Without a doubt, Tesla’s electric cars are the best vehicles on the market right now. They attract people with modern design, high efficiency, and the low cost of maintenance and operation. These vehicles are generally considered pretty theft-proof, thanks to always-on GPS which lets owners track their cars. But numerous smart features still make these cars extremely vulnerable to hacking. That’s how the two-factor authentication has become one of the most awaited things among Tesla users.
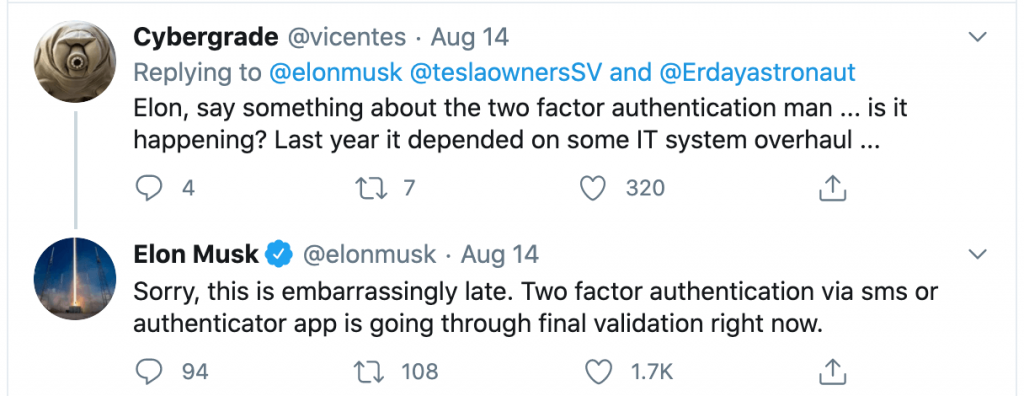
The good news is that the Tesla CEO Elon Musk has recently twitted that 2FA is now on the way. He doesn’t provide a timeline, but admits that this is “embarrassingly late”.
Why Tesla users are looking forward to 2FA
Firstly, what is two-factor authentication? It implies a request for data of different types, due to which it provides reliable protection against hacks and virus attacks. Usually, a person must enter a username and password (something they know), and then confirm the entry into the system by specifying the confirmation code sent to their phone (something they have) by e-mail, SMS, and chat-bot in the messaging app, or generated by the 2FA app or hardware authentication token. In some cases, it is possible to request biometric data (scanning of the eye retina, fingerprints voice recognition) – something they are.
At the moment, you only need a username and password to log in and unlock your car with Tesla apps. Imagine that someone recognized them. Fraudsters can simply install the application on their phone and get access to many of the functions of your electric car.
Two-factor authentication minimizes the risk of this and provides strong protection for your account.
| Read also: 6 Multi-Factor Authentication Myths You Still Believe
Tesla app two-factor authentication options to choose
If to believe Elon Musk, two MFA methods will be available to the Tesla app two-factor authentication users: SMS and 2FA applications. This means that most probably programmable hardware tokens Protectimus Slim NFC and Protectimus Flex will also fit as they are designed to replace 2FA apps.
SMS authentication
SMS two authentication is one of the most popular solutions. It is convenient and saves time on installing additional applications and buying individual hardware tokens.
It cannot be denied that SMS authentication is safer than simply entering a username and password. But it also has several disadvantages:
- The risk of replacing the SIM card;
- Cellular network vulnerabilities;
- Smartphone viruses.
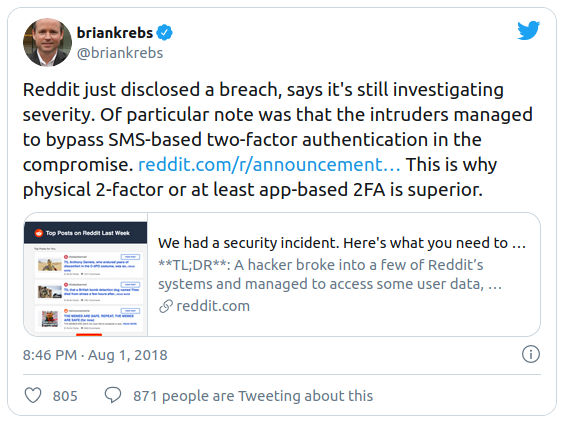
We described all these issues with SMS authentication in detail here. Of course, hacking your account won’t be as easy as it is now when the Tesla app works without two-factor authentication at all, but better choose any other 2-factor authentication method.
2FA apps
The second popular solution is MFA applications that generate one-time passwords on your smartphone. In this case, OTP passwords are not transmitted over any network, which eliminates half of the risks.
This type of two-factor authentication is much more reliable than SMS. But it also has its drawbacks. Every time you connect to the network, you make your smartphone vulnerable. Any downloaded application can go with a virus.
Programmable hardware token
As a rule, if the application supports two-factor authentication with the help of an in-app authenticator, you can also connect the Protectimus Slim NFC or Protectimus Flex hardware token for the Tesla app two-factor authentication.
Protectimus Slim NFC and Protectimus Flex are programmable TOTP tokens that can be connected almost to any service just like a 2-factor authentication application – by scanning the QR code that shows the secret key. You install the Protectimus TOTP burner app on your Android smartphone (note that the phone must support the NFC feature), scan the secret key with the help of this app, and then you add this secret key to the token via NFC. You can read more about Protectimus Slim NFC tokens and how to connect them to any website or app you need here.
The only thing you should be prepared for is that the size of the secret key in the Base32 format should not exceed 32 characters. There is no information yet what secret keys the Tesla app will use, but our programmable hardware token may become the most reliable option.
Hardware OTP token is a separate device that generates one-time passwords autonomously and doesn’t connect to any networks. Hardware tokens are usually produced in the form of plastic cards, USB flash drives, or key fobs. They have just a single purpose: to generate one-time passwords. These tokens exclude the risk of one-time passwords interception or being infected by viruses.
| Read also: The Pros and Cons of Different Two-Factor Authentication Types and Methods
Conclusions
Obviously, Tesla’s news has cheered up a large number of electric car owners, as well as those who are just thinking about buying a car. They can now sleep more peacefully.
But there are also users who have taken this Elon Musk security news without great enthusiasm. They want to have the SMS, app, or token authentication just as an option, without the necessity to generate the one-time password always when they need to unlock the vehicle, locate it, flash its lights, and so on.
Please, remember that Teslas are more like computers on wheels than traditional cars, so they have the computers’ advantages and weaknesses. Use the 2-factor authentication wherever it is possible, as it is the best way to ensure your digital security these days.
Read more
- Two-factor authentication for Windows 7, 8, 10
- How to Transfer Google Authenticator to New iPhone
- How to Secure Bitcoin Wallet
- 9 Must-Follow Gmail Security Rules
- PayPal Two-Factor Authentication with Hardware Security Key
- Twitter Two-Factor Authentication in Details
- 2FA Security Flaws You Should Know About
- Remote Work: How to Transition Team to Working From Home During the COVID-19 Pandemic
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!