Modern technologies have brought a lot of conveniences and opportunities into our lives, but also sharply reduced the chances of complete privacy. Photos that are not intended for prying eyes, credit card numbers, passwords for accounts in social networks and e-mail services, business documents stored in cloud services, the hand of a hacker is able to reach all this with little to no effort.
Traditionally one of the most vulnerable aspects of computer security is strong authentication. Therefore, multifactor authentication methods are constantly being improved and developed. The usual two-factor authentication, when temporary passwords are delivered by a text message, is far from being the only option. Let’s see what means of security authentication exist nowadays and what means are being developed?
1. Applications for smartphones.
According to recent studies, smartphones are used by about 50% of inhabitants of the Earth. If we take into account only the developed countries, where the problem of data protection is most acute, the numbers are even more impressive.
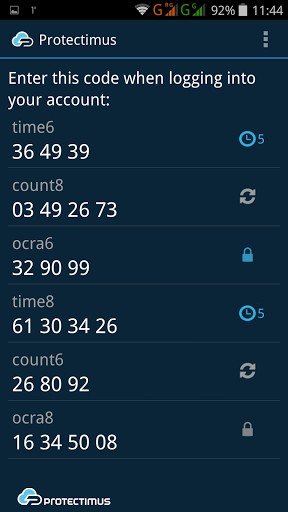
That is why applications that can turn the smartphones of the users into an OTP token are increasingly distributed. In ‘Google Play’ and ‘App Store’ you can download Protectimus‘ mobile authentication application for Android and iOS smartphones and for Android Smart Watch.
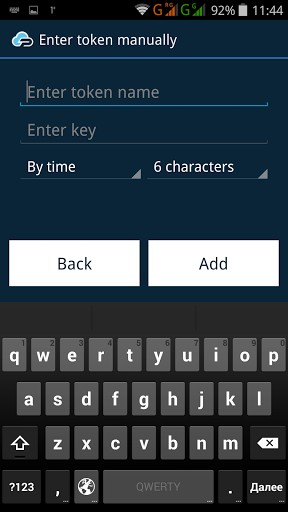
The Protectimus SMART application allows you:
- to select OTP (one-time password) generation algorithm, (HOTP, TOTP, OCRA);
- to set the length of the 2 step verification code (6 or 8 characters);
- to use the data signing function (CWYS), which protects from banking trojans and data modification;
- to create multiple tokens on a single device.
The system of data protection with the help of a software application, however, has one drawback. If the signing in the account takes place from another device (PC, laptop), the software token properly fulfills its functions. But if you go to a site with the same device on which the mobile authentication app is installed, the effectiveness of the protection will be reduced.

2. Hardware tokens.
Hardware OTP tokens can provide a higher level of information security. These devices operate autonomously; they don’t require an internet connection. In addition, one-time password token can be protected by a PIN-code to avoid unauthorized use in the case of loss or theft. Hardware tokens may look different, but they are always quite compact and small in size. For example, the ‘Protectimus Slim’ has a stylish design in the form of a credit card and TOTP token ‘Protectimus One’ is designed as a convenient key fob that can be worn together with the keys.
The ‘Protectimus Ultra’ token stands out for its reliability. Its main feature is that the secret key is generated only during the activation of the token, which means that even the developers of the OTP token don’t know the secret key in advance. ‘Protectimus Ultra’ uses the OCRA algorithm (OATH Challenge-Response Algorithm), which is currently the most reliable one-time passwords generation algorithm.

3. Biometric methods.
The previously described two-factor authentication methods are based on the one-time passwords generation while biometric techniques use different biometric parameters of the person instead of OTP passwords. Identification happens by the unique, peculiar to the only person’s individual parameters: voice, fingerprints, retina, or even selfie can act as identifiers. However, such ‘tools’, although very attractive in terms of ease of use, are not as reliable as usual and ‘boring’ one-time passwords.
4. Implementation of the implants.
Instead of the standard hardware token, which can be lost or stolen, the chip, embedded under the skin, is impossible to lose. Smartphone acts as a device for detecting a ‘key’. So far this method is still not thoroughly worked out and remains experimental. Although it is possible that it will someday become the leading method in the authentication of the users – who knows?
5. The method of comparing background noises.
Not so long ago, the Swiss developers have come up with an original idea to authenticate users using the background noise. Its essence is that when you try to log into your account, the device from which it is mad, and the smartphone simultaneously record the background noise, which surrounds the user. The records are matched on the server, and if the noises from both devices are similar, the user gets access to his account. Although the method is quite interesting, it raises some questions about the degree of its reliability.
Among them are:
- the high load on the server in the case of simultaneous processing of large amounts of data;
- the opportunity for the hacker to be in the same sound environment as the victim;
- the differences between the quality of microphones on different devices, and, as a result, differences in noise records.
It’s important to note that not two-factor, but multifactor authentication is already becoming the standard. In this case, the authentication process involves not only the OPT password check-up but also the analysis of typical user behavioral characteristics: the model and version of the browser, the place of entering the network, etc. If these and other parameters do not differ from usual, the access is possible without the entry of the one-time password. This model, which supplements traditional 2FA, is used in Protectimus two-factor authentication solution. Thus, the user can achieve both the desirable convenience and reliable data protection.
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


2017-03-07
It is in point of fact a nice and helpful piece of information. I’m glad that you just shared this useful information with us. Please stay us informed like this. Thank you for sharing.
2017-05-26
Thank you, nice article and website design simple
2017-05-28
Thank you, Very good writing
2017-07-25
Hi there! Do you use Twitter? I’d like to follow you if that would be okay. I’m absolutely enjoying your blog and look forward to new posts.
2017-07-28
I’m not sure where you are getting your info, but good topic. I need to spend some time learning more or understanding more. Thanks for great information I was looking for this info for my mission.
2017-08-22
Thank you for sharing superb information. Your website is so cool. I’m impressed by the details that you have on this web site. It reveals how nicely you perceive this subject. Bookmarked this web page, will come back for extra articles. You, my friend, ROCK! I found just the information I already searched all over the place and simply couldn’t come across. What a great site.
2017-08-24
I think other website proprietors should take this site as a model, very clean and magnificent user-friendly style and design, as well as the content. You’re an expert on this topic!
2018-01-02
It is in point of fact a nice and helpful piece of information.
2018-01-17
REALLY GOOD! i like it so much<3 Thanks for the Good Artickle Sir.
2018-05-12
After I read and try to understand this article and finally amazing.
we are all grateful for the existence of this article can add even more insight for us all
thank you
2018-05-23
interesting articles and this is my first reading a very interesting article thanks for this article that fits with the theme news.
2018-06-12
thanks for this article that fits with the theme news.
2018-06-14
I like this artickle thanks you!!
2018-08-04
You Article Very Very nice…
I like It your Posting…
2018-08-09
After I read and try to understand this article and finally amazing are all grateful for the existence of this article can add even more insight for us all
thank you.
2018-08-20
the article you create is very interesting, I really like to read it