Any of us is interested in protecting confidential data from becoming the public domain on the web. Especially from people who are looking for such information for fraudulent purposes.
The effective methods to avoid the invasion of online privacy are already known. And one of the most accessible ways is protecting access to your accounts with two-factor authentication. But… unfortunately, people don’t always use this option if it’s not mandatory. Just because two-factor authentication is not convenient.
Adaptive authentication (or Intelligent Identification as we call it in Protectimus) is a way to organize two-factor authentication so that it becomes convenient for end-users. Adaptive authentication means analyzing behavioral factors typical for the user and asking for a one-time password only if a large number of mismatches is detected.
Why nobody likes two-factor authentication
Let’s imagine that every time you want to check what’s new on your Facebook account protected with 2FA, you have to go through a complete account login procedure:
- Enter your login and password.
- Then wait for an SMS with a one-time password or use your token to generates it.
- Then, you also need to enter this one-time password into the login form.
How much time will this procedure take? And all this is just to browse the news and messages from friends?
According to the NordPass research, an average Internet user has around 80 accounts protected with passwords. Of course, people are not ready to follow the procedure described above every time they want to enter their accounts on every website they use. Especially if we talk about the services used many times a day, like social networks or email. That is why users always choose between simplicity and security and often not in favor of the latter.
To make the authentication process more user-friendly, adaptive authentication has been invented – an authentication based on behavioral factors analysis.
| READ ALSO: SMS Authentication: All Pros and Cons Explained
What is adaptive authentication
The system of adaptive authentication keeps a record of certain parameters of the device a person uses to access their account. If the analysis of the behavioral factors shows the typical behavior of the user, the login is automatic. And if one or more of them violate the usual ‘course of events, the request for additional confirmation of the user’s identity is needed. In the case of two-factor authentication, it is required to enter a one-time password.
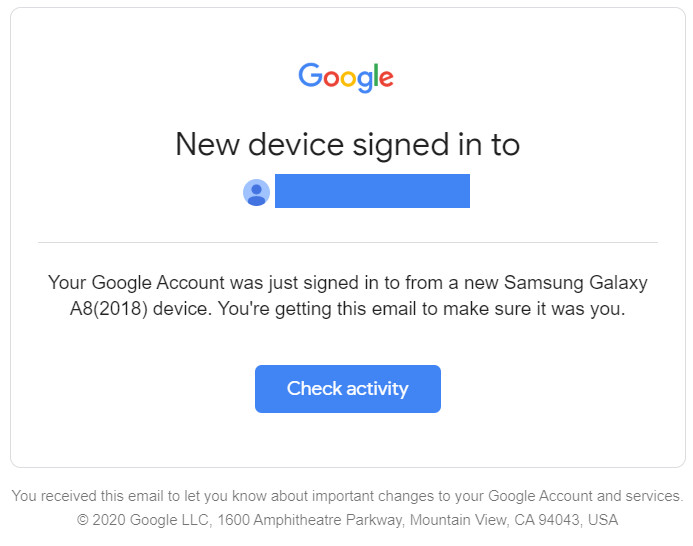
For example, let’s recall what happens when you log into your Gmail account. If you use the same device and the same browser, you don’t need to enter your credentials every time you check the mail. But when you try to log in to Gmail from another computer or another browser on the same device, the system will necessarily require entering your password. Sometimes you will also need to answer a secret question or use your OTP token if two-factor authentication is enabled. Google will even send a message about a suspicious sign-in attempt
The basis of adaptive authentication consists of behavioral characteristics relatively constant for each user. Among the parameters monitored by the system can be the following:
- name and version of the browser;
- the list of installed plug-ins;
- IP address, location of the computer;
- the input language;
- typical session time, a list of opened tabs and other behavioral characteristics of a user, etc.
It’s possible to adjust the adaptive authentication technology to the needs of each company. The authentication system can take into account more or fewer parameters during the analysis. It depends on the needs and the type of services the company provides. Every business decides which parameters to monitor and whether it needs adaptive authentication at all.
| READ ALSO: Securing VPN with Two-Factor Authentication
How Protectimus’ adaptive authentication feature works
Protectimus 2FA service allows the administrator to set custom adaptive authnetication conditions under which the authentication system will require a one-time password. We call this feature Intelligent Identification.
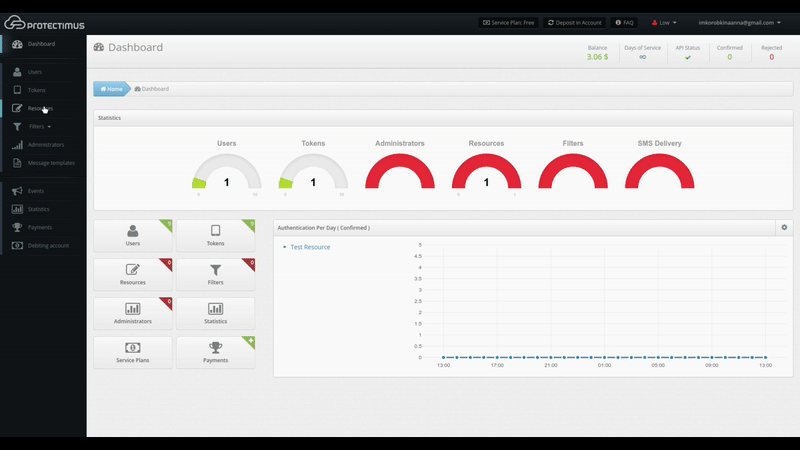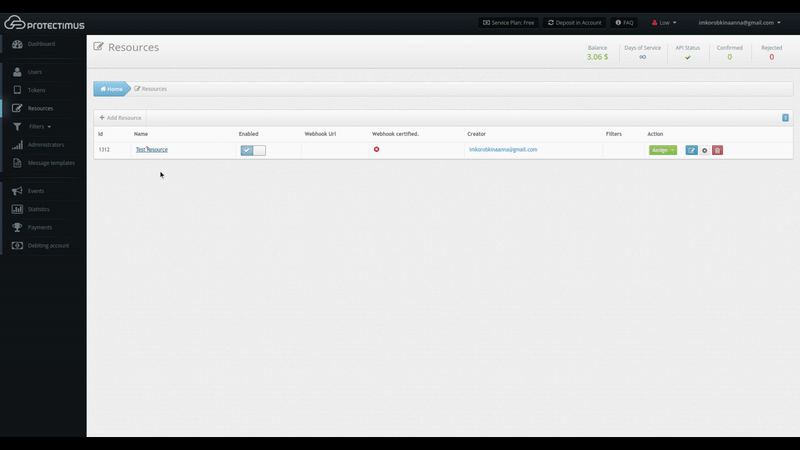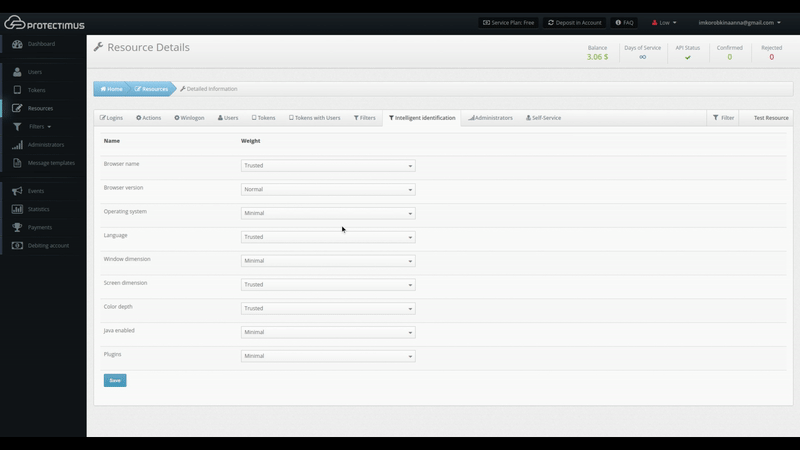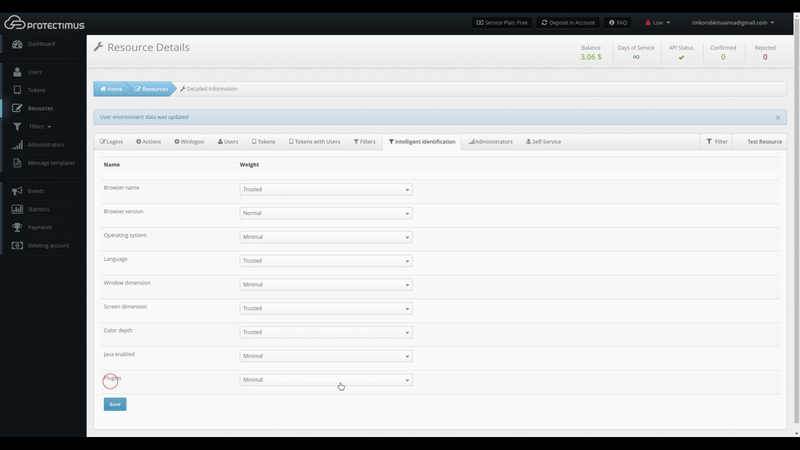
The list of tracked behavioral characteristics includes not only the model and version of the browser but also many other factors such as:
- browser name;
- browser version;
- operating system;
- language;
- window dimension;
- screen dimension;
- color depth;
- Java enabled or not;
- installed plugins.
The Protectimus administrator can set the level of trust (minimal, normal, or trusted) for each of these parameters.
To enable the Protectimus Intelligent Identification feature, you should: Log in to the Protectimus cloud service or on-premise platform -> Go to Resources -> Click the Resource name -> Go to the Intelligent Identification tab -> Set up the level of trust for all available parameters -> And click Save.
It is up to the customer to choose which of these factors should be taken into account. Or maybe the adaptive authentication shouldn’t be used at all.
It seems reasonable since each company that uses two-step verification has its own security requirements. For example, for social networks, forums, game platforms, it makes sense to use adaptive authentication, track behavioral factors, and request a one-time password only in case of deviation from the usual pattern of the user’s behavior. However, for banks and other companies involved in operations with money, such “loyalty” is hardly acceptable. It will be better to request one-time passwords during each login and transaction.
Adaptive authentication feature helps to make 2-factor authentication flexible and convenient both for the company and its users. We recommend you pay attention to this feature and activate it in your Protectimus account to make your users happier. Please, contact us with any questions about Protectimus two-factor authentication service and the adaptive authentication feature at [email protected].
Read more
- How to Enable Protectimus Self-Service Portal
- On-Premise 2FA vs Cloud-Based Authentication
- How to Add Two-Factor Authentication to Outlook Web App (OWA)
- Two-factor authentication for Windows 7, 8, 10, 11
- Active Directory Two-Factor Authentication
- New Programmable TOTP token Protectimus Flex
- Time Drift in TOTP Hardware Tokens Explained and Solved
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


2022-02-01
This approach improves overall security by ensuring that high-risk consumers have the highest level of adaptable and flexible security in place.