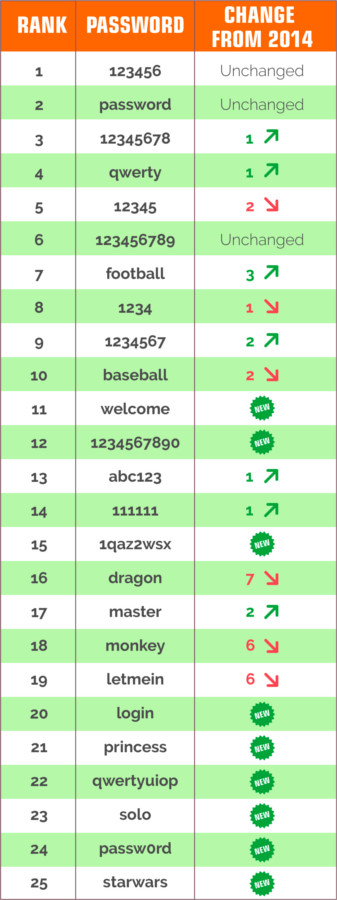
It is not a secret that the Internet users tend to choose weak and unreliable passwords. And even more! People use this weak password in almost all their accounts. And the list of the worst passwords of 2015, which was recently published by SplashData, proves that all the efforts to convince people of the importance of using strong passwords were vain.
For several years, the palm belongs to the notorious “123456” and “password”. Such loved by many key sequences as “qwerty”, “12345678“, and “1234567” didn’t lose their ground and even made some progress, becoming more popular. Moreover, there is a new variation – “qwertyuiop“. A popular password containing both letters and numbers “pasword1” was extruded with “passw0rd“, which not a bit more reliable than the first one.
It is interesting that the popularity of a new episode of the cult saga “Star Wars” caused the appearance of the new group of popular passwords. The list of 25 worst passwords of 2015 includes such words as “princess“, “solo” and “starwars“.
The list of 25 worst passwords of 2015 was formed after the analysis of more than two million passwords that appeared in the public access as a result of various leaks and hacker attacks during the year. The list of all the passwords is presented below.
Remember, all these passwords are not secure. Here you can read how to choose a strong password, which will be easy to remember, but difficult for a hacker to guess or to pick up.
But any password, whether weak or reliable, should not be the only obstacle to the intruder to your confidential data. Your account should be protected from cracking with two-factor authentication and one-time passwords. Here is an article on the principles of the two-factor authentication work and one-time passwords generation.
The worst passwords of 2015:
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


2016-01-26
I think 15th is not simple )
2016-01-27
Maxim, it is as strong as the 22nd one – qwertyuiop =)