Protectimus is one of the biggest and most reliable two-factor authentication providers. We’ve been developing cutting-edge 2FA solutions since 2014. Being a coordination member of the OATH Initiative for Open Authentication, Protectimus is one of the strongest voices in the propagation of ubiquitous strong authentication.
The main problem Protectimus works on is perfecting multi-factor auth solutions, to make 2FA easier, cheaper, and safer for everyone. All the products we will list below fulfill at least one of those goals.
Protectimus Winlogon
This is one of the best 2-factor authentication solutions for Windows user accounts and remote desktops currently on the market. The Protectimus Winlogon 2FA solution provides access protection for computers running Windows 7, 8, 8.1, 10 and 11. It will also protect local or remote access to a terminal Windows Server 2012, 2016, 2019, 2022 over RDP.
The most brilliant feature of Protectimus Winlogon is that it works even if the computer is not connected to the Internet. This is achieved with the help of backup codes. Normally, the Protectimus Winlogon component communicates with the Protectimus two-factor authentication server to validate one-time passwords. A network connection is required for that. So if the user is unable to connect to the Internet, they can’t log in to their account. But with the backup feature, the user can generate and save a backup code when installing the component. And then use that code instead of a one-time password to log into the account in offline mode.
There are, of course, other features worth mentioning:
- Auto registration of users and tokens;
- Mass installation on several computers ;
- Better RDP access (2FA can be switched off for Windows with one-time password asked for RDP only; one- or two-factor auth can be set up for RDP);
- RDP access filtering with IP and IP access control;
- Different access policies for RDP and Winlogon;
- PIN support in Windows 10;
- Microsoft account support.
Protectimus Winlogon setup does not require any special knowledge and can be done in about 15 minutes. The solution is perfect both for corporate and personal use.
| Read more: Two-factor authentication for Windows 7, 8, 10, 11
Protectimus Slim NFC and Protectimus Flex
These are the first programmable tokens on the market. These hardware tokens are available in card form (Protectimus Slim NFC) and key fob form (Protectimus Flex).
Designed as a safer alternative for MFA applications, these devices can be used to protect almost any account. From Google and Office 365 to Azure MFA and 2FA Protectimus system itself.
Programmable hardware tokens, unlike the classic ones, can have the seed programmed into the token by the end-user via NFC. These tokens work just like a multifactor authentication app. But the devices can be used to protect one account at a time. And they can be reused, namely, disconnected from one account and connected to another.
As we’ve already mentioned, programmable hardware tokens are a much safer alternative to the MFA apps. The one-time passwords for MFA are generated not on the users’ smartphones, but on the tokens. And the tokens have no internet connection, they can not be infected by any viruses. Intercepting such a password is virtually impossible.
Both Protectimus Slim NFC and Protectimus Flex come with the time synchronisation feature. This allows us to avoid the time drift problem, the common issue with all TOTP hardware tokens.
The only drawback of these tokens is that the app for programming them is available for Android only.
| Read more: New Programmable TOTP token Protectimus Flex
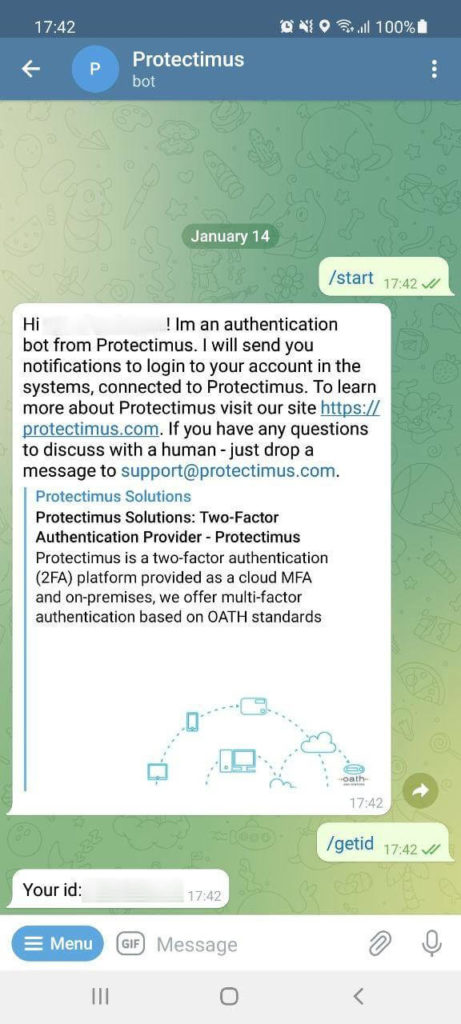
Protectimus Bot
This one is a unique Protectimus solution for delivering one-time passwords. The idea behind it is to make 2FA as easy and comfortable for the end-user as SMS authentication. Yet, without the main pitfalls of SMS authentication – high price and insecurity. So the Protectimus team came up with the idea to deliver one-time passes via the most popular messengers – Telegram, Facebook Messenger, Viber. For Protectimus clients and their end-users, this delivery method is completely free of charge.
Protectimus Bot 2FA is much safer than SMS 2FA because the passwords aren’t delivered via the cellular networks, so the GSM network vulnerabilities can not be used to intercept the OTPs. Messages sent via these services are encrypted. So even if the OTP is intercepted the hacker won’t be able to use it. And there are no known viruses able to extract one-time passwords from the messaging apps. While SMS extraction viruses are aplenty.
Other things that work for the security of 2FA via the chatbot:
- The access to the messengers is password protected. Two-factor authentication can be used to protect them additionally.
- If someone attempts to log in to the user’s account, the user will immediately receive a notification.
The end-users don’t need to install any additional apps or buy hardware tokens. There’s a 99% chance that the users already have one of these messaging apps installed. Protectimus bot can even be used without access to a smartphone since all of the chosen messengers have web versions.
Protectimus 2FA chatbot can also deliver other messages and notifications as well as one-time passwords.
| Read more: 2FA Chatbots vs. SMS Authentication
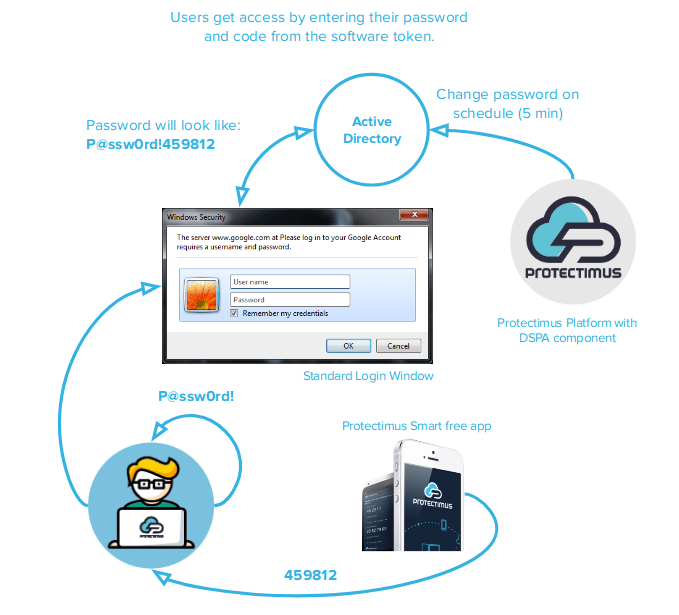
Protectimus DSPA
This is another unique Protectimus solution. Dynamic Strong Password Authentication or DSPA for short integrates directly with a database or user directory and turns the common user passwords into dynamic ones. These dynamic passwords consist of two parts. The first part, the password the user created, is a static part. The second part is dynamic. It is an OTP and it changes every 30 seconds. The dynamic password looks something like this: Password86542
Where the “Password” part is the user’s static password, and the “86542” part is the dynamic one-time password.
DSPA ensures that the integration is extremely easy. All the users in the database are simultaneously protected, there’s no need to configure 2FA on each endpoint.
And it offers better security. There’s no way to bypass 2FA with DSPA even if someone tries to initiate a direct request to the repository via the command line.
| Read more: Active Directory Two-Factor Authentication
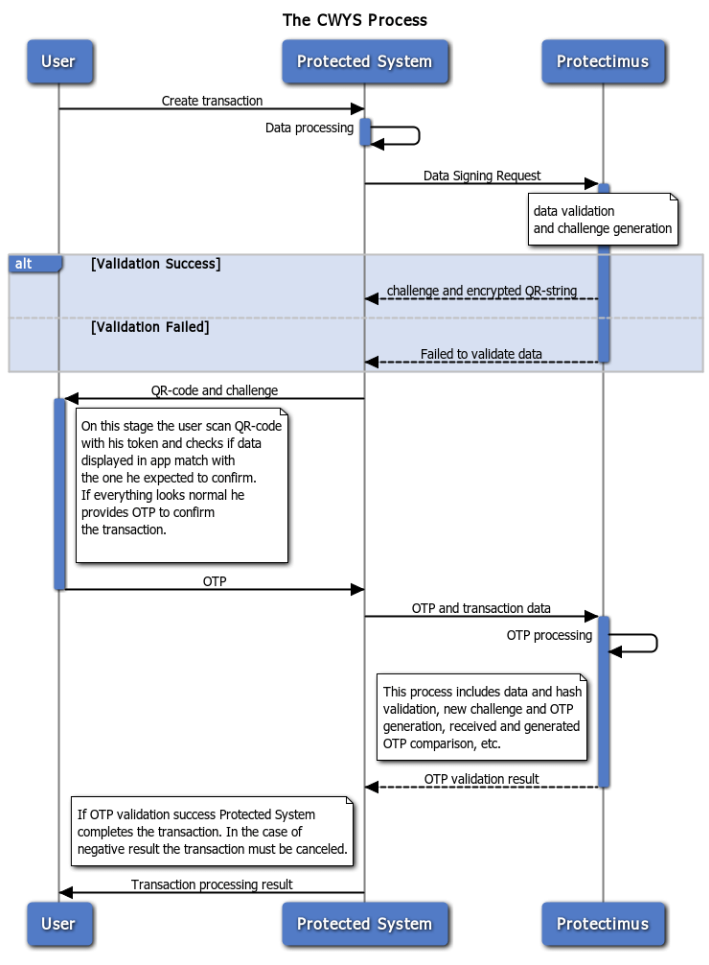
Protectimus CWYS
Confirm What You See (CWYS) data signing feature from Protectimus is based on the transaction data signing method. The original method allows a user to confirm a financial operation by verifying certain details of the transaction. Usually, the recipient’s account, amount, and currency are the things verified.
Protectimus CWYS creates one-time passwords using the user’s transaction (or another operation) data. This method is second to none in protecting financial operations. Imagine – an end-user wants to transfer a big sum. The user creates a transaction and needs to confirm it with a one-time password. This one-time password is created on the basis of this very transaction data: the transaction sum, currency, account data, etc. Thus, this OTP password can confirm only the valid transaction created by the user.
Read also
- 6 MFA Myths You Still Believe
- Hardware Tokens for Azure MFA
- How to Add Two-Factor Authentication to Outlook Web App (OWA)
- Remote Work: How to Transition Team to Working From Home During the COVID-19 Pandemic
- The Pros and Cons of Different Two-Factor Authentication Types and Methods
- On-Premise 2FA vs Cloud-Based Authentication
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!