The Rothschild brothers, who grew rich making profits on the results of the Battle of Waterloo, used to say: “He who owns information owns the world”. The only thing to specify here is who the information belongs to: yourself or somebody else. All throughout its history, mankind has been involved in authentication technique development, from making call signals imitating birds’ sounds and manual ciphering to logging into a system via GPS.
During this entire period of time, the key focus has been the search for a simpler authentication method (one that does not involve compromising a system’s reliability). The problem is that sooner or later all new protection methods grow outdated and obsolete; besides, enterprising fraudsters are no fools – they may not want to own the world, but they do want to own at least some nude celebrity photos. And, as we know, what one man built up another man can break down. In modern times, the information battlefield is the Internet — it is the most convenient platform with the largest audience. Authentication methods are growing more complex and sophisticated, too: digest authentication (HTTPS protocol), OpenID, OpenAuth, etc.

Three factors to verify a user: what he knows; what he owns; and what nature gave him at birth.
At this stage in the society’s development, we have come to a paradoxical conclusion: to make authentication simple, we need to make it more complicated. That is, more complicated for a manufacturer; for a user, things remain as simple as ever. There are three factors that can be used to verify a user: what he knows (a password); what he owns (a card key); and what nature gave him at birth — his biometric data. The three parameters combined in one system — what could be simpler?
But, there is also the aspect of cost-effectiveness to be considered. In and of itself, a biometric detector is nothing new; for example, iPhone has the Touch ID technology. But when used together with Apple’s software, the fingerprint scanner will produce an error, which once even led to a recall of an update to iOS 8.0.1. On a user’s level, too, there are occasional problems with the use of a scanner. Besides, biometric technologies are relatively expensive. In terms of reliability, they leave much to be desired, too: a small cut can alter a fingerprint. Besides, once a criminal has a person’s biometric data in their possession, they can use the data for illegal purposes indefinitely — until the end of either the criminal’s or the poor discredited person’s natural life. But, the first two factors mentioned above are worth combining, both in terms of cost-effectiveness and protection level.
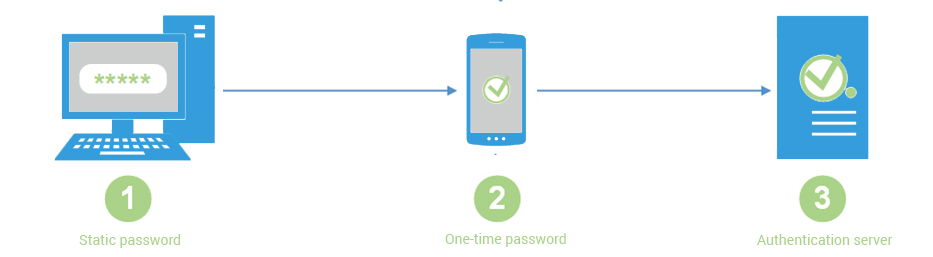
In two-factor authentication, two passwords are used — a reusable static password and a one-time password.
In two-factor authentication, two passwords are used — a reusable static password and a one-time password. In our case, here is what happens when the “One Time Password” technology is used. A user wants to get authenticated in the system and first enters his regular static password and then his OTP (One Time Password) shown on the screen of a special gadget called a token. The system transmits the data to the authentication server, which will use the same algorithm to generate a password and compare it to the password entered by the user; if the two passwords are identical, the system welcomes the user. The gadget costs less than ten dollars, and the service is under a dollar per month.
The conclusion is that two-factor authentication with the use of a token is the optimal solution from the point of view of protection, cost, and ease of use. All that a user is required to do is enter another password.
Those who are in search of reliable 2FA solutions, we recommend taking into consideration only products certified according to OATH standards. One of the most interesting and up-to-date companies providing such services is Protectimus. It deserves attention, thanks to an innovative approach to the implementation of already proven technologies, a wide range of services and tokens, and great respect for their customers.
Figuratively speaking, each authentication method used separately is a string that is easy to break. It is a much better idea to combine them and use a high-strength reliable rope.
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.


2017-01-13
You always do the right thing. God Bless you.
Thank you