Nowadays, when hackers constantly look for vulnerabilities, while more and more aspects of life are being digitized, cyber security is of utmost importance and every app developer has to pay special attention to access management.
Keycloak is one of the most ingenious solutions created with app developers in mind. It provides an elegant and easy way
With Keycloak comes an easy to roll out Multi-Factor Authentication (MFA) with one-time passwords (OTP). By default, Keycloak multi-factor authentication supports time-based OTP (TOTP) delivered via an authenticator app only.
But for those who want to add an extra layer of security for their users, there is a perfect solution — reprogrammable token Protectimus Slim NFC. This token is, basically, programmed to be utilized as a replacement for the mobile authentication app.
Below we provide detailed instructions on:
- how to configure Keycloak MFA
- how your users will set up their hardware Keycloak token Protectimus Slim NFC
- how to run Keycloak 2FA with other ways of authentication (SMS, email, hardware tokens, chatbots)
Keycloak multi-factor authentication configuration
Configuring Keycloak multi-factor
Enforcing existing user:
Go to your Keycloak admin area, find “Users” in the sidebar menu and select a user from your list. Then navigate to the “Details” tab and select “Configure OTP” in the “Required User Actions” section:
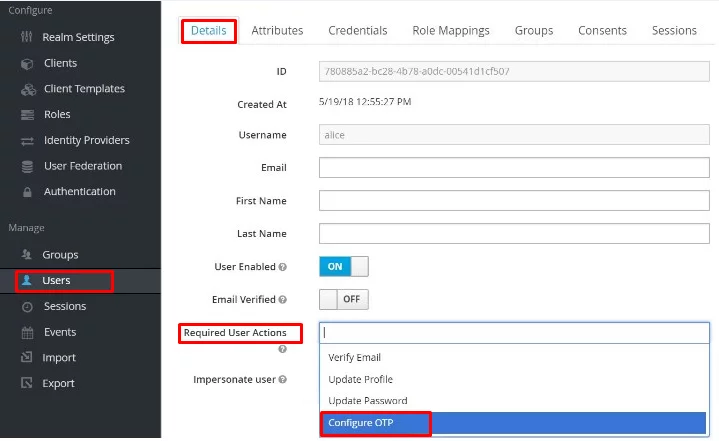
Enforcing new users:
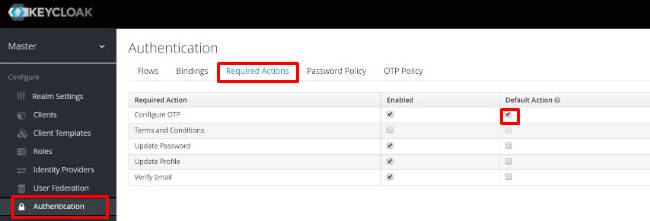
Select “Authentication” in the sidebar menu in the Keycloak admin area, then find the “Required action” tab, in the top row (“Configure OTP”) check “Default action”.
Keycloak two-factor authentication with hardware tokens
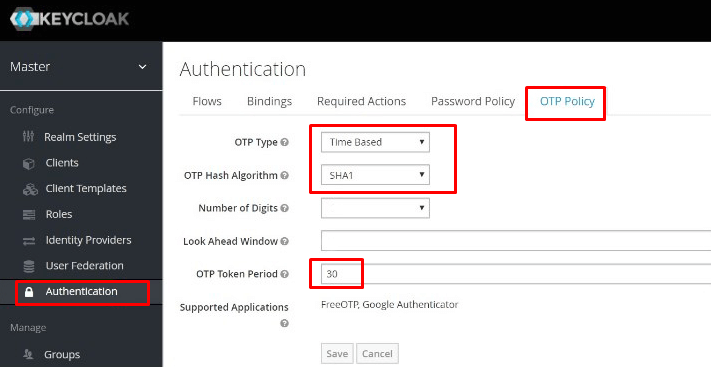
To hook up Protectimus Slim NFC to Keycloak the following OTP Policies have to be applied: SHA1, TOTP, 30 or 60 seconds period.
Find the “OTP Policy” tab in your “Authentication” section in the Keycloak admin area and adjust the required parameters as follows, don’t forget to click the “Save” button:
Now your users will be able to follow these simple steps to add Protectimus Slim as the second factor when logging into your apps or services:
1. Download Protectimus TOTP Burner application.
2. Launch our application, click “Burn the seed”, then select the “Scan the QR code” option:
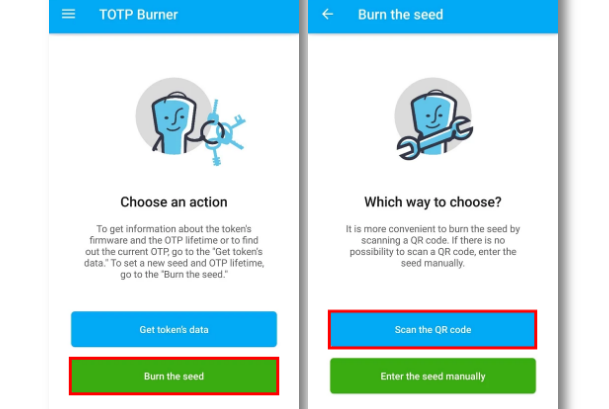
3. After completing the usual login process with username and password the user will have to set up the Mobile Authenticator. This is where they will get the QR code:
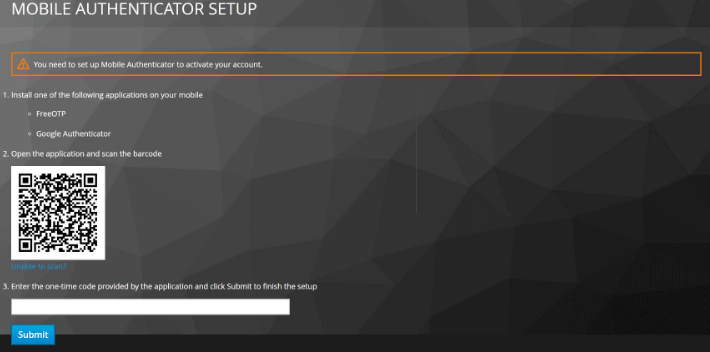
4. After the code scanning is done the user needs to turn the token on, place it within the mobile’s NFC antenna range and click “Continue”:
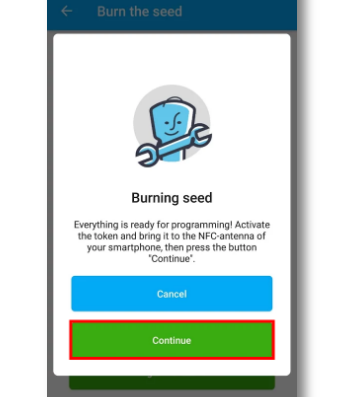
5. After the application provides the confirmation message, Protectimus Slim NFC can be used with your Keycloak protected application or service using Keycloak multi-factor authentication:

Keycloak OTP via SMS, email, hard tokens, chatbots
Out of the box, Keycloak is an awesome solution for managing security and access. But integrating it with Protectimus multifactor authentication service will expand your protection options, provide more features and make your apps and services truly bulletproof.
With Protectimus you will be able to add any MFA method you wish: Keycloak two-factor authentication via email, hardware tokens with hardcoded keys (these are cheaper than the reprogrammable ones), Keycloak 2fa SMS, and even capability to deliver OTP via chatbots in various messengers.
But what’s more important, you’ll get a set of advanced Protectimus 2-factor authentication security features. Let’s take a closer look at the most important features Protectimus authentication solution has to offer.
Data signing (CWYS — Confirm What You See)
This is a very effective way to protect sensitive data from phishing software, Trojans and various other harmful software injections aimed to steal one-time passwords.
CWYS data signing feature generates OTPs in reliance
Geographic filters
By implementing this ingenious filter you can both allow and block entry to users from particular countries of your choosing.
Time-based filters
This feature is great for granting access to corporate environments. With it, you can allow users access only at certain hours, for example — working hours. This way the corporate portal is protected against unauthorized access much better.
Adaptive authentication
This smart feature is great for those who need to constantly log in and out of a system and the access rules are not extremely strict, where some amount of trust is allowed. With this feature on, Protectimus will analyze the users’ environment (OS and language, browser name and current version, resolution of their screen, the presence of certain plugins etc) and will request OTP only if there’s a significant mismatch.
Role-based access policies
This allows for creating different groups of users and assigning different access protocols for these groups in the same Protectimus account. So you can have one type of access protection for end-users and a completely different one for administrators, for example.
Users self-service
By allowing users to handle their own tokens you take the extra work-load off the system administrator and save your funds.
As you can see, integrating Protectimus multifactor authentication service with Keycloak allows for a much more versatile approach to protecting and managing access to your apps and services.
Protectimus is available both as an On-Premise Platform and a Cloud Service, the integration is done via API.
The pricing will pleasantly surprise you, for example, you can have up to 10 users completely free of charge. To learn more about Protectimus pricing plans go here.
Read also:
- The Pros and Cons of Different Two-Factor Authentication Types and Methods
- Office 365 MFA Hardware Token
- Hardware Tokens for Azure MFA
- 10 Steps to Eliminate Digital Security Risks in Fintech Project
- Man In The Middle Attack Prevention And Detection
- 10 Basic BYOD Security Rules
- 4 Reasons Two-Factor Authentication Isn’t a Panacea
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!