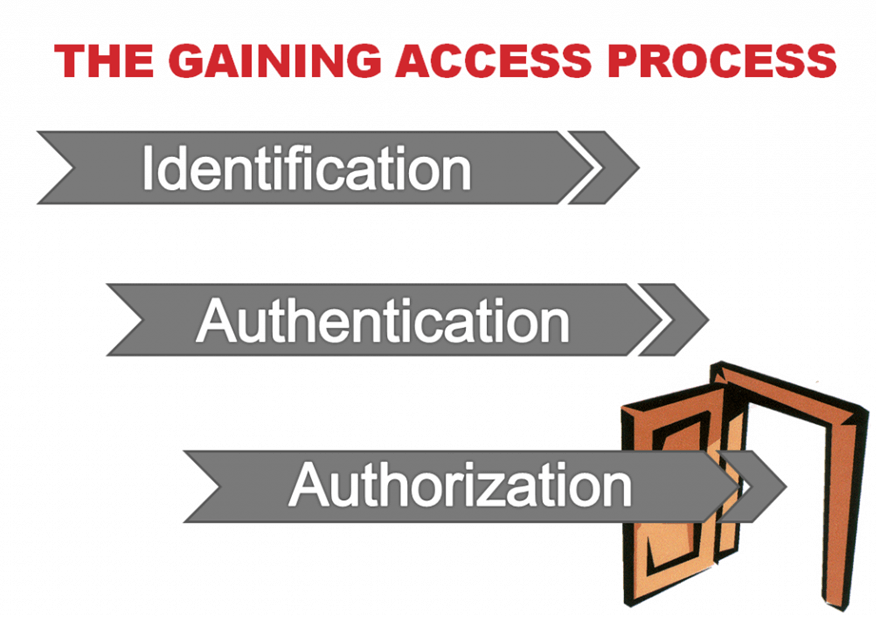
Identification, authentication, and authorization. We all face these three concepts every day, but not everyone knows the difference. Since these terms are essential in data protection, they deserve to be explained better.
To begin, let’s take an example from everyday life. It will help you to understand the difference between authentication and identification in general.
A new employee comes to work for the first time. At the entrance, he introduces himself to a security guard and says that he is a new manager. Thus, he identifies himself – tells who he is.
The security guard does not believe the words he says. He demands to provide evidence that this person is a new manager and has the right to enter the office. To solve the problem, the employee has to show his pass with the photo. And the security guard should compare it with his list of registered employees. The employee confirms his authenticity – this is authentication.
Finally, a forbidden door opens, and the guard lets the employee in. Once the employee receives the permission to enter the office the authorization happens.
In the virtual world, everything is almost the same as in the real. Only the names of the “characters” are changing. The security guard is a server that controls the access to the website. And the manager who came to work – a user who wants to log in.
It should be added that the security guards will repeat the procedure every day. Even when all the security guards know the manager by his look and name. They just do their job, like the server does.
All three concepts – identification, authentication, and authorization – are the stages of one process that controls users’ access to their accounts.
To perform any action on a website, the user must “introduce himself” to the system. User’s identification means presenting grounds for the entry to the site or service. As a rule, your username or email address provided during registration serve as identificators. If the server finds in its database the data coinciding with that entered by the user, the user’s identification is successful.
Login is a perfect thing. But where is the guarantee that it was entered by the person registered on the site? To finally verify the user’s identity, the system typically authenticates the user.
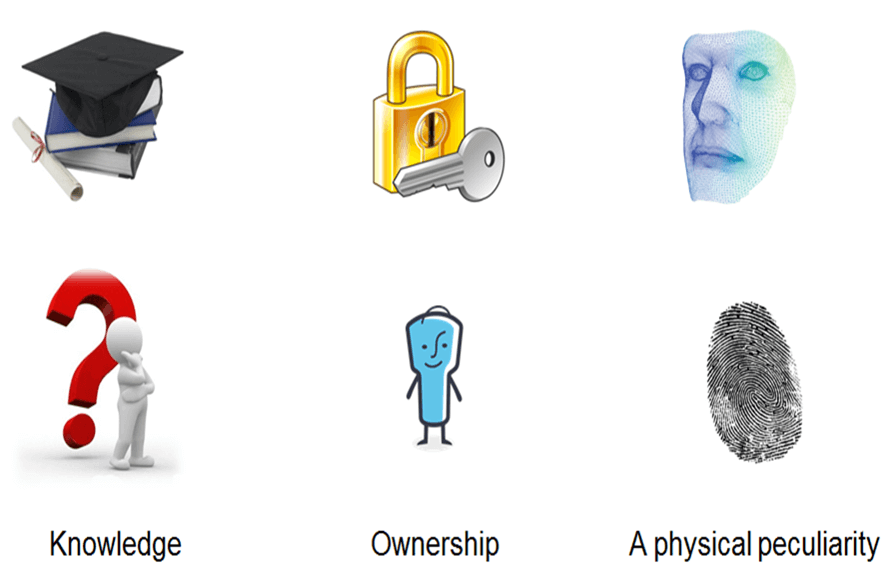
Now, more and more often the two-factor authentication is used. A usual static password serves as the first factor. The second factor may be different depending on the types of authentication methods used in this or that case:
- one-time password or PIN-code;
- magnetic stripe cards, smart cards, certificates with a digital signature;
- biometric factors: voice, retina, fingerprints, etc.
Despite the rapid development of biometric authentication methods, they are not enough reliable when used remotely. It is not always possible to guarantee the correct operation of devices and applications which perform retina or fingerprints scanning. You cannot be 100% sure whether the mould of the hand or fake user’s picture is used during verification. So this method can be considered valid only if authentication is directly controlled. For example, biometrics is quite efficient when the employee enters the office.
Under the conditions when the verifier and the verified are remote, as it happens on the Internet, the 2-factor authentication method using one-time passwords works much better. There are various authentication means and you can always choose the most convenient for each case. This may be authentication via text messages, one-time passwords generated by a hardware token or a special application on a smartphone. The choice is by the user.
Two-way authentication can be one-sided when the user proves his authenticity to the system, or bilateral when the server and the user mutually confirm their authenticity through “challenge-response” algorithm. This 2FA algorithm is used in Protectimus Ultra token and allows, among other things, to cut the risk of entering the phishing sites.
The last phase of the user’s entry is called authorization. Depending on whether identification and authentication were successful, the server either allows or does not allow the user to perform certain actions on the website.
The difference between the terms “authorization” and “authentication” is quite significant. You can often hear or read on the Internet the term “two-factor authorization”, but it is not correct. User’s authorization is the system’s final answer to the question, “Can this user get access to this or that information or function?” And because of its uniqueness, the authorization cannot be two-factor.
Yet, in order not to bring unnecessary confusion, this distinction is not usually emphasized. The two concepts are often used interchangeably.
A clear understanding of what the identification, authentication, and authorization are will allow you to use the functions they provide correctly. The latter will be beneficial for the safety of the information you store on the Internet.
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


2016-02-09
Cool http://www.protectimus.com always done then you need to take the article, once even in your personal life helped!
Develop and with the last Christmas to you all!
2017-04-15
Great work! That is the type of info that is meant to be shared across the internet.
Shame on the search engines for not positioning this publish higher!
2017-06-29
Great blog! Is your theme custom made or did you download it from somewhere?
A theme like yours with a few simple adjustments would really make my blog shine.
Please let me know where you got your design. With thanks
2017-07-10
Hi Willian, thank you for asking. We downloaded a ready-made theme called Nexus and customized it. Hope this info will help you in building your own blog.
2017-07-08
You really make it seem so easy with your presentation but I find this matter to be actually something which I think I would never understand. It seems too complex and extremely broad for me.
I am looking forward to your next post, I will try to get the hang of it!
2017-07-13
Pretty! This has been an extremely wonderful post. Many thanks for providing this information.
2017-07-13
Informative article, totally what I wanted to find.
2017-07-20
Gгeetings! Veгy helpful advice within this post! It is the little changes that produce the most significant changes. Thanks for sharing!
2017-08-09
It’s a remarkable post for all the web visitors; they will get advantage from it. I am sure.
2017-08-13
Ηi there! I just wanted to ask if you ever have any trouble with hackers? My last blog (wordprеss) was hacked and I ended up losing months of hard work due to no datɑ backup. Do you haᴠе any methods to stop hackers?
2017-08-24
Hey! Someone in my Facebook group shared this website with us so I came to check it out. I’m definitely enjoying the information. I’m book-marking and will be tweeting this to my followers! Excellent blog and brilliant design and style.
2017-08-28
I just couldn’t leave your website before saying that I really enjoyed the useful information you offer to your visitors… Will be back soon to check up on new posts
2017-09-12
Useful info. Lucky me I discovered your site accidentally,
and I am stunned why this accident did not happened earlier!
I bookmarked it.
2017-09-20
I feel this is among the such a lot important info for me. And i am glad reading your article. But wanna remark on few common things, The website style is perfect, the articles is in point of fact great : D. Good job, cheers
2020-02-27
Thank you so much I need to know this!