Time-based one-time password algorithm (TOTP) is the focus of this post. But, before we delve deeper into the TOTP meaning, we’d like to mention the organization that is instrumental in the one-time password algorithms’ existence — OATH, or Open AuTHentication. OATH is a collaboration of all sorts of specialists, who made their mission to create a truly secure and universal network for all to use. We at Protectimus are proud to be a part of this collaborative effort.
In this article, we will learn what OATH TOTP is. We will have a closer look at TOTP algorithm implementation and the work of the TOTP mode. Finally, we will provide a full list of Protectimus TOTP tokens designed for time based token authentication to help you choose the one that suits you best.
Table of contents:
What is TOTP algorithm
We’ve already answered the “what does TOTP mean?” question above. But what is TOTP authentication? An uncomplicated answer is — it’s a 2-factor verification method that uses the time as a variable. Let’s expand on this a bit and unravel how TOTP authentication actually operates.
TOTP algorithm (RFC 6238) implies that an OTP is a product of two parameters encrypted together. These are a common value, which is a shared secret key, or seed; and a variable, in this case – the running time. These parameters are encrypted with a hash function.
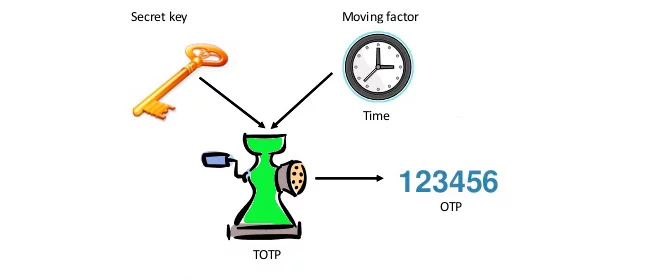
Here’s a TOTP algorithm example to illustrate:
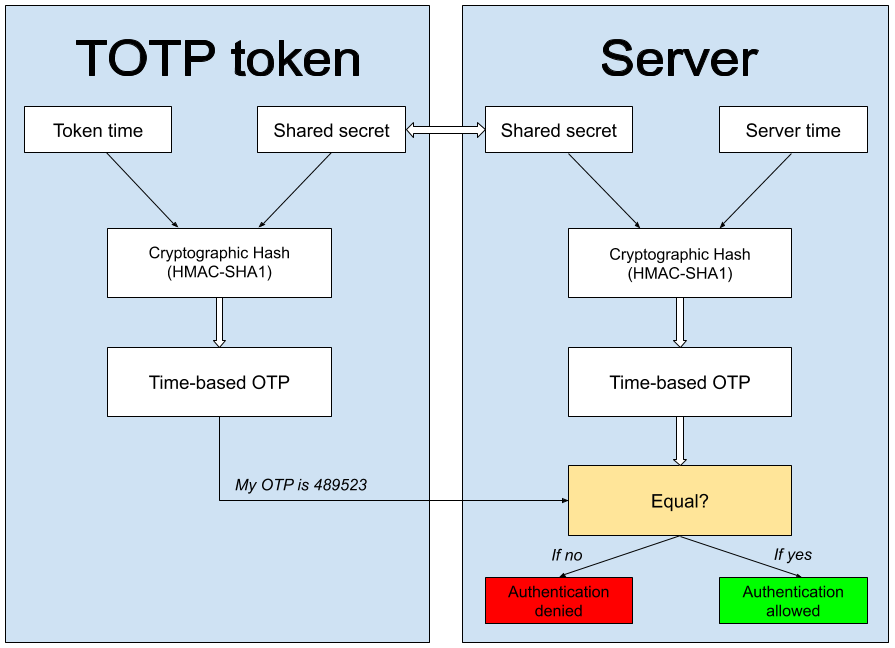
- A user wants to log into a TOTP 2FA protected application or website. For the OTP authentication to run, the user and the TOTP server need to initially share a static parameter (a secret key).
- When the client logs into the protected website, they have to confirm they possess the secret key. So their TOTP token merges the seed and the current timestep and generates a HASH value by running a predetermined HASH function. This value essentially is the OTP code the user sees on the token.
- Since the secret key, the HASH function, and the timestep are the same for both parties, the server makes the same computation as the user’s OTP generator.
- The user enters the OTP and if it is identical to the server’s value, the access is granted. If the results of the calculations aren’t identical, the access is, naturally, denied.
To explain the above example a bit let’s note here that the mentioned seed is a string of random characters, usually 16–32 characters long. “Sharing” the key usually implies scanning a QR code that shows the seed generated by the server with the client’s TOTP app. Alternatively, the key is already programmed in their TOTP device. The timestep is calculated using UNIX time, which starts on January 1, 1970, UTC. The timesteps are to be 30 or 60 seconds, so the time value used for TOTP is the number of seconds run since 00:00 January 1, 1970, divided by 30, or 60. Finally, the mentioned HASH function is a cryptographic mathematic function that simply changes one value into another and usually shortens the result to 6-8 symbols. This result is what we called a HASH value above.
All of this is specified in TOTP RFC.
TOTP algorithm background — HOTP
OATH has been actively working on secure 2FA since 2004. The first algorithm that the organization created is HOTP — HMAC-based One-time Password, presented in 2005. This method uses a counter as a variable and a seed as a shared value to create OTP.
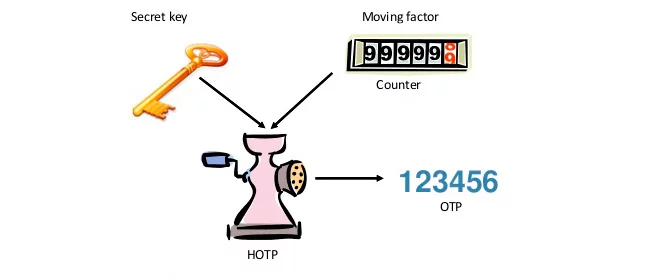
The creation of a one time password is the event for the counter in HOTP, so each new password increases the counter by 1. We’ve described this algorithm in every detail in this article.
The counter-based method has a number of flaws, we’ll touch upon them next. So in 2008 OATH presented TOTP as an expansion of the parent algorithm, the next step of the MFA evolution.
| Read also: OCRA Algorithm Explained
TOTP vs HOTP
HOTP is a lot less bulletproof than the time-based one-time password algorithm. If a HOTP OTP token falls into a hacker’s hands, the criminal can write down the OTPs and use them at any time. The HOTP passes do not have an expiration time, the hacker just has to use one faster than the owner.
Another drawback of HOTP is the server-token unsynchronization if the button on the device is pressed too many times. Remember, the counter increases with each new OTP? The server has no ability to follow how many times the token button is clicked since the physical tokens are completely offline. This is accounted for in the algorithm, but if someone clicks the button too many times unintentionally (a child plays with it), or intentionally (a criminal) the token is rendered useless.
HOTP is also more vulnerable to brute-force attacks and other ways to guess the next OTP. The hacker would have to get access to the token and write down a few of the OTPs, the password guessing will take some serious computing and a few hours. But it’s still possible.
In the HOTP vs TOTP battle, TOTP security would certainly win. TOTP passwords have a limited lifespan. If a password provided by an RFC6238 TOTP generator is not used within 30, sometimes 60 seconds, it simply expires and can not be used for login. So writing the OTPs down won’t do a hacker any good. The token button can be clicked as many times as your heart desires, it won’t put the token and server out of sync.
TOTP tokens do have their own issue — time drift. But we’ve already solved it in programmable tokens Protectimus Slim NFC. Let’s talk about it next.
| Read also: 2FA Security Flaws You Should Know About
TOTP synchronization problem
A TOTP hardware token is completely offline, no network connection whatsoever. This makes it impenetrable for the majority of known hacker attacks. But the TOTP algorithm relies on the time, so the tokens are supplied with a clock of sorts — an oscillator. With no way to sync the time, a drift happens eventually. But the time the server has is always precise.
The discrepancy is averagely 2 minutes per year. And yes, the algorithm has a synchronization window to allow for it. But OTP tokens have batteries with a long lifetime. So, in a few years, the drift inevitably overflows the sync window and becomes an issue. Eventually, the server and the TOTP device start to generate different values.
We have a very detailed blog post on this problem and how we managed to fix it. So we won’t delve into details and just say here that since May 2019 Protectimus Slim NFC devices have the synchronization issue fixed.
| Read also: TOTP Tokens Protectimus Slim NFC: FAQ
Protectimus TOTP tokens
Time-based OTP algorithm is a widely applied MFA solution, there’s even Google Authenticator TOTP mode. Protectimus can offer you three tokens developed with time-based OTP RFC specification.
| Token | Description |
|
|
|
|
|
Read more:
- The Pros and Cons of Different Two-Factor Authentication Types and Methods
- Two-Factor Authentication Solutions Comparison: Google Authenticator vs. Protectimus
- 10 Most Popular Two-Factor Authentication Apps Compared
- Electronic Visit Verification with Hardware Tokens
- Two-factor authentication for Windows 7, 8, 10
- Active Directory Two-Factor Authentication
- 2FA Chatbots vs. SMS Authentication
- Duo Security vs Protectimus
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.





2020-06-26
We are considering using the Protectiums Two for use in an existing system. In this system TOTP is already implemented, users use the Google Authenticator app to generate the verification codes. We would like to offer the possibility to use the Protectiums Two instead of this app. We realize we have to adapt the system to be able to enter the secret instead of allowing users to scan a QR code with the generated secret. Is this secret provided with each Protectiums Two? And will we still be able to keep the window size at 2? Our TOTP’s refresh every 30 seconds.
2020-06-26
Hi Jelle, sure, we’ll send you the secret keys in an encrypted archive. The window size can be kept at 2, but because of the time drifts, you’ll need to adjust the clock on the server each authentication to synchronize it with the tokens’ clocks. In our service, this issue is already foreseen and solved according to the RFC 6238 standard.