If you read this article, you probably know the answer to the “what is OWA” question. But just in case — OWA Outlook is a browser email client to access Microsoft Outlook without any on-premises installations for Exchange 2013, Exchange 2010 users. For Microsoft Outlook update for Microsoft Exchange 2016 it was rebranded as “Outlook on the web”. OWA Outlook online provides access not only to email, but to other personal information like calendar, contacts, and tasks, and is widely used by businesses all over the world. With such sensitive data involved, OWA two-factor authentication becomes imperative.
We developed two products for Outlook OWA 2FA. The first product is Protectimus OWA, developed specifically for Office OWA integration. The second solution is Protectimus DSPA which adds 2FA directly to the repository (Active Directory, Lightweight Directory Access Protocol, databases) and thus adds MFA to everything linked to the business AD, LDAP, etc.
Today we will give you an in depth look into both methods. We will describe their work, show you how to implement each solution and list the tokens that support them.
Method 1. Use Protectimus OWA 2FA Plugin
Our Exchange OWA plugin is designed to integrate Outlook 2-factor authentication for mail on Microsoft Exchange 2016, Exchange 2013 as well as 2019. Protectimus installation wizard finishes a Microsoft MFA setup in 15 min tops.
How it works
With the plugin from Protectimus, OWA multi-factor authentication will be integrated with the OWA app only, nothing else. This method requires registering to Protectimus cloud service or downloading our MFA platform (contact out ), setting it up and starting the installation wizard. That is it.
This product for OWA two-factor authentication runs either in cloud, or locally. The customer gets all the advanced features like geo and time filters, IP filters, analysis of the user environment etc. Every Protectimus token works with this plugin, and it supports third-party tokens as well.
Supported tokens
All the MFA tokens are divided into software and hardware kinds. The divide is derived from the secret key (seed) implementation. Since we are focused solely on Microsoft Outlook Exchange login here, we won’t delve into details on how 2FA works. But you can always read other articles on our blog for more info on various MFA specifics. For now let’s just mention the tokens Protectimus OWA two-factor authentication supports:
| Token | Description |
|
|
|
|
|
|
|
|
|
|
|
|
As for the third party tokens — our OWA webmail 2FA supports any tokens that work on OATH standard algorithms. We support several of the most popular tokens from other OWA two-factor authentication providers, so the integration should not take too much effort on your part but you’ll still need a bit deeper knowledge of your token.
How to set up Outlook Web App 2-factor authentication with Protectimus OWA
First, get the OWA multi-factor authentication installer. Then register and sign in Protectimus cloud service and follow these steps:
- Add Resource. Only the Resource Name is obligatory, the rest of the parameters are optional.
- Add Users. Add a user’s Login, other parameters are optional. The user Login has to be login@domain, where login is the username in Active Directory, and domain is the corporate domain.
- Add Tokens. As you already know any OATH tokens may be used, but we will use Protectimus Smart.
- Add the Token Name. Using the Protectimus app scan the QR with the seed encoded. Input the OTP code you see next and click Save.
- Assign Tokens to Users. Return to the Users and match the tokens with the appropriate users: click Assign Token — Existing, select the required token, and click Assign.
- Assign Tokens and Users to the Resource. Go to the Resources page, click the Assign button, choose a Token-User combination, and select the tokens that should be accredited to the resource.
- Run the installation wizard as administrator. When you see the welcome message — click Next to proceed.
- Accept the terms in the License Agreement after attentively reading them, push the “Next” button.
- Choose the folder where you want the app installed, and press Next.
- Add API URL, Login, API Key, and Resource ID.
- API URL: https://api.protectimus.com/.
- API Login: the email of your Protectimus Service account login.
- API Key: you’ll find it on the Profile page.
- Resource ID: can be found on the Resources page.
- Click Next to continue.
- Everything is ready. Click Install and finish the process.
- Outlook web access two-factor authentication is enabled now.
Here’s a video to illustrate the above steps:
Method 2. Use Protectimus Dynamic Strong Password Authentication to enable OWA two-factor authentication through AD
Unlike Protectimus OWA, DSPA was designed to add MFA to everything hooked up to Active Directory, which includes OWA Outlook Web App for Outlook Exchange 2010.
How it works
After DSPA is deployed the users’ passes in Active Directory, and with it in Outlook Exchange, get a second dynamic part in addition to the common user password.
The dynamic password is a one-time password generated on the basis of TOTP algorithm, this means these OTPs expire in a few seconds or minutes. The passwords’ lifespan can be set up by the admin and can be anything from a few seconds to hours.
An Outlook Web Access password created with the dynamic component will be something like “Passcode855511”, where “Passcode” is the user’s static pass, and “855511” is the changing OTP added by the dynamic pass component.
For Protectimus DSPA to work you will need Protectimus on premises solution (the price starts from $199/month).
Supported tokens
Since DSPA allows the admins to set the OTP lifetime as long as they like, the tokens, which will deliver those OTPs, have to support this feature as well. This pegs down the token choice significantly.
| Token | Description |
|
|
Custom hardware tokens
|
|
How to integrate Outlook two-factor authentication applying DSPA
Configuring Protectimus on-premise for AD, and Microsoft OWA alongside, is as easy and effortless as the Protectimus OWA setup:
- Install Protectimus MFA Platform.
Request the platform with DSPA and installation instructions from us.
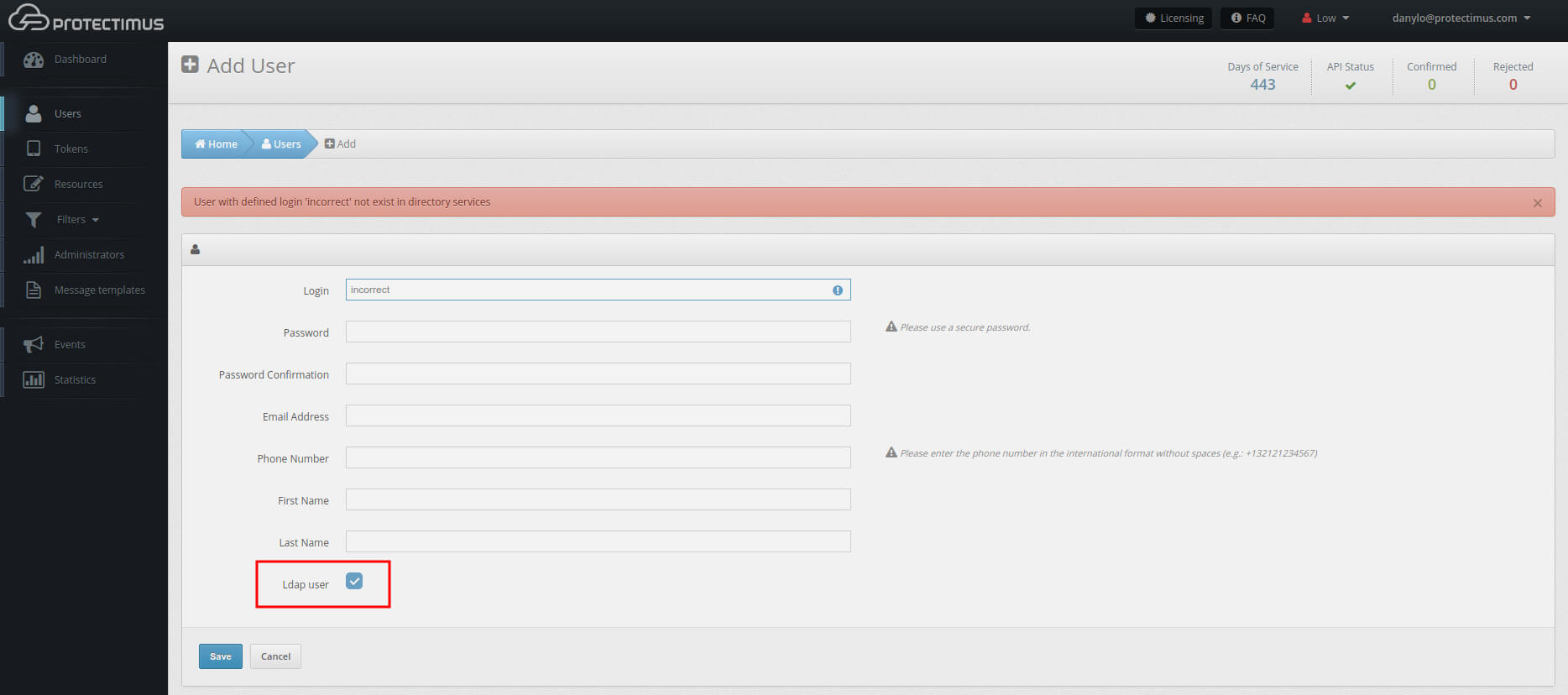
- Add users.
On the Users tab, choose Add User. Then check the LDAP User box. The Login has to be the user’s AD Common Name. Each end-user needs an email address, an admin has to add them on this step.

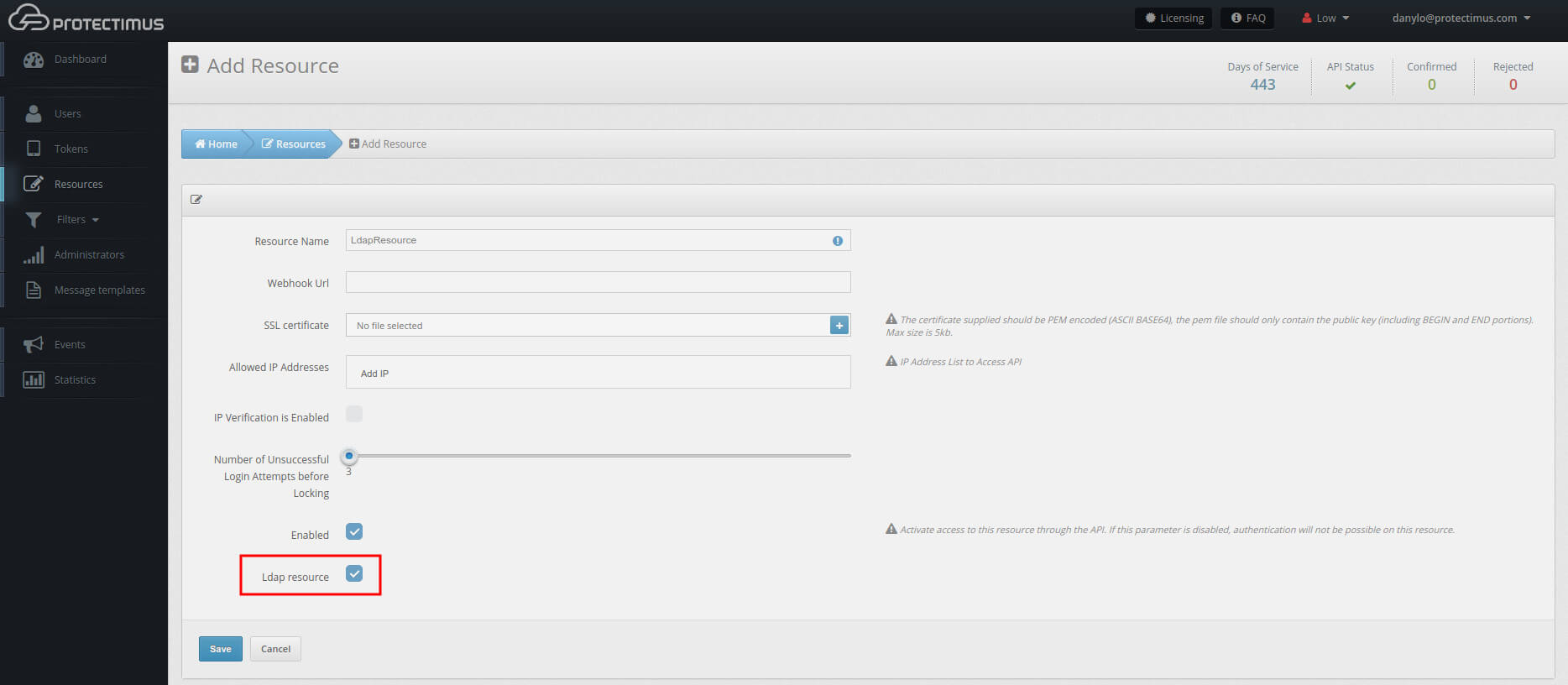
- Create a resource.
On the Resources tab, choose Add Resource. Check the LDAP box.

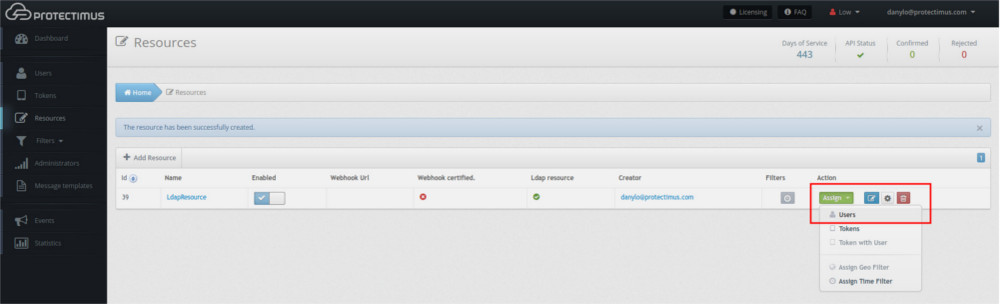
- Assign Users to the Resource
Next, the Users are to be attached to the Resource. In the Resources tab, click Assign -> Users. Only LDAP users can be assigned to an LDAP resource.

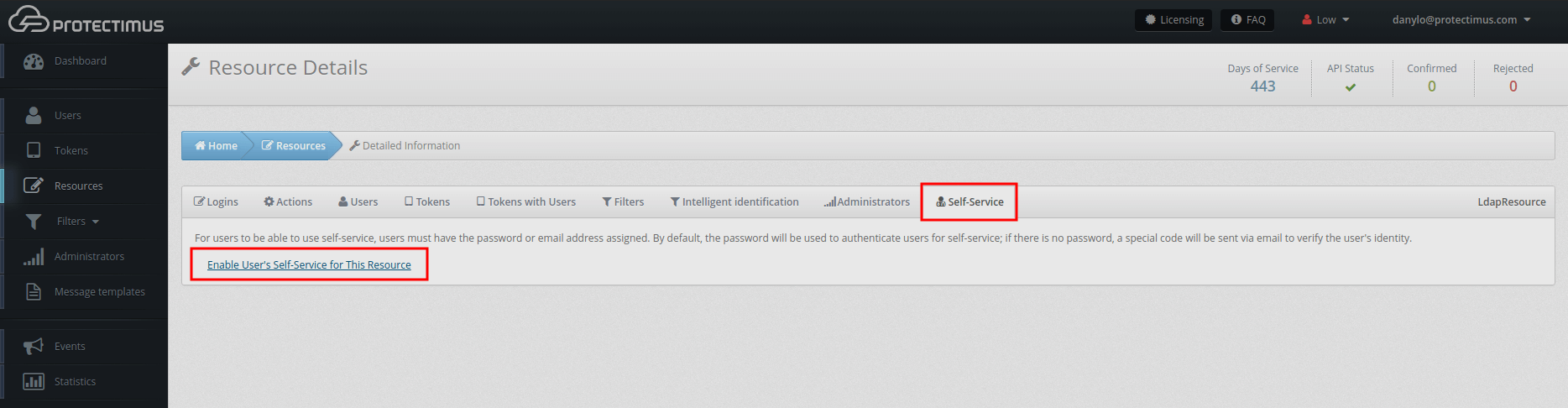
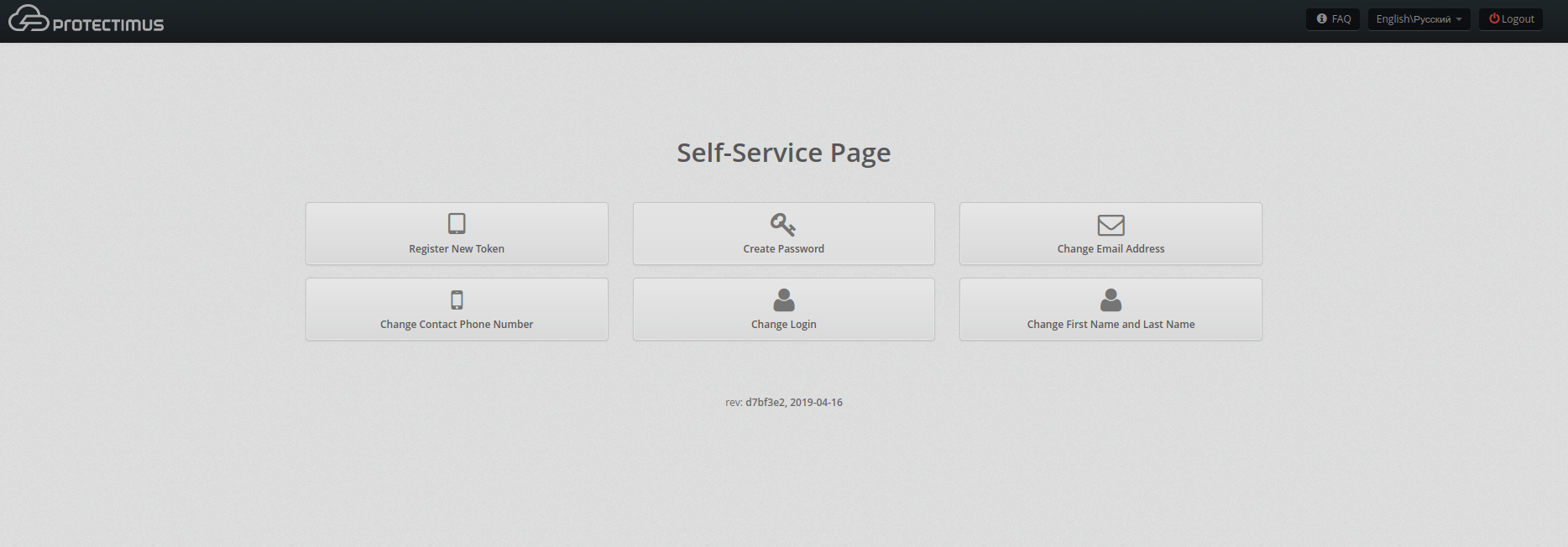
- Enable Self-Service.
Find and check “Enable User’s Self-Service for This Resource” in the new resource. Come up with the URL for your end-users to access the page by adding a custom part to the link. If we add “mywebowa”, the link would be https://service.protectimus.com/selfservice/mywebowa

- Make your Users create tokens via Self-Service.
Each user has to create their own tokens and add their static passes to them. Give the link you came up with to each end-user. Ask them to sign in with their Common Name and the OTPs emailed to the addresses you added in the second step. Every user needs to register a New Token (let them know what time interval to choose) and to add their AD unchanging passcode.

Conclusions
OWA intermedia security settings are not sufficient enough if you want your business OWA mail and everything connected to it to be truly secure. Both two-factor authentication outlook options we offer are good, which one to choose depends on your needs and the quantity of users you have. If you want to protect everything, not only web Outlook, and you have more than 200 users — opt for DSPA. If all you need to protect is webmail OWA and the quantity of users is small — Protectimus OWA is the way to go.
If after reading this article, you still have any questions on our Microsoft Outlook web app 2FA solutions, or you hesitate on which one to choose — do contact us. We are here to help you protect your Microsoft Exchange Outlook web access.
Read also:
- Two-Factor Authentication Solutions Comparison: Google Authenticator vs. Protectimus
- Two-factor authentication for Windows 7, 8, 10
- Hardware Tokens for Azure MFA
- Office 365 MFA Hardware Token
- Duo Security vs Protectimus
- 2FA Chatbots vs. SMS Authentication
- TOTP Tokens Protectimus Slim NFC: FAQ
- Best Protectimus MFA Features for Financial Services Cybersecurity
- Electronic Visit Verification with Hardware Tokens
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.








2020-07-10
Hi, I need to enable MFA with OWA. My servers are on-Premises, is it working ?
2020-07-13
Sure. We can provide an on-premises version of our 2FA platform and setup OWA 2FA with it. Please, contact our support team at [email protected] to get the on-premise platform.
2020-07-12
I need 2FA for Exchange OWA, but softbase token, not hardware based. Do you have soft token for owa 2FA?
2020-07-13
No problem, Protectimus OWA MFA solution allows using our free software token Protectimus Smart OTP or any other software token including Google Authenticator.