on the hard drive.
Developing a security policy and remote work rules, you should categorically forbid all users to store documents on their desktops. Any work file must have its place in the cloud. Cloud services are one of the most useful tools you need. Firstly, they are safe, and it is easy to protect them with MFA. And secondly, they’re just pretty convenient for daily routine tasks.
 |  |
The most popular solutions are G Suite or Office 365. They handle a huge amount of tasks. For example, your employee Peter creates a word processing document, spreadsheet, or presentation. Peter doesn’t store any of these files on his computer but relies entirely on the cloud. If Peter needs to stay at home for self-isolation purposes, he always has access to such documents, wherever he is. Moreover, Anna, his colleague from another country, has this access too. Anna can open the latest version of any presentation at any time, make corrections, or leave a comment for Peter with fresh ideas.
Moreover, cloud services usually offer some additional tools to plan your day and track current tasks. You can also benefit from audio and video calling tools to stay in touch with colleagues.
And of course, your G Suite, Office 365, or any other software account must be secured with 2-factor authentication. The best level of cybersecurity is achievable with Protectimus Slim NFC or Protectimus Flex hardware tokens.
Messaging apps for remote work
Our team is constantly exchanging messages, and yours? It’s incredibly convenient because you need to stay in touch, discuss projects, and brainstorm new ideas together. Especially if you work from self-isolation or from different parts of the world and are deprived of the opportunity to chat while drinking coffee in the office.
Of course, there are a million various messaging apps out there. But you need a systematic approach, which means the most convenient solution. Small teams feel good on Telegram. But if you have more team members and need different channels (for example, Marketing, Design, Offtopic, etc.), you should opt for Slack. Video conferencing requires Skype or Zoom.
If you do not want your confidential data to be transmitted and stored on the servers of other companies, use RocketChat. This is an open-source solution that is installed on the company’s servers and all messages and files do not leave the company’s internal network. You can choose from both free and paid plans, depending on your needs.
Agree on rules for communicating in the app and make sure every employee sets it up. You can organize one general chat for free communication, as well as several chats for projects and current tasks. Respect each other’s time and organize calls only if there is a pool of tasks that need to be discussed in voice mode. But don’t ignore calls and video conferencing altogether, as they help your team communicate better in isolation.
Task managers and Customer Relationship Management systems
We’re not reinventing the wheel by telling you to use the task manager. It can be Trello, Asana, Jira, or another service of your choice. If you still do not work with similar programs, try them right now. They are essential for projects with milestones, responsible employees, deadlines, etc.
A similar tool exists for effective work with clients. This is CRM. Try Zoho, Bitrix, Creatio, depending on your company’s size, customers’ pool, and your tasks.
 |  |
 |  |  |
Each solution has its advantages and is suitable for projects with different goals. For example, if you need to track development milestones, rely on Jira. Trello is a great place to start because it’s simple and intuitive. And so on.
Software for video calls, presentations, and conference calls
You have no opportunity to meet with your team in person, but that does not mean that you should cancel all meetings. Even interviews can be conducted online if you have appropriate software like Zoom or Skype.
Talk about important issues with your voice and turn on the camera to create a more engaging atmosphere. Keep holding meetups, weekly planning meetings, conferences, as they help you stay a team regardless of the world situation and working conditions.
| Read also: 10 Basic BYOD Security Rules
IT security threats you should be aware of to work remotely
Working from home offers a huge number of benefits for employees, and the main one is saving time. But while your team rejoices at the opportunity to sleep an hour longer in the morning, you need to think about the threats that could interfere with the workflow.
Be prepared for the fact that such a work format is associated with an increased risk of a company’s data leakage. You cannot find out how each employee’s computer is configured, how technically competent Peter or Anna is, and how many of their relatives or friends also use this computer. This ignorance opens up a lot of opportunities for attackers who want to harm your company.
While the whole world is suffering from the crisis and trying to adopt new standards of life, hackers feel happy. As long as you and other entrepreneurs transfer your businesses online, they feel like a duck to water here as having hacked one home computer, a hacker can easily gain access to the whole corporate network.
If the home computer of your employee is poorly secured, be sure attackers will find a way to hack it. That’s why it is important to know about the most common threats and ways to confront them.
Leakage of confidential information
Here are some situations that lead to leakage of confidential information:
- An employee’s PC is infected with malware that infects a corporate server when connected to a remote desktop.
- The team member is not prepared for social engineering, man-in-the-middle, or phishing attack.
- An employee has lost one’s device with an open remote work connection
- The device stopped working and required repair, there is always a slight chance that the computer repair technician will save all the data from the device or even from your corporate network if the user can access it remotely.
- All family members use a single account on your employee’s home computer. They may not necessarily intend to harm you, but they are unlikely to be aware of your security standards.
All of these situations are real, and they can happen to any company that is not protected enough. That’s why you should make sure that your team is educated enough. Develop a good security policy and regularly organize awareness training. Make it a mandatory part of your work routine.

Malware
You cannot think that one computer infected with a virus is harmless. You know that the strength of a chain is determined by the strength of its weakest link. Of course, this will lead to infection of the entire corporate network. The worst part is that there is an endless list of virus source options. For example, Peter decided to download a movie using a torrent. Or Anna accidentally clicked on a link in a phishing email. The virus may remain unnoticed for a long time, but it will make itself felt. How can this situation be avoided? Make sure every team member has a quality antivirus. Buy licenses for all of them, because you are interested in the security of their data. Another important aspect is the security policy. Read on to find out how to make up with these rules.

Unauthorized access
If the user sets a weak password for their account and doesn’t use two-factor authentication, hacking one’s account may be pretty easy for a professional attacker, who will use a brute force technique, first of all.
Another major threat is keyloggers – malware that intercepts and collects usernames and passwords.
Though sometimes the hackers don’t even have to use any software for that. What if your employees just left all their passwords on a piece of paper next to the computer? In the office, such situations occur less often, but at home, they pose a real threat.
| Read also: Reddit was hacked: how it happened, who the victims were, and why SMS authentication failed
Cybersecurity tips for remote working: where do you start?
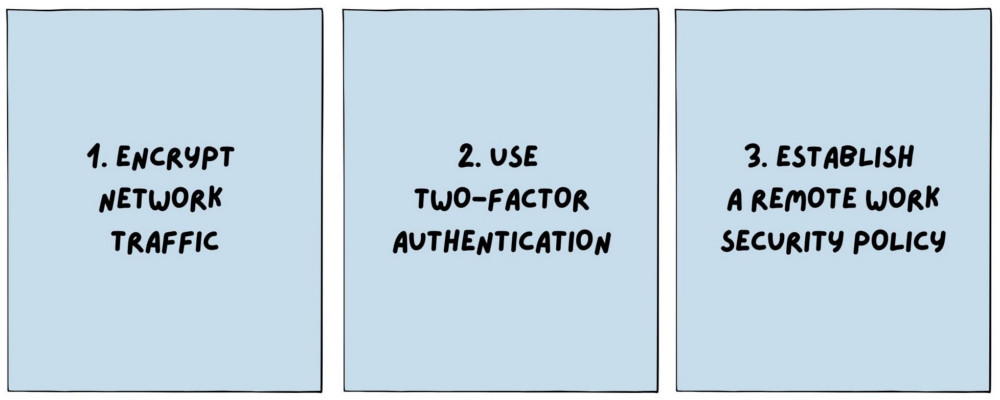
There are 3 main cybersecurity tips to follow:
- Always encrypt network traffic when connecting to remote workstations;
- Use 2-factor authentication without exceptions and excuses;
- Establish a work from home policy, include it in a standard employee’s contract, and train your employees to avoid basic cybersecurity threats like phishing, social engineering, etc.
Remote work connection protection
If you set up remote access to your team PCs, the connection must be protected. Use any method of encrypting your network traffic, such as an encrypted VPN, or at least standard encryption features, for example, the Microsoft Remote Desktop app offers such.
Two-factor authentication when working remotely
Whatever service your employees use, they must activate two-factor authentication. This is a reliable barrier that breaks all plans of intruders, protects you from keyloggers and brute force attacks.
Even if hackers succeed with phishing or other illegal methods, two-factor authentication will help prevent the consequences of such interference. It is irreplaceable if your employee’s relatives have access to a computer or someone has received a list with usernames and passwords.
Two-factor authentication must be configured for all critical nodes:
- Take care of the remote desktop first. Protect the RDP connection with 2FA, configure Citrix and VMWare two-factor authentication via RADIUS, etc. You’ll find the two-factor authentication solutions for Windows logon and RDP here and more info about the 2FA integration via RADIUS that will help you to protect Citrix and VMWare here.
- Add two-factor authnetication to your VPN client, learn how to integrate Protectimus two-factor authentication to any VPN client via RADIUS here.
- Encourage your employees to enable built-in two-factor authentication for macOS or install Protectimus Winlogon for Windows. The step-by-step guide on installing Protectimus Winlogon is available here.
- Instruct the team to enable two-factor authentication when working with any cloud services. Read how to protect Office 365 accounts with hardware tokens here, and how to add hardware OATH token to Azure MFA here.
- Generate one-time passwords with hardware tokens. Learn more about universal programmable OTP tokens Protectimus Flex, which will fit all your two-factor authentication needs here.
How to set up two-factor authentication for RDP
- Download the Protectimus Winlogon & RDP installer
First of all, go to the Protectimus Winlogon & RDP landing page and download the installer and a setup manual.
- Register with the Protectimus Cloud service.
Go to https://service.protectimus.com/en/ and get registered.
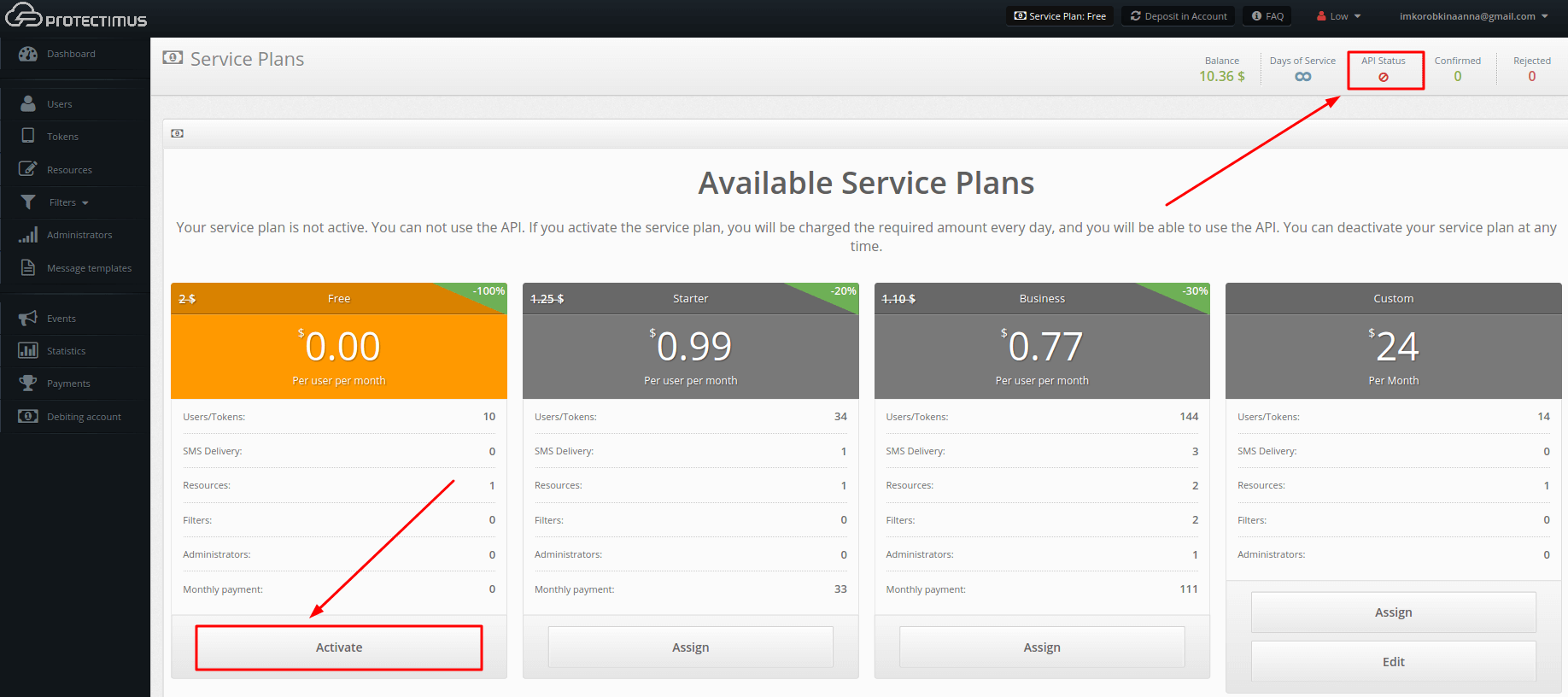
- Choose and activate the Service Plan.
Start with the Free service plan for testing purposes, you can always change the service plan if you need to protect more than 10 users.

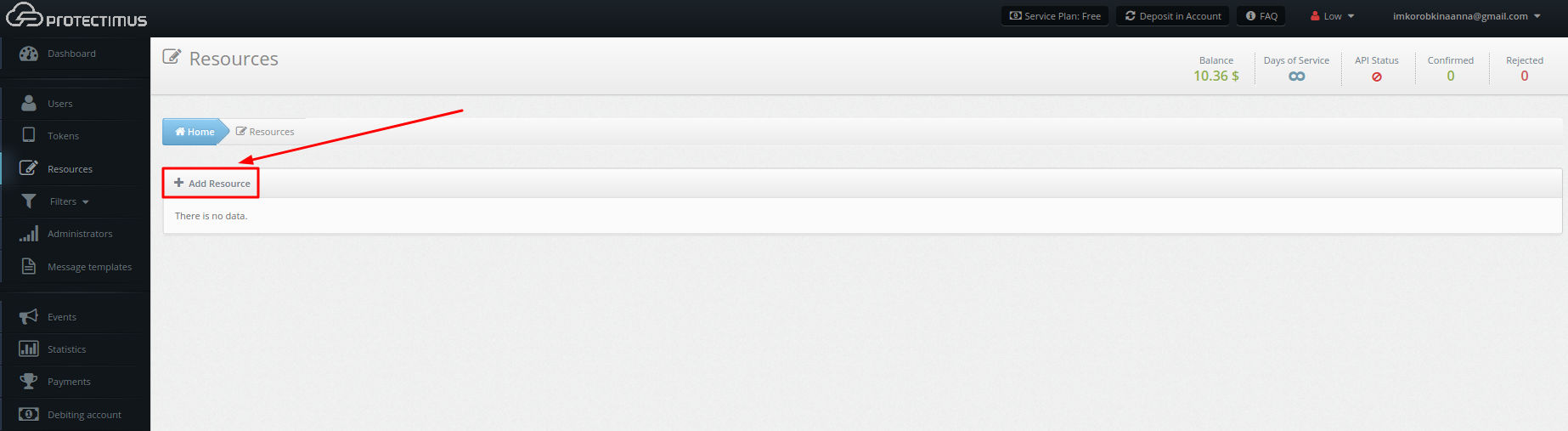
- Add Resource.
Go to Resources and add a resource. It’s enough to indicate just the Resource Name.

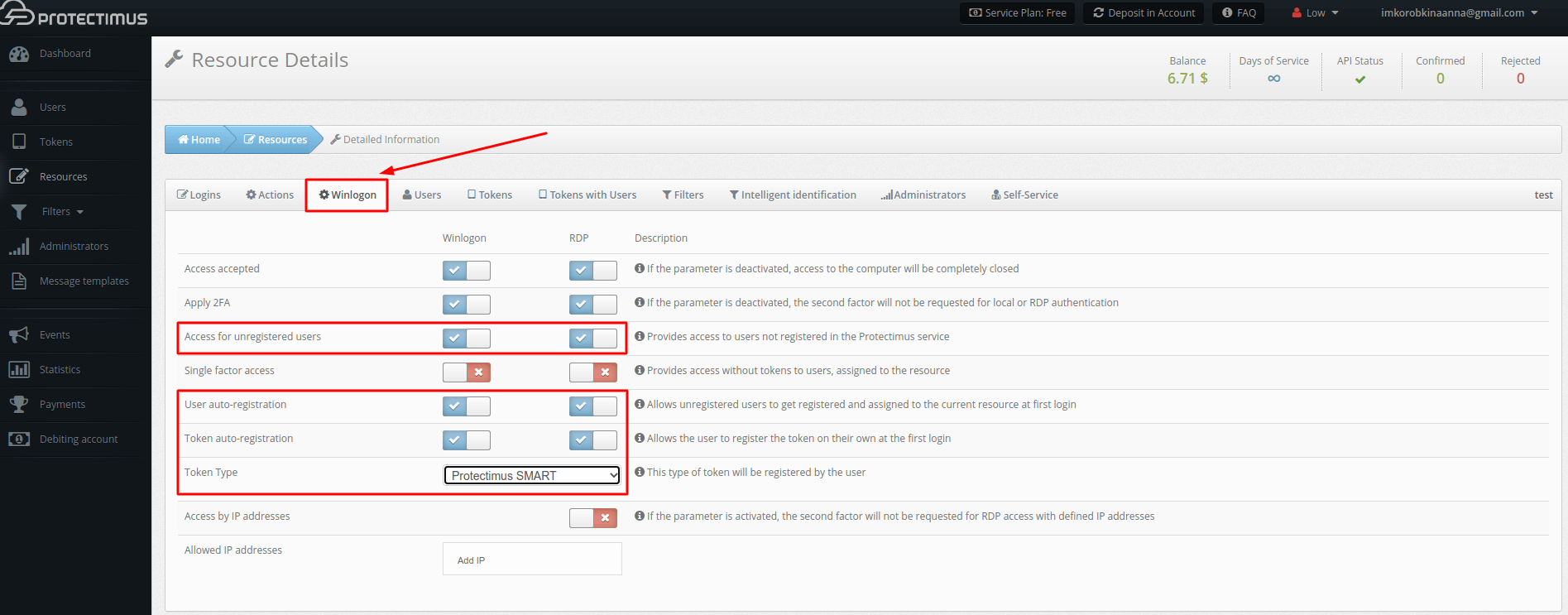
- Enable Users’ and Tokens’ auto-registration
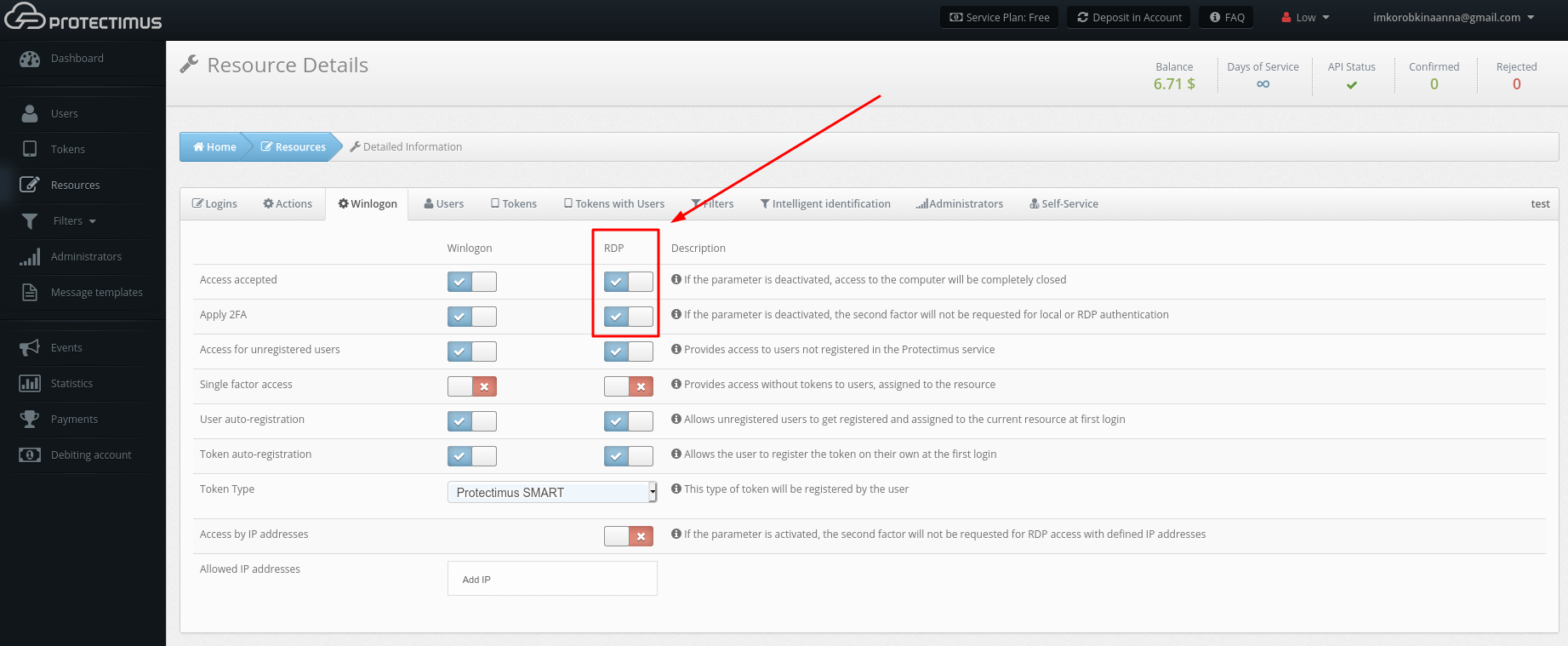
Go to the Resources page, click the name of the resource, open the Winlogon tab, and mark the following options:
– Access for unregistered users
– User auto-registration
– Token auto-registration
– Select the Token Type your users will add
- Enable two-factor authentication for RDP. This means that every time your users will connect to this computer via RDP, they’ll have to enter a one-time password.
On the Winlogon tab, make sure that the access over RDP and two-factor authentication for RDP are enabled.

- Install the Protectimus Winlogon & RDP component you’ve downloaded on your computer.
Run the Protectimus Winlogon installer as administrator.
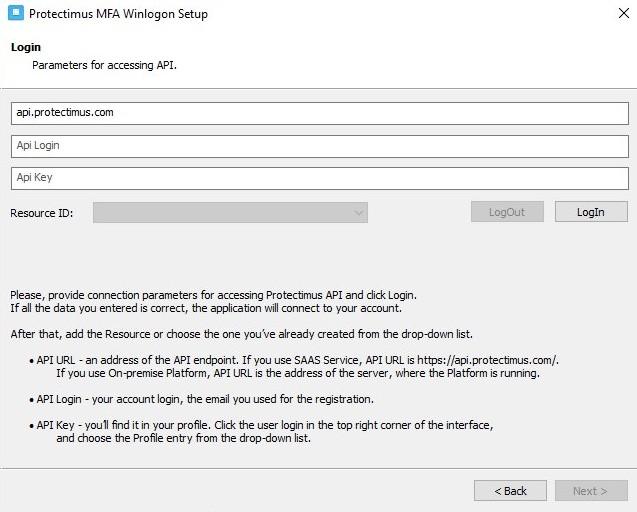
The installation process is intuitive, just click Next every time until you see the page where it’s necessary to indicate API URL, API login, and API key:
– API URL. Use https://api.protectimus.com/.
– API Login. This is the login you chose when registering with the service (that is, your email).
– API Key. You’ll find your API key on the Profile page. To navigate to this page, click on your username in the upper-right corner of the interface. Then, choose “Profile” from the drop-down list.
When you are done with all these fields, click Login.
Then choose the required Resource ID – the ID of the resource you’ve created before the installation.
You can find additional details in the Protectimus Winlogon setup manual that you’ve downloaded.
How to choose OTP tokens for work from home
If you want the most reliable way to protect your employees and yourself, take care of hardware tokens for all team members. Below you’ll find a table with a comparison of available options of hardware tokens for Windows and RDP, G Suite, Office 365.
| Token | Features | Fits |
 |
|
|
|
|
|
|
|
|
| Read also: The Pros and Cons of Different Two-Factor Authentication Types and Methods
Remote work security policies
First of all, speak to the team! They feel relaxed because they know that IT-managers have their back. It is your task to explain to them why they must be more responsible and strictly follow the security policy. Don’t provide them with an option, set up security rules, and make them obligatory. The safety of the entire company is at stake.
Your security policy may include the following points:
- If possible, set up a home office that no one else has access to;
- Maintain a clean desk policy, do not leave any paperwork or paperwork with working notes;
- Always lock screens or turn off devices when not in use;
- Set strong passwords and use two-factor authentication;
- Keep work and personal gadgets separate;
- Connect via VPN to encrypt your internet connection;
- Remember your privacy;
- Use only reliable Wi-Fi networks.
Find the time and money for the required IT security training while working remotely. There is no point in modern solutions if one of your employees has not heard of phishing, vishing, smishing, pharming, or malicious advertising. Unsafe Wi-Fi network? All passwords in one file? Don’t expect them to be responsible and well-aware of all these issues. It is your job to control it, so provide your people with all the information they need.
Besides, make sure your team has all the required software including antivirus software, VPN, etc. They should have a thorough understanding of how to work with documents, keep in touch with colleagues, track tasks, or give presentations. You may already be familiar with most of these tools, but it’s never too late to rethink the pool of programs that are obligatory for the work tasks.
Don’t think that we want to scare you or dissuade you from transferring the company to remote work. Our goal is to make our business more informed and secure. By understanding that all of your departments and employees are protected, you can focus on your priorities and take your business to the next level.
Communication plays an important role here. It is not enough for you to understand the threats and risks to the company. All team members should monitor their online activity and minimize the risk of their data being compromised.
| Read also: 4 Reasons Two-Factor Authentication Isn’t a Panacea
Conclusions
Nobody knows how long the pandemic will last or when you will return on vacation. It is important to understand that working from home is our new reality. And it is your task to make it as safe as possible.
Basic safety rules are relevant to any work environment. For this reason, we recommend that you discuss the threats of phishing and social engineering with employees, oblige them to regularly change passwords, and monitor the data they share on social media. If you have encountered difficulties in transferring your team to remote work, you can always write to us at [email protected]., and we will try to help you with this.
Read more
- 10 Steps to Eliminate Digital Security Risks in Fintech Project
- 10 Windows Computer Safety Tips
- 9 Must-Follow Gmail Security Rules
- Why US, Canadian, and EU Universities Choose Programmable Hardware OTP Tokens
- How to Add Two-Factor Authentication to Outlook Web App (OWA)
- Active Directory Two-Factor Authentication
- On-Premise 2FA vs Cloud-Based Authentication
- Two-Factor Authentication Solutions Comparison: Google Authenticator vs. Protectimus
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.










2021-02-08
It’s cool you mentioned the RocketChat. I consider it the safest messaging app for corporate use as you can install it on your own servers, which means no need to share sensitive data with any third-party company. We use it for two years already and are quite satisfied. It’s also an advantage that we can make our own improvements as RocketCha is open source.
2021-02-13
Hi Anna, I agree with you that it’s necessary to enable two-factor authentication for all the employees, no matter if they work remotely or not. But when we tried to make 2FA obligatory in our office, some people refused to install Google Authenticator on their cellphones. Understandably, we can’t make the employees install the apps on their personal devices, and it’s too expensive to supply them with corporate phones. Please, advise if your programmable tokens can replace the app? It could be a nice way out for us.
2021-02-15
Hi Soto, sure, if your two-factor authentication system supports a Google Authenticator app, most probably you can connect a programmable OTP token Protectimus Slim NFC or Protectimus Flex instead of the app. You’ll find all the necessary info about how programmable tokens work and how to connect them instead of the 2FA app here: https://www.protectimus.com/blog/programmable-totp-token-protectimus-flex/
Please, note that the secret key should be up to 32 symbols long (in Base32), and you’ll require an NFC-enabled Android smartphone to add the secret key into the token. But you can use one smartphone for all your employees, the app used for programming the tokens doesn’t store the secret keys, so it’s secure. Protectimus Slim NFC and Protectimus Flex function the same way, they only differ in form-factor.
2021-05-17
You have mentioned very interesting points! ps decent internet site.