It is hard to manage multiple users and systems, especially when there are not even hundreds, but thousands of them in a network. That’s why businesses and organizations love Microsoft Active Directory. It allows for storing and managing all the information on the organization’s systems, users, their credentials, sites and whatever else you might think of in a network, in one place.
But you must agree that this much of fundamentally important information kept in one place makes Active Directory a tidbit for hackers. And simple password-username verification is far from sufficient to protect it all from attacks. This is why multifactor authentication is especially crucial for Active Directory security. Dynamic Strong Password Authentication (DSPA) solution from Protectimus has it well-cowered for you and your users. Adding the second layer of security to all systems and services attached to Active Directory in one go has never been easier.
In this article, we will describe in detail how our two-factor authentication solution for Active Directory works, why ours is the easiest approach to Active Directory MFA, which methods of MFA can be used with it and how to get it running. We will also provide answers to the most asked questions on our solution for the Active Directory multi-factor authentication.
How it works
Protectimus Dynamic Strong Password Authentication (DSPA) operates via direct Active Directory integration, it simply adds a 6-digit dynamic password to the static user password. These 6 symbols are essentially a one-time time-sensitive pass code that is generated with the TOTP algorithm. This one-time password (OTP) is constantly changing.
As a result of the ingenious integration, to get into a Microsoft AD attached account the user needs to enter a combined pass of this configuration — u$erp@ssword123456, the u$erp@ssword part here is the never-changing password devised by the user, admin, or generated by the system itself and the 123456 part is a dynamic OTP generated by Protectimus MFA token.
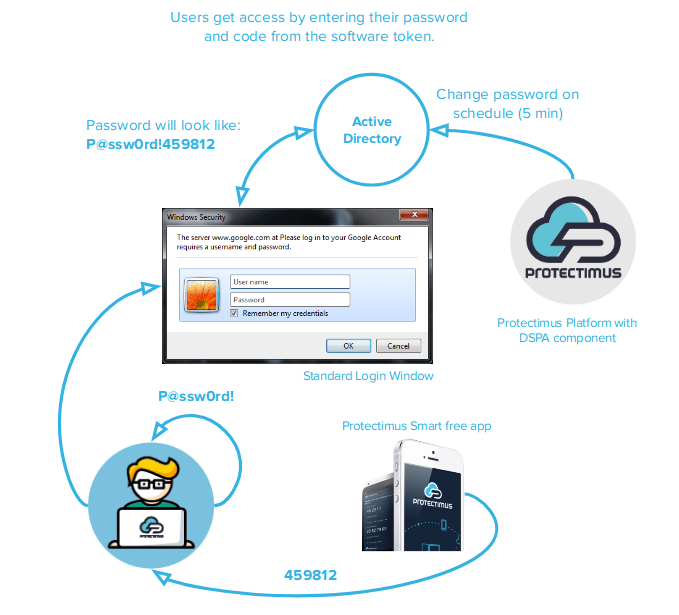
The company’s Active Directory server administrator can set the time-step, in which the OTP is changed, to 30 seconds or more (for example, for 600 seconds). So the DSPA part (those 6 digits OTPs) of the user passwords constantly change according to the timeline determined by the admin. Besides, teams of users can be made to be, or not be subject to the DSPA element in their static passwords; making the two-factor authentication AD required for the most valuable accounts only.
| Read also: Two-factor authentication for Windows 7, 8, 10
Advantages of this approach to AD 2-factor authentication
1. Advanced Active Directory security
Every regular 2-factor verification arrangement adds the second layer to the endpoints only. As a result, the hackers have a window to bypass 2FA and call the user directory up straightforward. Active Directory domain is easily called up through the Windows command prompt, so the hacker simply needs a user’s credentials (login and password) to act maliciously under their name and no Active Directory 2-factor authentication will be there to stop him.
Two-factor authentication Active Directory solution from Protectimus allows to enable the complete system protection and ensure no-one can get into AD without the additional dynamic OTP.
2. Ease of use and maintenance for AD administrators
Another issue that our solution for Active Directory two-factor authentication easily fixes is the need for multiple 2FA solutions for various accounts, services, and platforms. Traditionally the administrators have to implement different MFA solutions for different services that are in use by their company, then install this additional software on every user’s device. Needless to say, all this software has to be maintained and regularly updated. Protectimus DSPA is a brilliant solution for this issue, integrating it with AD adds Active Directory one-time password to every single service and platform attached to AD.
| Read also: 2FA Security Flaws You Should Know About
What authentication methods are available
As has already been mentioned above — with DSPA the admin can set any time step for the dynamic Active Directory password reset – 30, 60 or even 3000 seconds. So the token that generates and delivers the OTP has to accommodate this feature too. Currently, there are two methods of two-tier authentication with DSPA available — 2FA mobile application Protectimus Smart OTP and custom hardware tokens. The third one — chatbots, is currently in the works and will be released soon.
1. 2FA app
Our free 2FA application Protectimus Smart OTP is available for both Android and iOS and can be used not only for 2-factor authentication Active Directory but for other sites and services protection too. The app allows for setting the OTP change schedule to multiple units of 30 seconds, so you can set it to 30, 60, 90, etc. which makes it the best option for OTP delivery for MFA Active Directory.
2. Hardware tokens
Classic hardware tokens for two-factor authentication come with factory-applied time-lag for the password change, it can be 30 or 60 seconds. Hardware tokens for 2FA Active Directory with any other timestep are available as custom orders only. The price for these custom tokens is a bit higher than those we have for order on the website, chat with us to learn more.
| Read also: The Pros and Cons of Different Two-Factor Authentication Types and Methods
How to set it up
Configuring Protectimus platform for Windows Active Directory protection is rather easy and straightforward:
- Install Protectimus on-premise platform and the DSPA component.
Contact us via [email protected] to request the platform with the DSPA component for download.
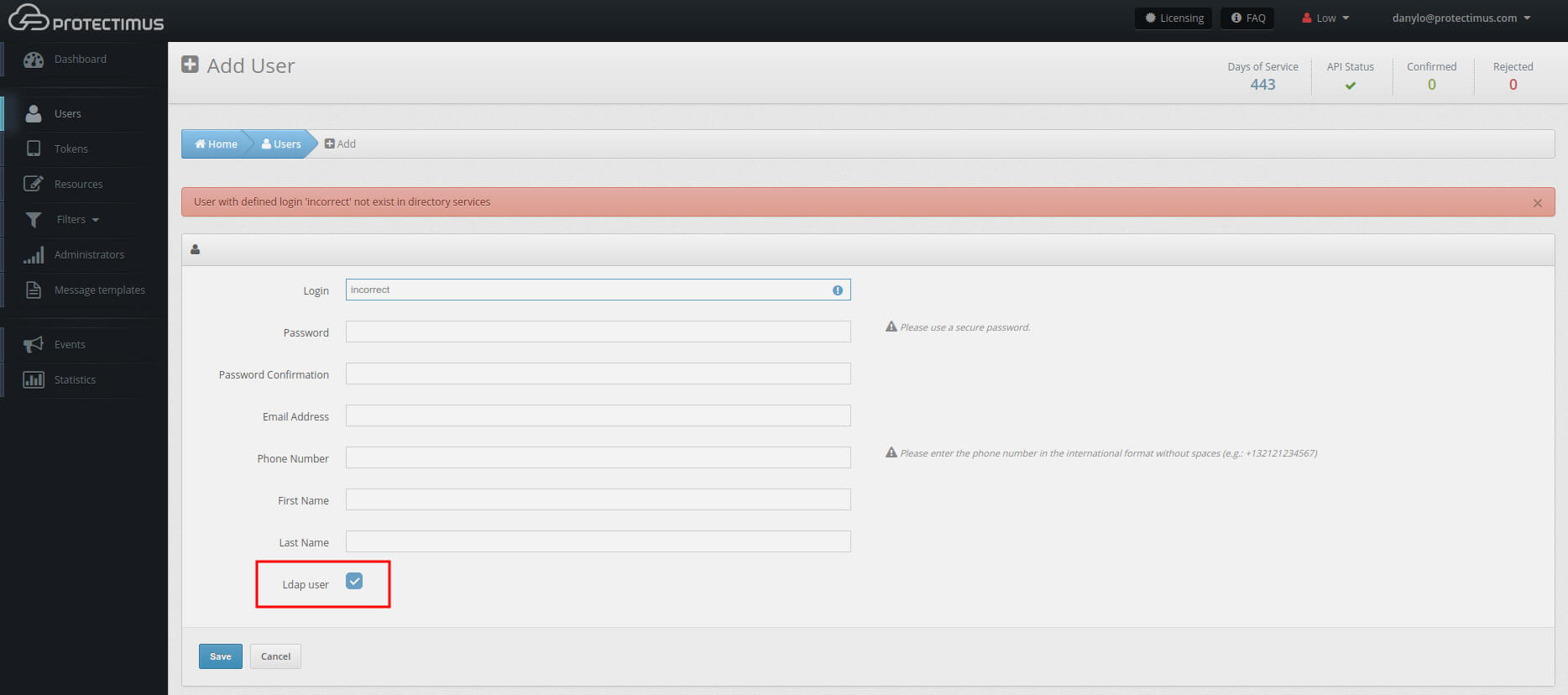
- Add users.
Make sure to check the LDAP User checkbox at the bottom. The user Login used here must match the Common Name in AD. It’s also required to specify the Email Address for each user.

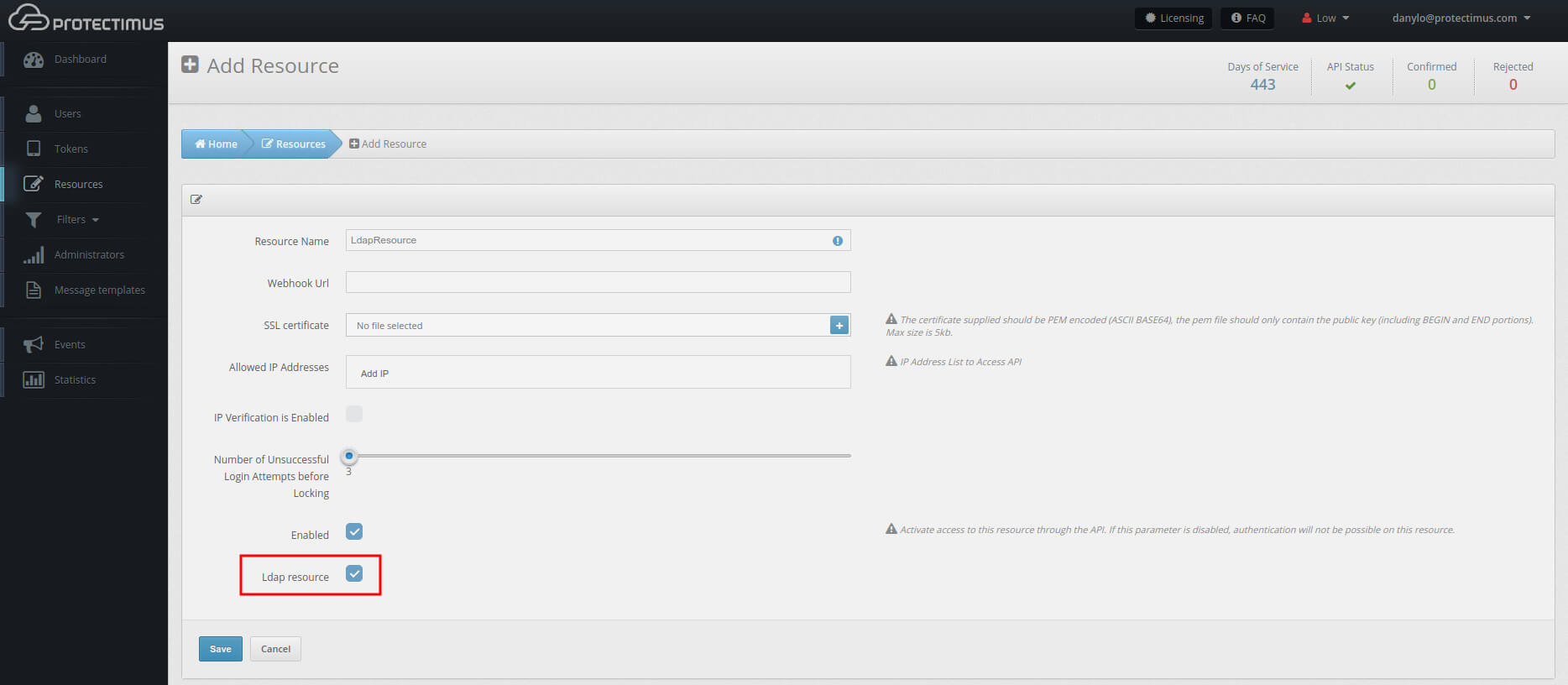
- Create a resource.
Here too, make sure to check the LDAP checkbox at the bottom.

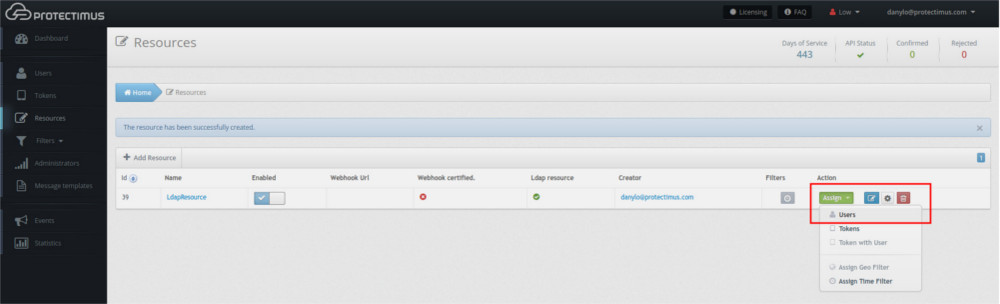
- Assign Users to the Resource.

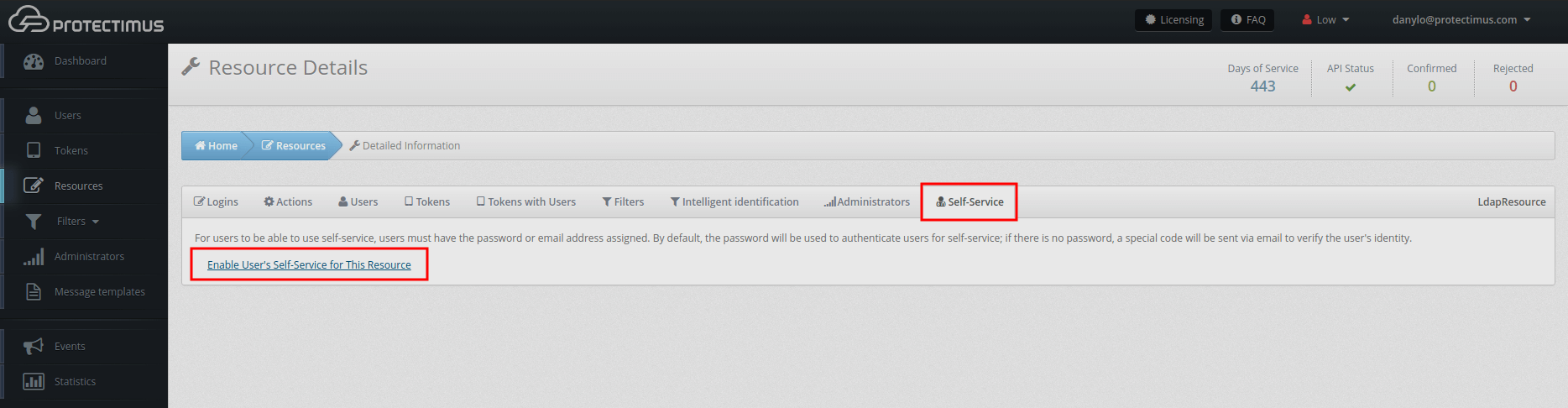
- Activate Self-Service.
Clicking on the resource name you created. Go to the Self-Service tab and click “Enable User’s Self-Service for This Resource”.You will be asked to specify the part of the address at which the Self-Service will be available to your users? For example, if you enter “protectimus”, your Self-Service address will be https://service.protectimus.com/selfservice/protectimus

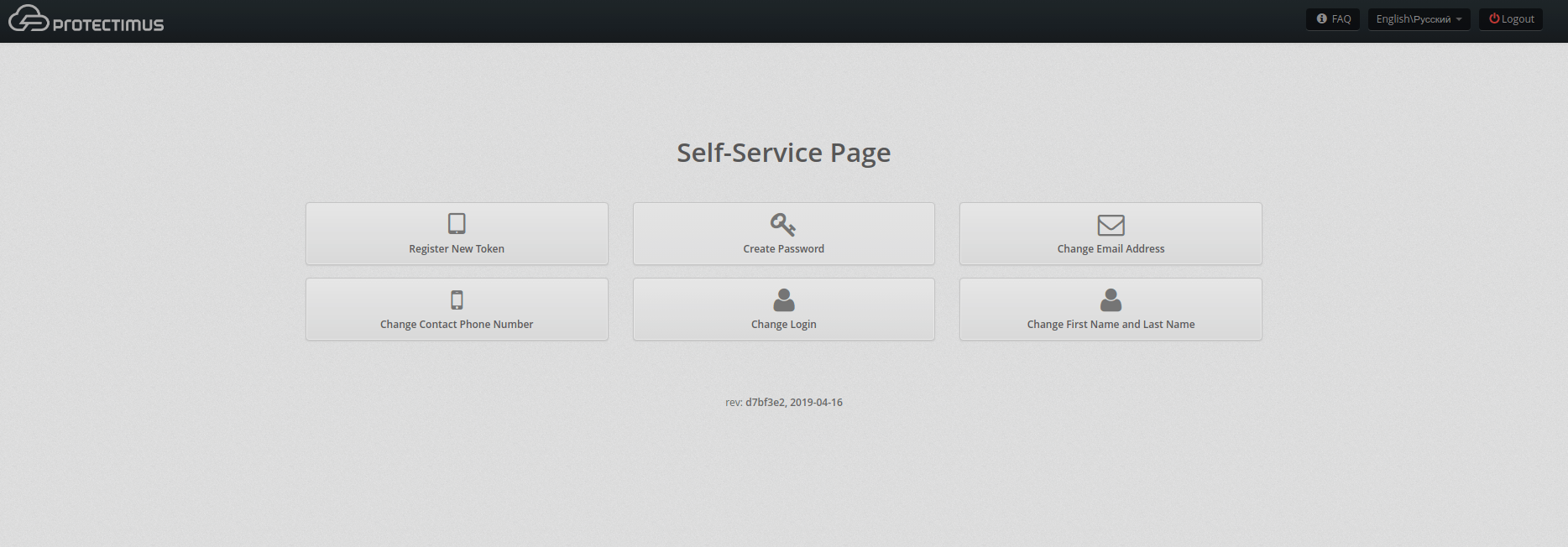
- Give this link to your users to create tokens and static passwords.
Users will need to login to the self-service page using their Logins (CN) from step 2 and the OTPs that will be sent to emails you also specified in step 2.
On the Self-Service page, the users will be asked to Register New Token (the administrator should inform the user what time step to set up) and to Create a Password (the password must match their AD static password).
| Read also: Hardware Tokens for Azure MFA
FAQ on Active Directory two-factor authentication
The price depends on the number of users. The minimal price is $199 for up to 181 users.
As we’ve already mentioned — DSPA operated through direct AD integration, and as such it allows to protect any system attached to AD. Among these are OWA, ADFS, Azure, Windows, Office 265, Jira, etc.
To start testing install and run the Protectimus MFA platform and integrate it with your AD. The minimum tech requirements are Java (JDK version 8), PostgreSQL DBMS, ver10 or later. Contact [email protected] for the installation package and detailed instructions.
Protectimus DSPA allows you to add two-factor authentication directly in any database or user directory, including Active Directory, LDAP, etc.
Read more:
- Duo Security vs Protectimus
- 4 Reasons Two-Factor Authentication Isn’t a Panacea
- Time Drift in TOTP Hardware Tokens Explained and Solved
- Electronic Visit Verification with Hardware Tokens
- 10 Steps to Eliminate Digital Security Risks in Fintech Project
- Keycloak Multi-Factor Authentication With Hardware Tokens
- Sophos 2FA with Hardware OTP Tokens
- 2FA Chatbots vs. SMS Authentication
- Office 365 MFA Hardware Token
- Man In The Middle Attack Prevention And Detection
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


2020-06-18
Hello, what about when the computer is not connected to the company network?
Like a laptop… when the user get home and need to login, which password he will type then?
Thanks
2020-06-18
Hi Ben,
If to talk about Windows, by default, when there is no connection with the domain controller, Windows allows logging in with the last password that has been used for successful login. The user should predict the situation and save the last password they use to login to their account when they are still online. You can always disable this function, but then the user won’t be able to log in to their account offline.
Also, the user may have an additional account on the same computer that won’t be protected with two-factor authentication, just in case of such offline scenarios.
2021-01-04
How does it work with ActiveSync? the mobile activesync applications will check the credentials periodically and if it has changed it won’t work.
2021-01-13
Hi Mohammad, it’s to be tested but, most probably, Dynamic Strong Password Authentication technology won’t support ActiveSync. The main purpose of the Dynamic Strong Password Authentication (DSPA) component is to let AD administrators protect with 2FA all their users, who connect to Active Directory from several different services, without performing dozens of integrations and installing dozens of plugins. ActiveSync is more about convenience for the end-user, while DSPA is about security and ease of implementation. There is always a trade-off between convenience and security.
2021-05-06
We are looking to use this solution only for our IT department users. Can it be configured to apply the requirement for MFA only to a specific group in AD or does it have to be all AD users?
2021-05-13
Hi Mark, sure, with Protectimus DSPA you can apply the requirement for MFA only to a specific group in AD.