Introducing Protectimus SHARK, a cutting-edge hardware TOTP token that supports the SHA-256 hashing algorithm. With Protectimus SHARK, you get a reliable authentication device that generates one-time passwords with unmatched security. Unlike older OTP tokens that used SHA-1, Protectimus SHARK takes a step ahead with the more up-to-date and secure SHA-256 hashing algorithm. This advanced token authentication solution creates an impenetrable barrier against unauthorized access and cyber threats, making it a vital part of a strong 2FA strategy.
In this article, we’ll explore the unique advantages of Protectimus SHARK as a TOTP token with SHA-256 algorithm support. Discover its exceptional features and benefits that set it apart from other authentication methods. Learn how Protectimus SHARK enhances the security of your online accounts and data, ensuring a safer and more reliable authentication experience.
1. Understanding TOTP Tokens and Hashing Algorithms
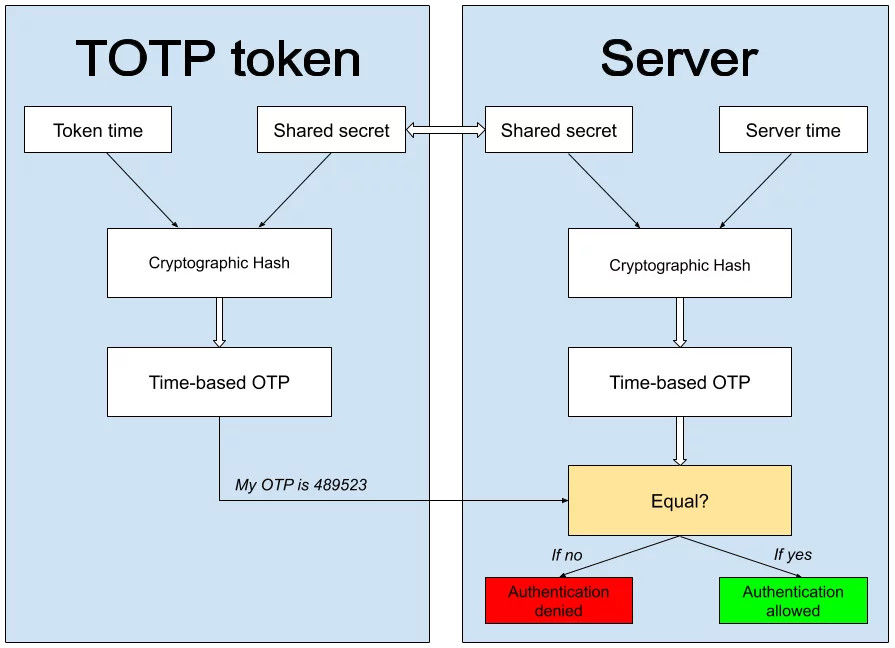
Two-factor authentication (2FA) has emerged as a powerful defense mechanism to fortify traditional password-based security. At the core of 2FA lies Time-based One-Time Password (TOTP) tokens, which play a crucial role in generating time-sensitive one-time passwords for enhanced security.
TOTP tokens serve as a second factor of authentication, providing an additional layer of protection beyond traditional passwords. These small, portable devices generate unique one-time passwords that are valid for a short period, typically 30 or 60 seconds. The dynamic nature of TOTP tokens adds a time-based element, making it extremely difficult for attackers to predict or reuse passwords, even if they manage to intercept them.
To ensure the integrity and security of TOTP tokens, robust hashing algorithms come into play. Hashing algorithms are mathematical functions that convert sensitive data, such as shared secrets and current time, into fixed-length hash values. One of the most critical components of TOTP token generation is the choice of a hashing algorithm, as it directly impacts the strength and security of the one-time passwords generated. Use an online TOTP token generator to see how the TOTP algorithm works.
Among the various hashing algorithms, SHA-256 stands out as a widely adopted and highly secure choice for TOTP token generation. SHA-256, a member of the SHA-2 family, produces a 256-bit hash value, making it substantially stronger than its predecessor, SHA-1, which generates a 160-bit hash value. This increased hash size significantly expands the potential hash space, making it exceedingly difficult for attackers to reverse-engineer or guess the original input based on the output hash.
Compared to the SHA1 hashing algorithm commonly used in TOTP tokens, SHA-256 offers a higher level of cryptographic protection. SHA-1 has been found to possess vulnerabilities, which could potentially compromise the security of TOTP tokens. Therefore, the adoption of SHA-256 in TOTP token generation is crucial to stay ahead of emerging security threats.
In the following sections, we will explore the advantages of Protectimus SHARK, a cutting-edge TOTP hardware token with SHA-256 support, and how it elevates the security of online accounts and data in a rapidly evolving digital world.
| Read also: Time Drift in TOTP Hardware Tokens Explained and Solved
2. Introducing Protectimus SHARK TOTP Token
Protectimus SHARK is a cutting-edge TOTP hardware token that takes two-factor authentication (2FA) to a whole new level. Designed with the latest security measures in mind, Protectimus SHARK stands out with its robust support for the SHA-256 hashing algorithm, making it a powerful weapon against cyber threats.
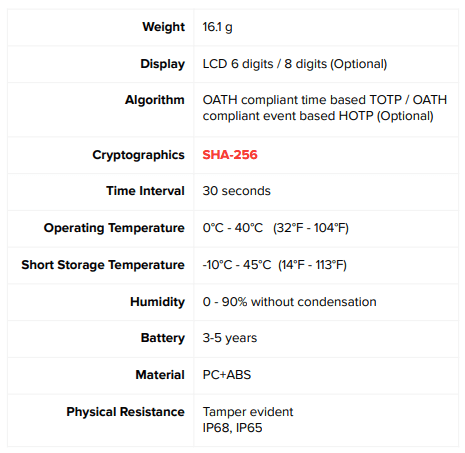
Let’s delve into what sets Protectimus SHARK apart from the rest. Its physical attributes are built for convenience and durability. The token’s compact and lightweight design allows for easy portability, fitting perfectly on your keychain for on-the-go access. Plus, its sturdy construction ensures long-lasting performance, making it ideal for daily use without compromising security.
Protectimus SHARK’s core strength lies in its robust support for the SHA-256 algorithm. Unlike previous generations of TOTP tokens that supported the weaker SHA-1, Protectimus SHARK adopts the more up-to-date and secure SHA-256 hashing algorithm. This upgrade vastly enhances the security of one-time password generation, reducing the risk of unauthorized access to your online accounts.
Protectimus SHARK is also easy to integrate with standard TOTP systems. Whether you use Protectimus Cloud Service, an On-Premise Platform, or any other 2FA service supporting SHA-256 TOTP tokens, Protectimus SHARK effortlessly aligns with your existing authentication infrastructure.
Please note that Protectimus SHARK tokens are produced with embedded secret keys that cannot be reprogrammed by the end-user. To synchronize the secret keys with the 2FA server, you will need access to the two-factor authentication server.
In the following section, we will delve deeper into the unique advantages of the SHA-256 hashing algorithm supported by Protectimus SHARK, exploring how it elevates your authentication experience and fortifies your online security.
| Read also: The Pros and Cons of Different Two-Factor Authentication Types and Methods
3. Advantages of SHA-256 in Protectimus SHARK TOTP Token
Protectimus SHARK is an advanced TOTP hardware token, and one of its key strengths lies in its support for the SHA-256 hashing algorithm. Let’s delve into the advantages of SHA-256 and understand how this robust encryption elevates the security of Protectimus SHARK TOTP tokens.
Strong Cryptographic Foundation
SHA-256 provides a solid cryptographic foundation for generating one-time passwords in the Protectimus SHARK hardware token. As a hash algorithm, SHA-256 converts the user’s shared secret and the current time into a fixed-length string of characters, also known as the hash value. The crucial property of SHA-256 is its one-way process, making it virtually impossible to reverse-engineer the original input from the hash value. This ensures that the sensitive data, including the user’s password and TOTP secret, remains well protected.
Larger Hash Size Compared to SHA-1
An essential advantage of SHA-256 over weaker hashing algorithms, such as SHA-1, is its larger hash size. While SHA-1 produces a 160-bit hash value, SHA-256 generates a much larger 256-bit hash value. This increased hash size expands the potential hash space, making it exponentially more difficult for attackers to guess or reverse-engineer the original input based on the output hash. The larger hash size of SHA-256 adds an extra layer of security to the one-time passwords generated by Protectimus SHARK OTP tokens.
Resilience Against Collision Attacks
SHA-256’s robustness also lies in its resistance to collision attacks. In the context of TOTP tokens, a collision attack occurs when two different inputs produce the same hash value, potentially leading to security vulnerabilities. SHA-1, unfortunately, has known weaknesses in this regard, whereas SHA-256 has been designed to be highly resistant to collision attacks. This property ensures the integrity and security of one-time passwords generated by Protectimus SHARK.
Compliance with Industry Standards
SHA-256 is widely recognized as a secure and recommended hashing algorithm by organizations such as the National Institute of Standards and Technology (NIST) and the Internet Engineering Task Force (IETF). Its adoption in Protectimus SHARK aligns with industry best practices and security standards, providing users with peace of mind regarding the reliability and robustness of their authentication experience.
| Read also: The Advantages of SHA-256 over SHA-1 for TOTP Token Security
4. Conclusion: Embracing SHA-256 with TOTP Token Protectimus SHARK
Protectimus SHARK is a reliable hardware TOTP token that sets new standards in two-factor authentication (2FA) by incorporating the powerful SHA-256 hashing algorithm. By adopting the SHA-256 algorithm, Protectimus SHARK strengthens the security of one-time password generation, creating an impregnable defense against unauthorized access and cyber threats.
By adopting SHA-256 over weaker alternatives like SHA-1, Protectimus SHARK takes a giant leap forward in protecting sensitive data. The larger 256-bit hash size offered by SHA-256 adds an extra layer of defense, making it incredibly challenging for attackers to decipher the original input from the output hash. This robust encryption ensures that one-time passwords remain secure and untampered, significantly reducing the risk of unauthorized access.
Moreover, Protectimus SHARK’s resilience against collision attacks ensures the integrity of one-time passwords, safeguarding against potential security vulnerabilities. Compliance with industry standards, as recognized by NIST and IETF, further solidifies Protectimus SHARK’s credibility as a secure authentication solution.
In conclusion, Protectimus SHARK’s user-friendly design and integration capabilities make it an ideal choice for enhancing the security of various online accounts and services. By leveraging the advanced features of Protectimus SHARK TOTP tokens, our clients can enjoy a safer and more reliable authentication experience, defending their users against the ever-evolving landscape of digital threats.
5. Read Also
- Authenticator App Protectimus SMART Updated – Now With Encrypted Cloud Backup
- Protectimus MFA Prices: How to Save with Coupons, Discounts, Referrals, and Subscriptions
- New Programmable TOTP token Protectimus Flex
- TOTP Tokens Protectimus Slim NFC: FAQ
- 2FA Chatbots vs. SMS Authentication
- Protectimus Customer Stories: 2FA for DXC Technology
- Protectimus Customer Stories: 2FA for Advcash
- Protectimus Customer Stories: 2FA for SICIM
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!