You asked, and we delivered – the new programmable TOTP token Protectimus Flex in a key fob format is already here!
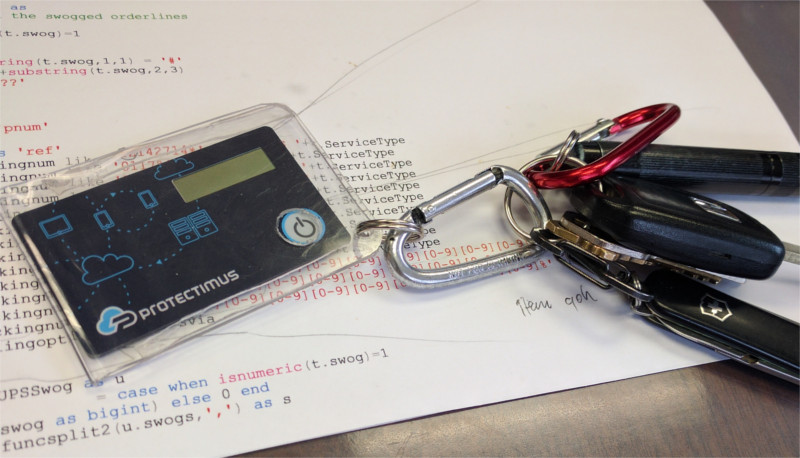
Unlike our other popular programmable hardware token Protectimus Slim NFC, the new Protectimus Flex TOTP token comes in the form of a key fob. This makes our latest two-factor authentication hardware token more comfortable to use, and more durable. The security token can easily be fastened to your keys, this way you won’t forget it, or lose it. There is a bonus feature in the new gadget — it has a battery indicator. This makes it easier to understand when it’s time to order a replacement.
Similar to Protectimus Slim NFC, the new hardware token device requires an Android phone with NFC to burn the secret key (seed) into the device. Protectimus Flex supports secret keys no longer than 32 symbols in the Base32 numeral system. And the new TOTP authenticator can generate OTP passwords for any website that supports MFA apps, so you don’t have to install Protectimus MFA platform to work in conjunction with it.
How the new TOTP hardware token Protectimus Flex works
A hardware security token is typically a small device with a window display. These gadgets are roughly divided into two types:
- So-called classic tokens, they are delivered with the seed hardcoded and the user cannot change it.
- And programmable ones, a programmable TOTP token is designed for a seed to be written into it multiple times.
Simply put — programmable physical token functions just like any MFA app software token (but note that unlike an MFA app one programmable hardware token can store only one secret key). These devices are safer than an app, since a one time password is generated not on a smartphone, but on a device which has no Internet connection, thus, cannot be infected by any viruses. So programmed hardware token authentication often replaces those apps for better-safeguarded OTP authentication.
Besides, programmable TOTP token Protectimus Flex supports time synchronization feature. When you add the secret key into the token, the Protectimus TOTP Burner application automatically sets the exact current time on the token. This feature allows avoiding the time drift problem that is a common thing with TOTP hardware tokens.
Physical programmable tokens are our specialty. And while Slim NFC is in high demand, its form factor of a card is slightly uncomfortable for some customers. Form is the main difference between Slim and Flex, the mode of action of both devices is the same.

We’ve already written about the TOTP algorithm, which the programmed tokens operate on. If you want to know every detail behind TOTP you can read it here. And for a better understanding of the distinctions between classic and programmed physical tokens, as well as a detailed description of a programmable device we’d like to refer you to this article.
Which sites can Protectimus Flex hardware 2FA token be linked to?
A seed no longer than 32 Base32 symbols can be added into the programmable OTP hardware token Flex. The gadget can be used for TOTP MFA setup for one website, app, or service at a time. So, if the website aligns with these criteria then this TOTP hardware authenticator can be utilized for this website.
Programmable hardware token Protectimus Flex can be utilized to deliver an MFA code for Azure MFA, Office 365, Google, PayPal, Twitter, Facebook, Dropbox, Github, Coinbase, and a lot of others.
Keyfob form-factor advantages
We are always in touch with our customers, we listen to all the feedback we receive. Ever since our first programmable 2-factor authentication hardware token was presented we have been receiving inquiries for the same token but in key fob form. A lot of the customers asked if it is safe to drill a hole in the Slim NFC token to fasten it to their keys. One client even made a custom case for the OTP device.
The key fob form factor turns out to be more usable. You can not lose or forget the token if it’s fastened to your keys. It is far harder to nip it from you as well. Besides, the key fob form might be a bit more durable than the card form.
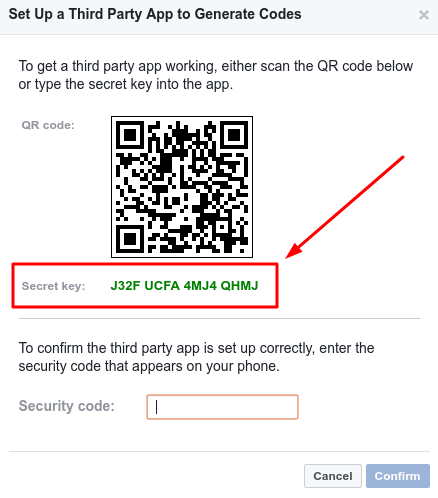
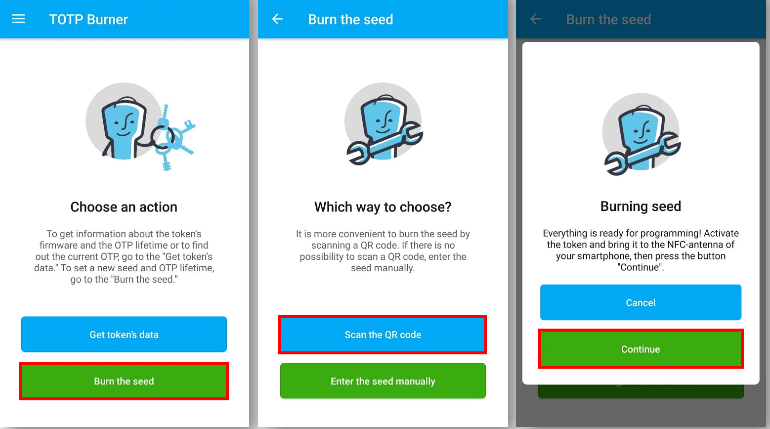
How to program the Protectimus Flex TOTP generator
To program the Flex hardware OTP token you will need an Android cellphone with enabled NFC. Naturally, the website you’d like to link the token to has to support TOTP MFA. This programmable OATH hardware token is perfect for those websites that support MFA with a TOTP authenticator app.
- Download a Protectimus TOTP Burner app
Download our TOTP burner application to your Android phone.
- Start the MFA setup
Start setting up multi-factor authentication on the website you want the token to be linked to.
- Program the new 2FA hardware token:
3.1 Start the burner application.
3.2 Click “Burn the seed”.
3.3 Click “Scan the QR code” and scan the code from the website’s TOTP QR code generator.
3.4 Activate Protectimus Flex and make sure it is placed near the phone’s NFC antenna.
3.5 Click “Continue”. The process is finished when the OTP authentication key activation confirmation message arrives. - Enter the one-time password to finish the MFA setup
Go back to the MFA protected website and log in using the OTP code delivered by your token.
Frequently Asked Questions
No, Flex can be used for one website/service, with one seed programmed into it, at a time. But Flex can be repurposed. When you stop using a website the OATH TOTP hardware token was initially programmed for, you can disconnect the device from that website and program it for another website/service.
This TOTP hardware key can be linked to almost any website that offers 2FA with Google Authenticator or supports any other MFA application. Among the supported services is the majority of payment systems, social networks, cryptocurrency exchanges, and many others.
No. The app is currently available for Android only.
The OATH TOTP token battery lasts up to 5 years, you can’t charge or change it. But the device has a battery indicator, so you can easily buy a replacement before the battery reaches its limit.
The price is $19.99 for one device.
Our TOTP Burner app and a smartphone with Android and NFC antenna are required to program this TOTP token generator. The step-by-step guide is provided in the article above.
There is absolutely no way to get the seed from a programmed token. And the burning app retains no secret keys. The token has no open interfaces, so once after production, it cannot communicate with the outside world (except NFC). But, for NFC, the token does not have an API for reading secret (only writing secret). Additionally, the app does not store secret keys. You can safely use a single phone to program several tokens.
Sure, you can order as much as one item with a custom logo. Contact our sales team for more details.
An Android mobile phone is required to burn the seed into the token. After the programming is complete the device works totally autonomously.
Yes, when you program a secret key into the Protectimus Flex token, the app automatically sets the exact current time on the token.
Read more
- TOTP Algorithm Explained
- The Pros and Cons of Different Two-Factor Authentication Types and Methods
- 2FA Security Flaws You Should Know About
- Hardware or Software Token – Which One to Choose?
- Two-factor authentication for Windows 7, 8, 10
- Two-Factor Authentication Solutions Comparison: Google Authenticator vs. Protectimus
- On-Premise 2FA vs Cloud-Based Authentication
- Remote Work: How to Transition Team to Working From Home During the COVID-19 Pandemic
- Securing VPN with Two-Factor Authentication
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


2021-01-17
How is it protected from unauthorized access? If it is stolen, for example.
2021-01-20
Valery, if you use this or any other OTP token with Protectimus two-factor authentication system, the Protectimus administrator can set up additional PIN protection. In this case, the user will have to enter a PIN code every time they enter a one-time password from the token before or after the OTP. This approach makes a token useless for the fraudster as a one-time password won’t work without a PIN. But if you use the programmable hardware OTP token with any other service, then when it’s stolen, it’s stolen, and the person who has stolen the token knows your one-time passwords. Though they still need to know your static password to get access to your account, so you’ll have time to notice the token’s missing and take action.