VPN, or virtual private network, is a popular and proven security tool used by companies across the globe to protect remote access to their corporate networks, especially today when almost every company switched to remote work, at least in part. VPN allows the creation of an encrypted link between a user and the company’s private server. And while this secures the corporate infrastructure from the direct attacks of malicious agents, VPNs themselves are still open to hacker intrusion. Here’s where VPN two-factor authentication comes into play.
Multi-factor authentication, or MFA, mitigates multiple VPN security risks, protecting the VPN from unauthorized access in case of user credentials theft. Let’s take a closer look at how MFA allows you to establish the best VPN security, how you can set up VPN two-factor authentication, and which VPN authentication methods to choose.
Why You Should Add 2FA to VPN Connections
Let’s consider four main reasons you need to secure your VPN connection with two-factor authentication.
1. VPN Two-Factor Authentication Protects Against Phishing Attacks
Among the main reasons you should ensure additional VPN security is the trend of phishing attacks, which are successfully performed by criminals in up to 17% of cases, according to the Duo report.
Phishing is a social engineering technique when a hacker contacts a person either via email, SMS, or a phone call, pretends to be a reputable organization representative, and persuades their victim to provide their credentials. Often the phishing email or message may contain an attachment with malware or a link that leads to the fake website, anyway, the main goal of the hacker, who performs the phishing attack is to get the user credentials.
If the phishing attack is successful, the hacker may get the login and password required to connect to the corporate system through the VPN. Then, the hacker would be able to enter this user’s profile, and install the malware, or steal sensitive data from the server computer.
An extra layer of authentication guarantees that the network cannot be breached by outside players, even if they possess the stolen credentials. VPN two-factor authentication verifies the identity of the user not only by a single password but by a time-based one-time password. It is much harder to steal and use such a one-time password as it’s valid only for 30 seconds, thus guarding against phishing and other security threats (brute force, keyloggers, MITM attacks, etc).
2. Two-Factor Authentication Is Required to Reach the Compliance Conditions
While two-factor authentication is helpful for every company that uses VPN for security, some need it more than others.
The security regulations instruct the companies to ensure a certain security level. For instance, the PCI DSS (Payment Card Industry Data Security Standard) dictates that organizations should actualize two-factor authentication for network access. Using two-factor authentication is also advised for HIPAA (Health Insurance Portability and Accountability Act) conformity.
If you’re in the finance or healthcare sector dealing with sensitive data, VPN 2-factor authentication will help you keep your clients’ data private and make sure it does not fall into the wrong hands.
3. VPN 2FA Helps to Enforce Certain Specific Security Policies
Using VPN two-factor authentication solutions leads to a more controlled and detailed approach to safety. With their help, you can create more detailed and specific security policies that will ensure the safety of your corporate data.
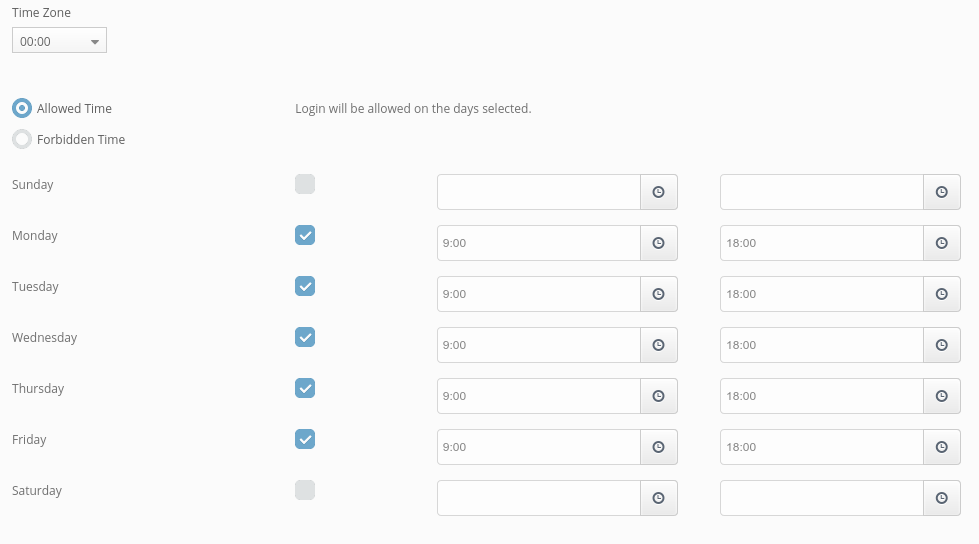
For example, you can limit the access to the network to devices located in a certain region or deny access from certain countries (for example, Russia or China famous for a large number of hacker attacks carried out from the territories of these countries). If you want to further limit the chances of malicious play, you can also set up the time of the day your employees can access their corporate accounts. Overall, the best two-factor authentication VPN solutions are the ones that give you the most control.
4. VPN 2FA Helps to Ensure Consistent Security for On-Premises and Cloud Apps
While VPNs are mostly used to secure the connection to the on-sight applications, more organizations are moving towards cloud solutions. This may create a certain discrepancy in the safety of access to different applications.
2-factor authentication helps to remove this discrepancy and make the security check process consistent and reliable on all fronts. Two-factor VPN access will both be familiar to employees that already use cloud solutions, and will provide an additional level of protection for the on-premise software the cloud applications already have.
| Read also: Remote Work: Dream or a Threat?
How does Two-Factor Authentication Secure Your VPN
VPN two-factor authentication adds another layer of security to the primary method of authentication (password). This additional layer should help to validate the user identity, thus ensuring that a person is unable to access the network using compromised credentials.
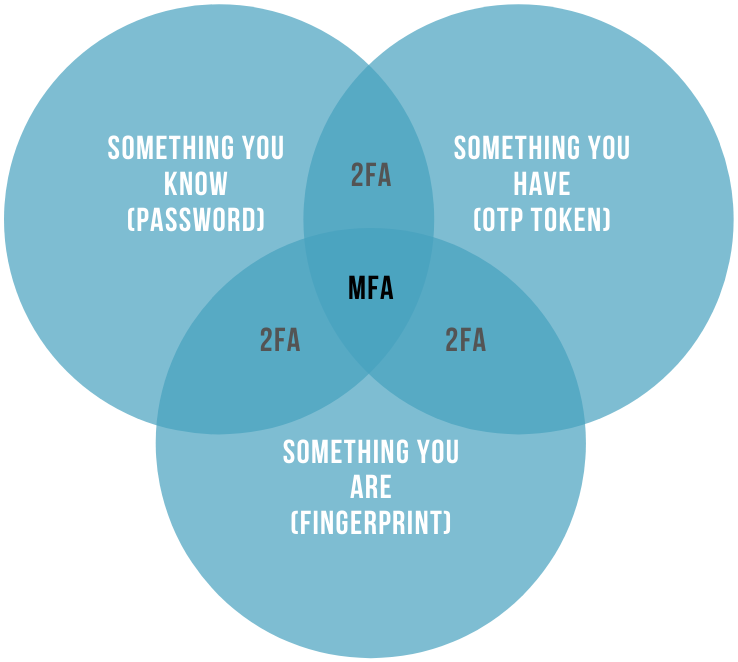
The extra layer of security should differ from the first one by its nature. Then it is very hard to compromise both authentication factors at the same time. Usually, there are three categories of aspects that are used for authentication, namely:
- Knowledge (something the user knows like their password or a mother’s maiden name);
- Possession (something the person has like a phone or an authentication token);
- Inherence (something the user is like a fingerprint or face ID).
If you use a password (something the user knows) as the first authentication factor, then you should use something the person has or is as the second authentication factor.
The type of two-factor authentication for VPN you choose should depend on which one is easier for you to deploy and make your employees use, and which provides the least chances for the malicious agents to break through. Some of the frequently used two-factor authentication methods are authenticators in smartphone applications or programmable and classic hardware security tokens.
| Read also: The Pros and Cons of Different Two-Factor Authentication Types and Methods
Protectimus MFA for VPNs: Features and Benefits
Let’s review what makes Protectimus one of the top two factor VPN authentication solution on the market:
1. Compatible with Most VPN Solutions
Protectimus can be connected to any VPN service with the help of the RADIUS networking protocol using the Protectimus RProxy component. This means that it can be used as a VPN 2FA solution with any service that supports RADIUS. This includes such industry leaders as SonicWall global VPN client and Sophos VPN. Protectimus can also work as Cisco VPN 2 factor authentication and Azure multi-factor authentication VPN.
2. Easy to Use VPN Two-Factor Authentication
While Protectimus is a complex and highly customizable service, it is easy to use for both the administrators and the end-user. It can be quickly integrated into the system either through a ready-made solution for the integration via RADIUS or with Protectimus API. If you have any questions and need assistance with integrating Protectimus two-factor authentication into your infrastructure, our technical support team is always ready to connect and help you with the integration in real-time.
When it comes to the server component, you can choose between using the Protectimus cloud service or setting up a private server (either on-premises or on a cloud two-factor authentication). While the Protectimus service is ready to use right away off the shelf, with an on-premise platform you have more control. So, you can choose the option that better suits your needs.
 |  |
Cloud Service | On-premise Platform |
|
|
3. Various OTP Tokens
Another layer of flexibility Protectimus provides comes with the list of OTP tokens you can choose from. They include:
- Classic hardware tokens (Protectimus Two);
- NFC programmable tokens (Protectimus Slim NFC and Protectimus Flex);
- OTP apps on iOS and Android (Protectimus Smart OTP);
- One-time code delivery via various channels, including e-mail, SMS, and 2FA chat-bots in Facebook, Telegram, and other messengers;
- And even third-party hardware tokens support.
 |  |  |
4. Additional Security Features
- Data Signing (CWYS – Confirm What You See) – OTP passwords generation using data from the user’s current operation. Read more about data signing here.
- Geographic Filters – allow you to grant or deny access based on a certain geographic location.
- Time-based Filters – allow you to grant or deny access during a certain period of the day.
- IP Filter – allows you to grant access only from certain approved IP addresses.
- User Environment Analysis – analysis of users’ browser version, operating system, language, screen resolution, etc., and request a one-time password in the case of mismatch with previous data.
5. Free VPN 2-Factor Authentication Integration Support
Protectimus team is ready to help with the MFA VPN set up online. No matter how complicated your infrastructure is, we’ll gladly help you to secure your VPN, protect your data, and ensure your safety from potential phishing attacks.
Please, get in touch with our support team with any questions you have at [email protected]
Read more
- Two-factor authentication for Windows 7, 8, 10
- How to Add Two-Factor Authentication to Outlook Web App (OWA)
- Active Directory Two-Factor Authentication
- Sophos 2FA with Hardware OTP Tokens
- Hardware Tokens for Azure MFA
- Office 365 MFA Hardware Token
- Keycloak Multi-Factor Authentication With Hardware Tokens
- Two-Factor Authentication Solutions Comparison: Google Authenticator vs. Protectimus
- 6 MFA Myths You Still Believe
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


2021-03-05
Will this solution work for the SonicWall VPN?
2021-03-09
Hi Ariel, sure, you can connect Protectimus two-factor authentication platform to SonicWall VPM via RADIUS protocol. Please, get in touch with our support team at [email protected] for further instructions and help with the integration.