Out-of-band authentication (OOB) is one of the most popular types of two-factor authentication in the financial sector. It presupposes sending the one-time password to the user via a communication channel other than the main one, which is used for transactions on the Internet.
Most often, during the OOB authentication, the OTP (One Time Password) is sent to the clients in the form of a text message via SMS or email and the company does not have to spend money to buy tokens or to require from users to install additional software on their smartphones. It must be noted that the Protectimus company also develops a new technology for out-of-band authentication – two-factor authentication with Push messages. This method is much cheaper than SMS authentication.
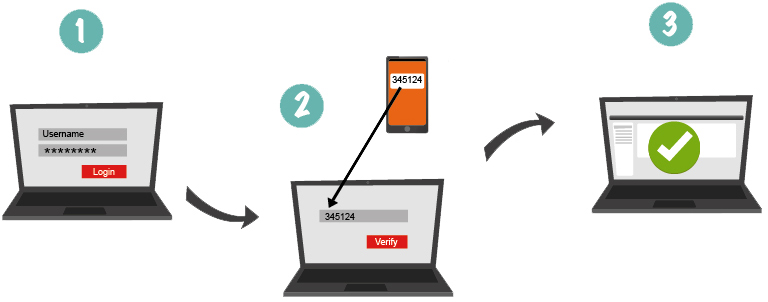
Out-of-band authentication is widely used in financial, banking institutions, and other organizations with high security requirements for the transaction. This type of protection significantly complicates the process of hacking, since for a successful theft of money or data a hacker should compromise two separate independent channels. This method of protection from unauthorized access is quite widespread and easy to use, but its security is under a great doubt because there is always the threat of man-in-the-middle attack
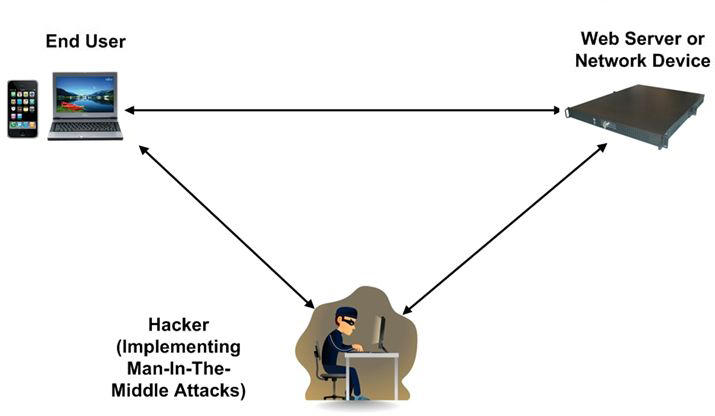
Man-in-the-middle attack
According to the results of surveys of financial institutions staff, the man-in-the-middle attack is the most serious threat to online banking, e-business and payment gateways. Zeus, Sinowal, Carberp, and Clampi are the most widespread maleficent programs for this type of attack.
The method of the man-in-the-middle attack involves compromising of the intermediary link, the penetration in data transfer protocol, the interception and substitution of correspondents’ messages, deletion or falsification of data while both sides are sure of the legality of the operations. Scenarios of such an attack can vary – the change in the connection parameters between the client and the server, the interception and substitution of public key exchange links between the client and server, the introduction of SQL-injection to grab an authorized session, data modification, Automated Transfer Systems, malware like banking trojans, but they are all aimed at gaining access to the customer’s account and conducting financial fraud behind his back.
To protect transactions from some of these attacks, such as data modification and Automated Transfer System, the best solution is a function of transaction data signing called CWYS (Confirm What You See). In the tokens that support this function, while generating one-time passwords, not only the secret key and the parameters of time / event / challenge-response (depending on the algorithm) are used, but also some additional information – the currency, the recipient, the amount of the transfer, etc. Thus, an attacker cannot use the one-time password generated for a particular transaction, to initiate another transaction. This feature is supported in such tokens as Protectimus SMS, Protectimus Mail, and Protectimus Smart.
It is worth noting that the weak link for the out-of-band authentication is the use of smartphones for making online payments. Making a payment with the same phone, which receives a message with an OTP password, the user literally ‘puts all his eggs in one basket’.
Two-factor authentication, in this case, has no efficiency, because if the virus is already on your phone and the attacker conducts an illegal operation, penetrated to this smartphone, nothing will prevent him from intercepting the one-time password sent to the same phone.
Today SMS authentication has become more reliable than ever before, thanks to the introduction of the CWYS feature. Although, a cheaper option for making online transactions is a completely free Protectimus Smart app for smartphones running on the Android platform and for iPhone. But the most reliable alternative is to use hardware tokens Protectimus One, Protectimus Ultra, and smart cards Protectimus Slim. The use of such tokens greatly complicates the process of the account compromising and completely excludes the possibility of the man-in-the-middle attack.
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


2016-01-12
Dear Ann,
Nice article,
The OOBA Technology has evolved and there are solutions which are make OOBA more safe and secure to use.
OOBA can be originating from same mobile phone and can also authenticate from same phone with completely encrypted isolated channel.
When ever you are ready to write any column with update OOBA info I can surely contribute.
Kind Regards,
Masood.
2016-01-12
Dear Masood, thank you for the response. We are always open for expert’s contributions. You may submit an article at [email protected]. If it is informative, interesting and doesn’t contain an evident advertising, you will become our guest editor, and we’ll publish it with the great pleasure.
2017-05-04
Asking questions are in fact nice thing if you are not understanding anything entirely, except this post provides pleasant understanding yet.
2017-05-24
Very good blog you have here but I was curious about if you knew
of any user discussion forums that cover the same topics talked about here?
I’d really like to be a part of group where I can get feed-back from other experienced people that share the same interest.
If you have any suggestions, please let me know.
Kudos!