There are currently two ways to implement an Azure hardware token for Azure Multi-Factor Authentication:
- With classic OATH tokens for Azure MFA with hard-coded secret keys, such as Protectimus Two. To make use of one of these you’ll need Azure AD Premium P1 or P2 license.
- With a programmable hardware token for Azure MFA Protectimus Slim NFC or Protectimus Flex which is a replacement for an authentication app from Microsoft. This Azure cloud MFA hardware token does not require a premium subscription account.
In this article, we will describe how to set up both types of hardware tokens for Azure token-based authentication. All three devices can be bought here.
Classic OATH hardware tokens for Azure MFA – how to set up
Currently, Azure AD supports tokens with passwords not longer than 128 characters and password life-span of 30 and 60 seconds. Protectimus Two hardware OTP tokens fit these requirements.
Once you choose and receive the Azure MFA OATH token you prefer you need to register your token with Azure. Below is the step-by-step guide on this simple process:
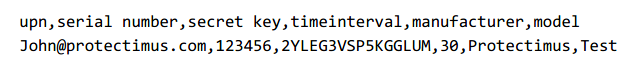
Step 1. Prepare a CSV file that includes your UPN (user principal name), the serial number of the hardware token Azure MFA, the seed (secret key), time interval, make and model of the Azure AD MFA hardware token. Make sure to include a header row, the result should look something like this:
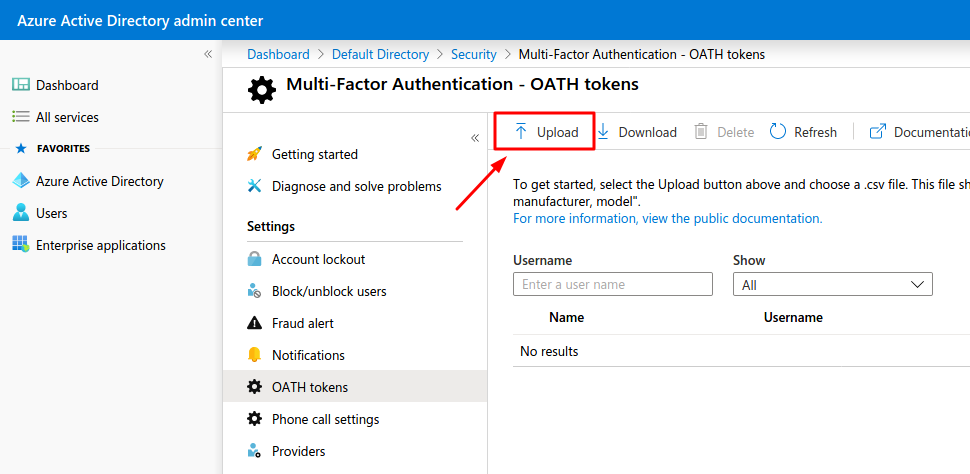
Step 2. Once the CSV file is created and properly formatted it has to be imported. Go to Azure Portal and browse to Azure Active Directory, then to Security and to Multi-Factor Authentication. On the MFA page choose OATH tokens and click the “Upload” button. Upload your CSV file; the upload process might take a few minutes.
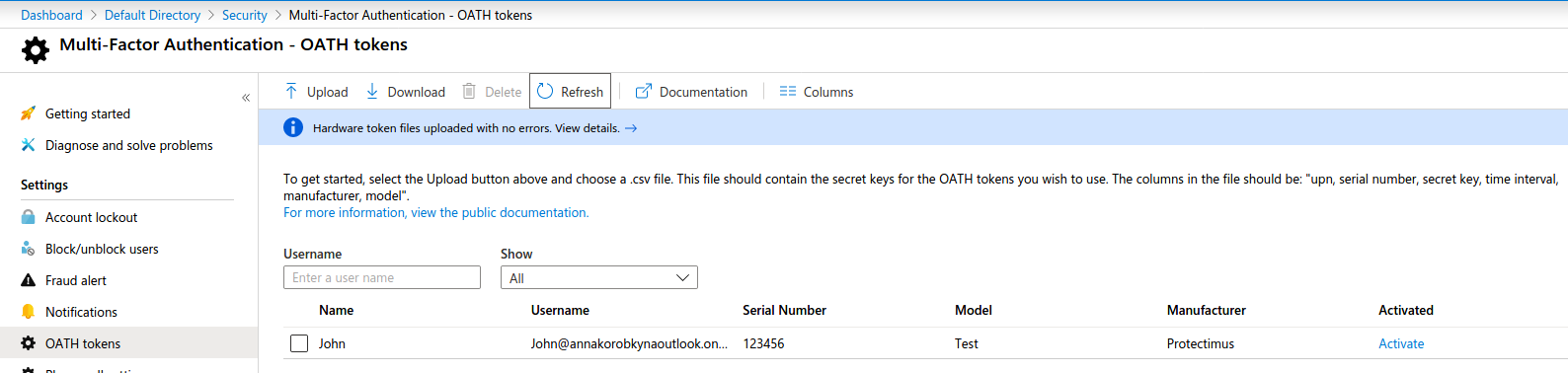
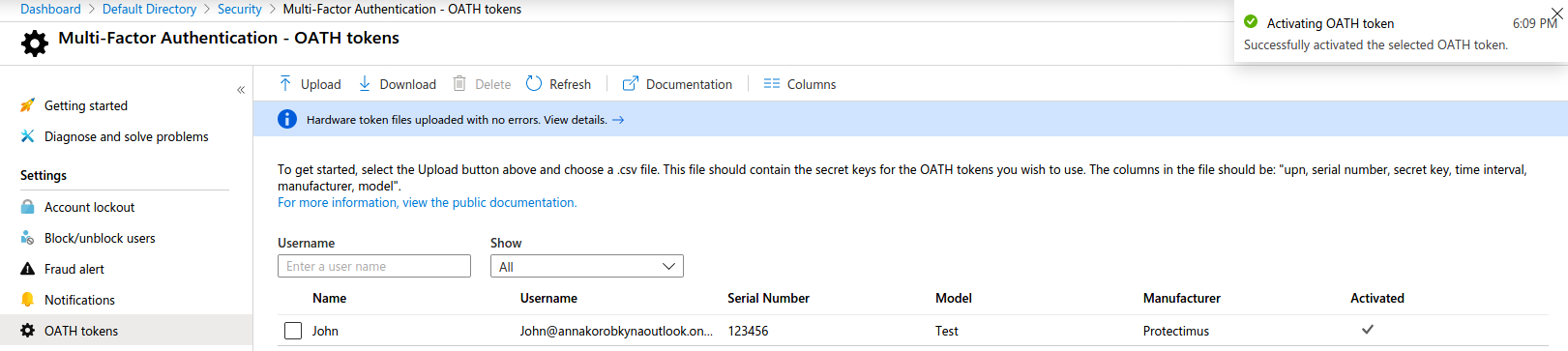
Step 3. Click the “Refresh” button. If the CSV file was uploaded successfully you will see a list of your Azure AD hardware tokens, if the file had an error you will be notified on the same page:
File uploaded successfully:
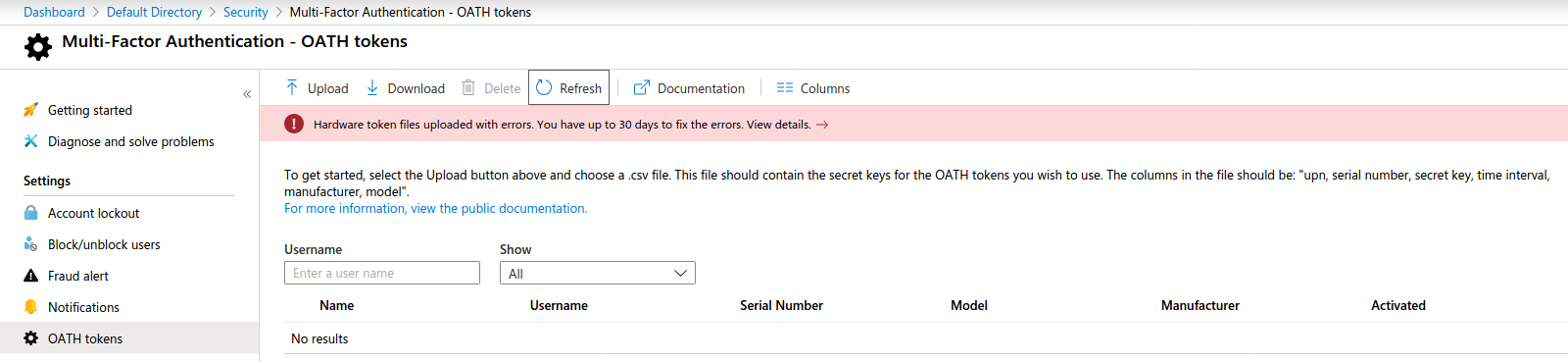
File uploaded with errors:
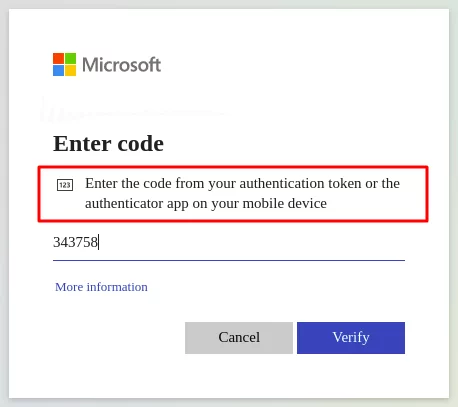
Step 4. Now you need to activate your Azure multi-factor authentication hardware token. If you have multiple tokens, you should activate them one by one. Click the “Activate” button at the lattermost column on the right and enter the password generated by the corresponding Azure MFA token. After that, click the “Verify” button.
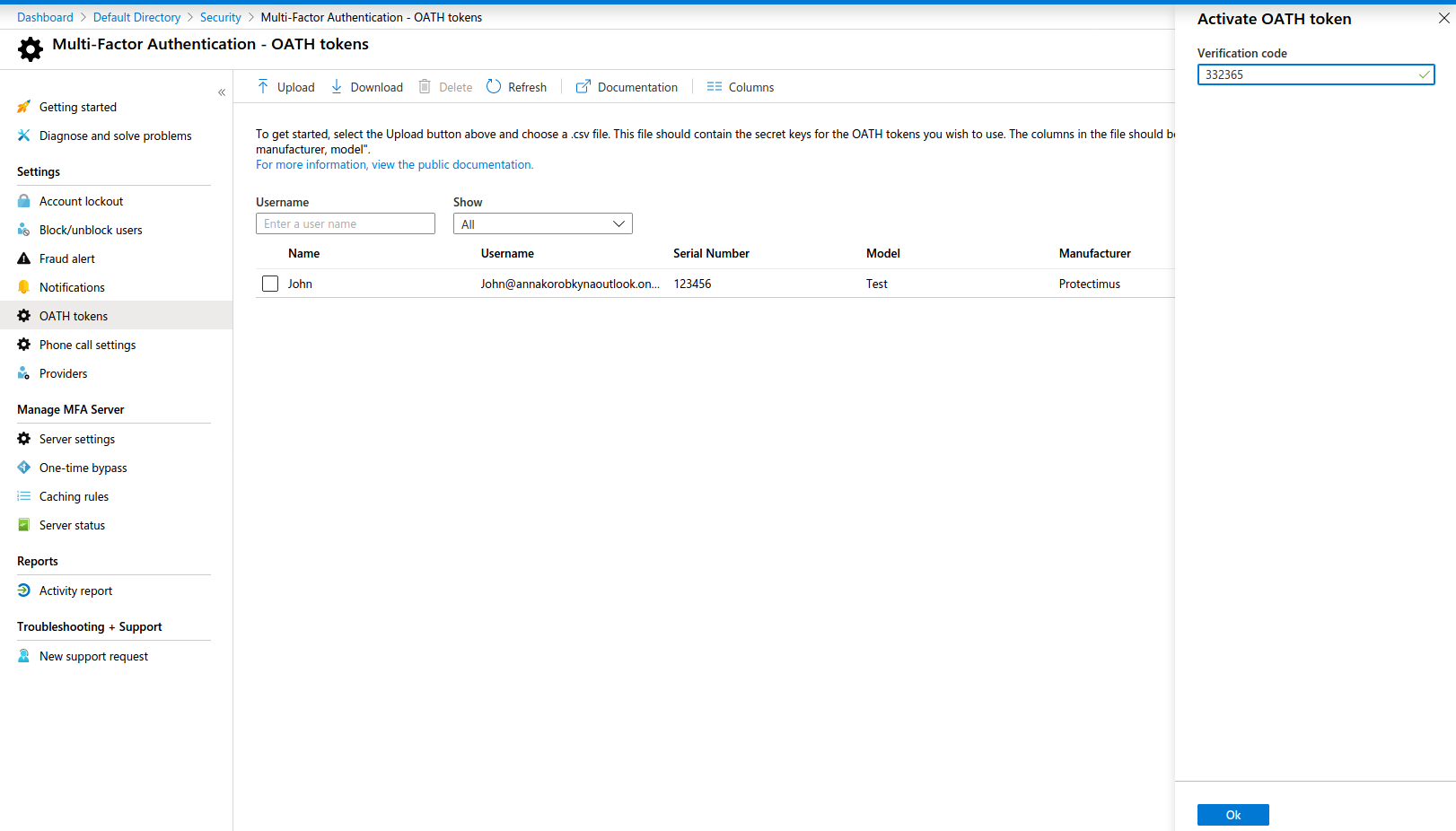
Step 5. Once the MFA server accepts your one-time password you will get a message confirming the activation of the Microsoft Azure token you selected from the list and there should appear a check mark in the corresponding “Activated” column. Now your token is successfully activated and can be used to log in.
Step 6. 2FA settings in the user account.
OATH tokens will be automatically set as a main 2FA method.
NOTE! If any other 2-factor authentication method is registered for a user, they can use several two-factor authentication methods at once. For example, I activated a 2FA app Protectimus SMART as a 2FA methos, in this case, both one-time passwords from hardware token and 2FA app will work when I enter any of them in this field:
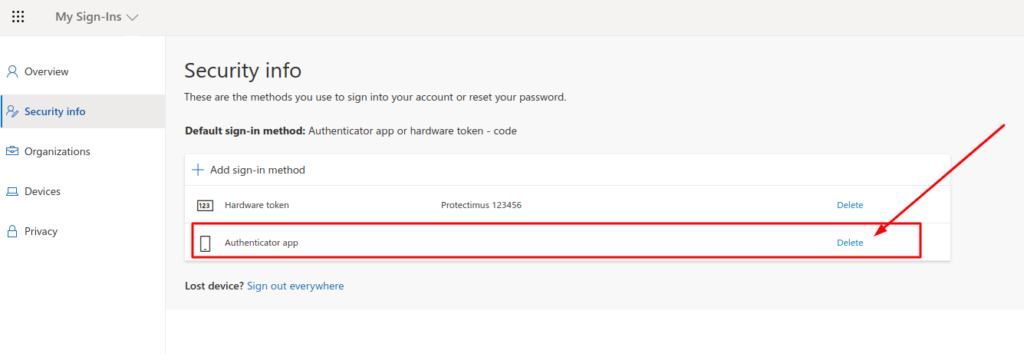
If you want to use only a hardware OATH token for Azure 2-factor authentication, login to your account and deactivate other two-factor authentication methods.
- Go to your account settings page at https://myaccount.microsoft.com/?ref=MeControl
- Navigate to the Security Info tab.
- Delete two-factor authentication methods you don’t need.
Programmable hardware tokens for Azure MFA
As has already been mentioned above – to use a classic Microsoft Azure MFA hardware token you need to have a premium subscription. But we know that not everyone is ready to pay 6 euros per month per one user. If you are not ready to pay too, programmable hardware tokens Protectimus Slim NFC or Protectimus Flex is the way to go for you. These tokens are recognized as authentication apps by the Azure MFA system, so you do not need a premium license to use them.
Adding Protectimus Slim NFC or Protectimus Flex as a recognized second factor of authentication to your Azure MFA is pretty straightforward. All you need to do is log into the MFA setup page, configure the authentication to recognize your Azure authentication token and program the device itself to be used for Azure MFA. The whole process takes mere minutes and is described in detail here.
Common questions
Microsoft does not provide any exact info on time drift with Azure MFA, but the implementation has been said to be based on RFC 6238 which suggests that the time drift is indeed supported. Azure MFA allows one-time passwords within a time range of 900 seconds, this means time drift support is not really necessary. But if you’d like to keep time drift issue under control, use Protectimus Slim NFC or Protectimus Flex tokens, which have a time synchronization feature now. The time is resynchronized when a secret key is flashed to the token.
A hardware token is by far the most bulletproof protection you can get for your data stored on a cloud. Such a device generates secure passwords without and needs no network connection whatsoever. With a hardware token you have an impenetrable wall between your data and anyone who tries to steal it. There’s simply no way for hackers to infect the device or intercept the generated codes. And if a hardware token is stolen or lost you most probably will notice it immediately, whereas with an infected app or intercepted SMS you might not know any damage is done before it’s too late.
If you want Protectimus Slim NFC you can have the device branded even if your order is as small as one token. With Protectimus TWO custom branding is offered for orders over 1000 devices.
No, this token allows for one seed at a time. But Protectimus Slim NFC can be programmed to work for a different resource once you stop using the one you initially programmed it for.
Read more:
- Office 365 MFA Hardware Token
- How to Program Protectimus Slim NFC Token
- The Pros and Cons of Different Two-Factor Authentication Types and Methods
- Why US, Canadian, and EU Universities Choose Programmable Hardware OTP Tokens
- 4 Reasons Two-Factor Authentication Isn’t a Panacea
- Windows Computer Safety Tips
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


2021-03-03
The Upload is greyed out for me. Do I have to be Global Admin or can a helpdesk role work?