Multi-factor authentication (MFA) is a well-known and effective measure of protecting access to user accounts. MFA helps to reduce the number of attacks associated with stolen login data. Due to the use of two or more different authentication factors, it’s almost impossible to access the account even if an attacker has the user’s login and password.
However, attackers constantly find new ways to bypass two-factor authentication, often exploiting human factors. One of such new growing threats based on human factor is the MFA fatigue attack.
Let’s explore what an MFA fatigue attack is and how to counter it.
What Is an MFA Fatigue Attack?
An MFA fatigue attack is a type of social engineering technique in which an attacker repeatedly triggers authentication requests, typically through push-based MFA, in order to overwhelm the user. MFA fatigue attacks are also called MFA bombing, MFA push bombing, MFA prompt bombing, or MFA push spam. The main goal of this type of attack is not to steal a one-time password, but to make the user approve a login request themselves.
In this scenario, the attacker already has valid credentials (a username and password). Instead of attempting to bypass MFA technically, they rely on persistence, timing, and psychological pressure to gain access.
This makes MFA fatigue fundamentally different from classic MFA bypass techniques such as phishing, brute force, keyloggers, man-in-the-middle, or SMS interception.
How MFA Fatigue Attacks Work?
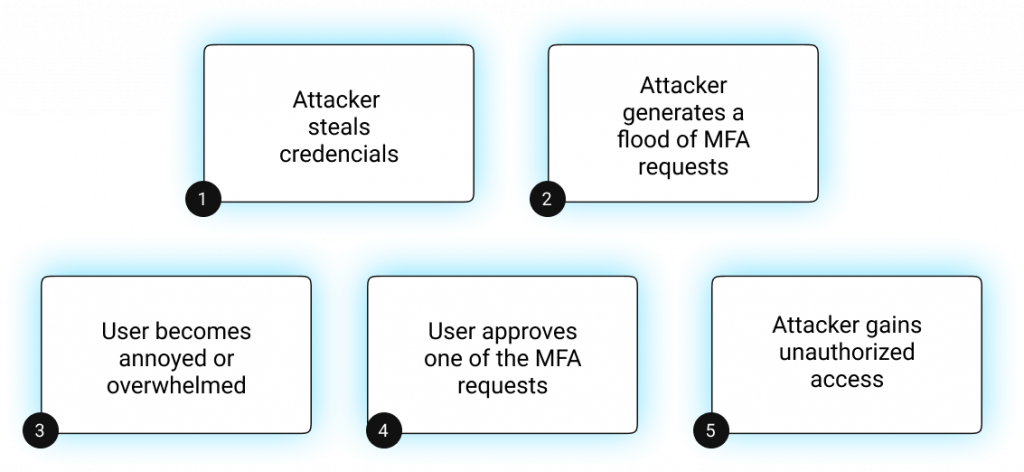
A typical step-by-step breakdown of an MFA fatigue attack looks like this:
- Credential compromise. The attacker obtains a valid username and password, often through techniques such as phishing, credential leaks, or malware.
- Repeated login attempts. The attacker initiates multiple login attempts that trigger MFA push notifications.
- Notification overload. The victim receives dozens of unexpected approval requests within a short period of time.
- Accidental approval. Due to fatigue, distraction, or confusion, the user taps “Approve” or “Yes” just to stop the notifications.
- Successful access. The attacker gains legitimate access, with logs showing a valid MFA-approved session.
Why Push-Based MFA Is Vulnerable to MFA Fatigue?
Push-based MFA is popular because of its convenience. A single tap is often all that’s required to complete authentication. However, this low friction also introduces risk.
Push notifications often:
- Provide little context about the login attempt;
- Can be triggered repeatedly without meaningful limits;
- Rely entirely on user judgment at the moment of approval.
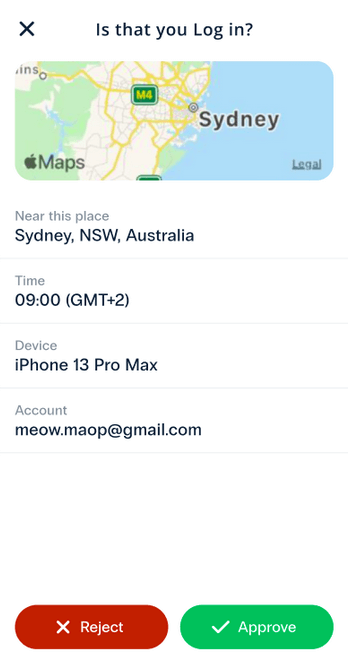
This risk can be partially mitigated by using CWYS (Confirm What You See) feature, a feature introduced by Protectimus.With this feature the push notification displays contextual details about the action being approved, making accidental or automated approvals far less likely. Alternatively, the issue can be further reduced by moving away from push-based authentication altogether and adopting alternative authentication methods, which we will discuss later.
Is MFA Fatigue an MFA Bypass or User Error?
From a technical perspective, MFA fatigue is not a cryptographic failure. MFA works exactly as designed – the system sends a request, and the user approves it.
However, from a security standpoint, MFA fatigue represents a practical MFA bypass. The attacker gains access without breaking MFA, simply by manipulating the approval process.
Because the login is successfully approved, such attacks are difficult to detect using traditional security logs. The session appears legitimate, even though it was initiated under malicious pressure.
The Human Factor Behind MFA Fatigue Attacks
MFA fatigue attacks succeed because they exploit well-known cognitive patterns:
- Alert fatigue – repeated notifications reduce attentiveness.
- Habituation – users become accustomed to tapping “Approve”.
- Context switching – requests arrive during meetings or off-hours.
- Desire to stop interruptions – approval becomes a shortcut.
Even security-aware users can make mistakes under sustained pressure. This highlights that MFA fatigue is not a failure of users, but a failure to design authentication systems around real human behavior.
Why MFA Fatigue Attacks Are Increasing?
One of the most talked-about instances of MFA fatigue attack occurred in September 2022 when an Uber EXT contractor had their account hacked by an attacker likely linked to a hacking group named Lapsus$.
Later, the Microsoft study identified over 382,000 attacks in a single year, revealing that 1% of users blindly approve the first MFA push notification they receive.
Several factors contribute to this huge rise of MFA fatigue attacks:
- Widespread availability of stolen credentials;
- Increased adoption of push-based MFA;
- Remote and mobile-first work environments;
- Low attacker effort combined with high potential reward.
How to Protect Against MFA Fatigue Attacks?
Preventing MFA fatigue attacks requires a combination of technical controls and user-level measures. The goal is to make blind approvals difficult for users and large-scale prompting ineffective for attackers.
1. Add Context to Authentication Requests
One of the main reasons MFA fatigue attacks succeed is that users are asked to approve requests without understanding what they are approving. This risk can be reduced by adding contextual information to authentication prompts.
With CWYS (Confirm What You See) data signing feature, authentication requests can display meaningful details such as the target system, action type, or request origin. When users clearly see what a request relates to, accidental or habitual approvals become far less likely.
2. Limit and Control Authentication Requests
MFA fatigue relies on the ability to send repeated authentication prompts. Organizations should limit authentication attempts and prevent unlimited request flooding.
Protectimus supports authentication policies and filters that allow administrators to restrict when authentication requests are permitted. Time-based and geo-based controls help block requests outside expected working hours or from unusual locations, stopping many attacks before users ever see a prompt.
3. Choose Another Authentication Method
Push-based MFA is convenient, but it is not the only authentication method you can use. MFA fatigue attacks specifically target push notifications because they can be approved with a single tap.
Using alternative authentication methods, such as two-factor authentication apps, hardware TOTP tokens, and chatbots in messaging apps, adds friction that attackers cannot easily exploit. These methods require deliberate user interaction and are resistant to push-bombing techniques.
4. Use Layered MFA Policies
The most effective protection comes from combining multiple controls. Contextual approvals, request limitations, and strong authentication methods work best together. This layered approach reduces unnecessary prompts for legitimate users while making large-scale MFA abuse impractical.
5. Educate Users and Encourage Reporting
Technical controls alone are not enough. Users should be trained never to approve unexpected authentication requests and to recognize repeated prompts as a warning sign. Clear internal processes for reporting suspicious MFA activity allow security teams to react quickly and prevent further abuse.
Conclusion
MFA fatigue attacks demonstrate that modern security threats increasingly target people rather than technology. Push-based MFA, while convenient, can be exploited if deployed without proper safeguards.
A resilient MFA strategy balances usability with layered controls, thoughtful policies, and user awareness.
When implemented correctly, MFA remains a powerful defense – not just against credential theft, but against the evolving tactics that seek to exploit human behavior.
Read also
- Protectimus vs ESET
- Protectimus vs Rublon
- Protectimus vs. Okta
- Passwordless Authentication with Protectimus DSPA: How it Works
- Protectimus Customer Stories: 2FA for Volet
- Protectimus Customer Stories: 2FA for SICIM
- Protectimus Customer Stories: 2FA for Ipak Yo’li Bank
- Protectimus Customer Stories: 2FA for DXC Technology
- Protectimus MFA Prices: How to Save with Coupons, Discounts, Referrals, and Subscriptions
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.

Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from Protectimus blog.
You have successfully subscribed!